Google’s new Gemini AI model means your future robot butler will still work even without Wi‑Fi
Google’s new Gemini Robotics On‑Device AI model lets robots run entirely offline The model can…











Tor Browser 15.0.2 is now available from the Tor Browser download page and also from our distribution directory. This version includes important security updates to Firefox. Send us your feedback If you find a bug or have a suggestion for how we could improve this release, please let us know. Full changelog The full changelog…
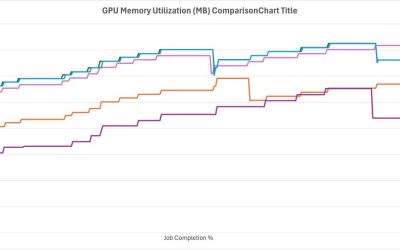
Optimizing generative AI applications relies on tailoring foundation models (FMs) using techniques such as prompt engineering, RAG, continued pre-training, and fine-tuning. Efficient fine-tuning is achieved by strategically managing hardware, training time, data volume, and model quality to reduce resource demands and maximize value. Spectrum is a new approach designed to pinpoint the most informative layers…

This post was written with Bharath Suresh and Mary Law from Snowflake. Agentic AI is a type of AI that functions autonomously, automating a broader range of tasks with minimal supervision. It combines traditional AI and generative AI capabilities to make decisions, perform tasks, and adapt to its environment without constant human intervention. These autonomous…

When people discuss the security implications of Unicode, International Domain Names (IDNs) are often highlighted as a risk. However, while visible and often talked about, IDNs are probably not what you should really worry about when it comes to Unicode. There are several issues that impact application security beyond confusing domain names. At first sight,…

A research team at the University of California, Riverside has found that routine exposure to microplastics — tiny pieces released from packaging, fabrics, and common consumer plastics — may speed up the formation of atherosclerosis, the artery-narrowing condition associated with heart attacks and strokes. The effect appeared only in male mice, offering new insight into…

By Reuters Published November 19, 2025 The BHV department store in Paris will not be allowed to host outdoor Christmas events this year, unlike in previous years, city authorities said, after they identified violations linked to the opening of Shein‘s first-ever physical shop within BHV. A view shows the Le BHV Marais department store, the…

By early June this year, an estimated 38 million tons of Sargassum drifted toward the coastlines of the Caribbean islands, the Gulf of Mexico, and northern South America, setting an unfortunate new record. During the summer, these floating mats of brown algae collect in large amounts on beaches where they decay and release an unpleasant…

By Reuters Published November 19, 2025 Associated British Foods‘ fashion chain Primark said on Wednesday it was eyeing growth in Germany again with a new approach after years of cutbacks and restructuring. Primark is known for its value fashion and lifestyle goods – REUTERS/ Shannon Stapleton The fashion chain opened its first new German store…

Chameleons have intrigued observers for thousands of years, largely because their eyes seem to roam independently in nearly every direction. After centuries of curiosity, modern imaging techniques have now uncovered the anatomical feature responsible for this extraordinary ability. Hidden behind each protruding eye are two long, spiraled optic nerves — a configuration not documented in…

By Bloomberg Published November 19, 2025 As the creative leads of many of the world’s great fashion houses begin to forge new identities on their runways, it’s a great time to question what consumers really want. Is quiet luxury over? Are loud labels back? Is bespoke the last real exclusivity? Is maximalism the mode of the day?…