Leveraging Generative AI to Reverse Engineer XLoader
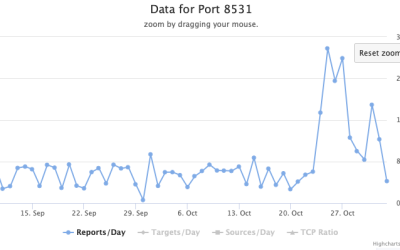
Research by: Alexey Bukhteyev Key takeaways XLoader remains one of the most challenging malware families to analyze. Its code decrypts only at runtime and is protected by multiple layers of encryption, each locked with a different key hidden somewhere else in the binary. Even sandboxes are no help: evasions block malicious branches, and the real…