A new home for Tor user documentation
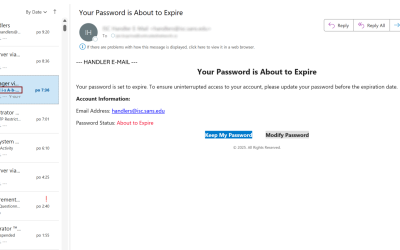
Privacy technology is only as powerful as people’s ability to use it. Every day, millions of people rely on Tor to protect their privacy and freedom online. But until now, finding answers to their questions meant navigating between different websites: one for the Tor Browser Manual, another for the Support portal. This fragmented experience made…