
ISC Stormcast For Monday, October 27th, 2025 https://isc.sans.edu/podcastdetail/9672
ISC Stormcast For Monday, October 27th, 2025 https://isc.sans.edu/podcastdetail/9672, (Mon, Oct 27th) Source link

ISC Stormcast For Monday, October 27th, 2025 https://isc.sans.edu/podcastdetail/9672, (Mon, Oct 27th) Source link
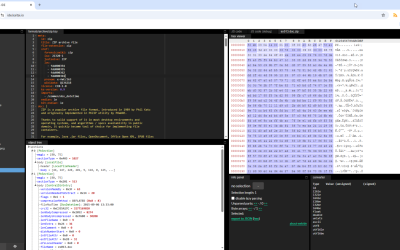
When I have a binary file to analyze, I often use tools like 010 Editor or format-bytes.py (a tool I develop). Sometimes I also use Kaitai Struct. What I did not know, is that Kaitai Struct also has a WebIDE, that allows you to parse all kinds of binary file formats in your browser. I…

Over the past two months, my outlook account has been receiving phishing email regarding cloud storage payments, mostly in French and some English with the usual warning such as the account is about to be locked, space is full, loss of data, refused payment, expired payment method, etc. Some of the emails have some typical…

ISC Stormcast For Friday, October 24th, 2025 https://isc.sans.edu/podcastdetail/9670, (Fri, Oct 24th) Source link

Research by: Antonis Terefos (@Tera0017) Key Points Check Point Research uncovered and analyzed the YouTube Ghost Network, a sophisticated and coordinated collection of malicious accounts operating on YouTube. These accounts systematically take advantage of YouTube’s features to promote malicious content, ultimately distributing malware while creating a false sense of trust among viewers. Our investigation identified and…

Infostealers landscape exploded in 2024 and they remain a top threat today. If Windows remains a nice target (read: Attackers’ favorite), I spotted an Infostealer targeting Android devices. This sounds logical that attackers pay attention to our beloved mobile devices because all our life is stored on them. The sample that I found (SHA256: 7576cdb835cd81ceb030f89fe5266649ed4a6201547c84da67144f407684a182)…

Oracle released its third quarterly edition of this year’s Critical Patch Update. The update received patches for 374 security vulnerabilities. Some of the vulnerabilities addressed in this update impact more than one product. These patches address vulnerabilities in various product families, including third-party components in Oracle products. In this quarterly Oracle Critical Patch Update, Oracle…

ISC Stormcast For Thursday, October 23rd, 2025 https://isc.sans.edu/podcastdetail/9668, (Thu, Oct 23rd) Source link

Starting yesterday, some of our honeypots received POST requests to “/cgi-bin/webctrl.cgi”, attempting to exploit an OS command injection vulnerability: POST /cgi-bin/webctrl.cgi Host: [honeypot ip]:80 User-Agent: Mozilla/5.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: es-MX,es;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 186 Origin: http://[honeypot ip]:80 Dnt: 1 Connection: close Referer: http://[honeypot ip]:80/cgi-bin/webctrl.cgi?action=pingconfig_page Cookie: userName=admin; state=login; passWord= Upgrade-Insecure-Requests: 1 …

ISC Stormcast For Wednesday, October 22nd, 2025 https://isc.sans.edu/podcastdetail/9666, (Wed, Oct 22nd) Source link