
ISC Stormcast For Thursday, August 7th, 2025 https://isc.sans.edu/podcastdetail/9560
ISC Stormcast For Thursday, August 7th, 2025 https://isc.sans.edu/podcastdetail/9560, (Thu, Aug 7th) Source link

ISC Stormcast For Thursday, August 7th, 2025 https://isc.sans.edu/podcastdetail/9560, (Thu, Aug 7th) Source link
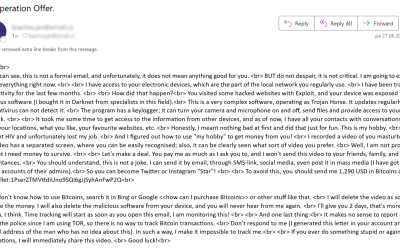
Sextortion e-mails have been with us for quite a while, and these days, most security professionals tend to think of them more in terms of an “e-mail background noise” rather than as if they posed any serious threat. Given that their existence is reasonably well-known even among general public, this viewpoint would seem to be…

ISC Stormcast For Wednesday, August 6th, 2025 https://isc.sans.edu/podcastdetail/9558, (Wed, Aug 6th) Source link

Arti is our ongoing project to create a next-generation Tor client in Rust. We’re happy to announce the latest release, Arti 1.4.6. This release of Arti has some improvements for Onion Service (Hidden Service) operators. There’s better resistance to denial-of-service (Proposal 362) and an experimental new utility for migration of Hidden Service identity key from…

By: Andrey Charikov, Roman Zaikin & Oded Vanunu Background Cursor is a developer-focused AI IDE that combines local code editing with large language model (LLM) integrations. Due to its flexibility and deep LLM integration, Cursor is increasingly adopted by startups, research teams, and individual developers looking to integrate AI tooling directly into their development workflow….
About 10 days ago exploits for Microsoft SharePoint (CVE-2025-53770, CVE-2025-53771) started being publicly abused – we wrote about that at here and here . The original SharePoint vulnerability is a deserialization vulnerability that allowed an attacker to execute arbitrary commands – while these could be literally anything, majority of exploits that we analyzed resulted in…

ISC Stormcast For Tuesday, August 5th, 2025 https://isc.sans.edu/podcastdetail/9556, (Tue, Aug 5th) Source link
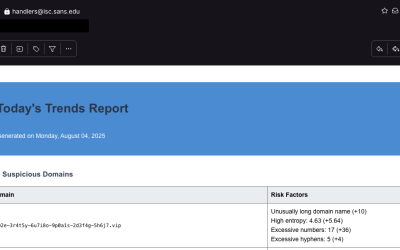
I implemented a new report today, the “Daily Trends” report. It summarizes noteworthy data received from our honeypot. As with everything, it will improve if you provide feedback 🙂 There are two ways to receive the report: E-Mail: Sign up at https://isc.sans.edu/notify.html JSON/HTTP: You may also just download the raw JSON data for…
Cyber threats are increasing in both volume and sophistication, while the enterprise attack surface continues to expand. This puts immense pressure on security teams, who are already overwhelmed by tool sprawl and a flood of disconnected findings—often lacking the context needed to prioritize based on business impact. To make matters worse, most security tools remain…
Agentic AI revolutionizes how enterprise organizations leverage artificial intelligence by introducing systems designed to function as autonomous agents capable of planning, decision-making, and executing complex workflows with minimal human oversight. Unlike traditional AI, which often performs isolated, reactive tasks, agentic AI brings contextual awareness, multi-step reasoning, and goal-driven behavior to enterprise processes. With the introduction…