
ISC Stormcast For Tuesday, July 29th, 2025 https://isc.sans.edu/podcastdetail/9546 – SANS Internet Storm Center
ISC Stormcast For Tuesday, July 29th, 2025 https://isc.sans.edu/podcastdetail/9546, (Tue, Jul 29th) Source link

ISC Stormcast For Tuesday, July 29th, 2025 https://isc.sans.edu/podcastdetail/9546, (Tue, Jul 29th) Source link

# Exploit Title: Adobe ColdFusion 2023.6 – Remote File Read # Exploit Author: @İbrahimsql # Exploit Author’s github: https://github.com/ibrahmsql # Description: ColdFusion 2023 (LUcee) – Remote Code Execution # CVE: CVE-2024-20767 # Vendor Homepage: https://www.adobe.com/ # Requirements: requests>=2.25.0, urllib3>=1.26.0 # Usage: python3 CVE-2024-20767.py -u http://target.com -f /etc/passwd #!/usr/bin/env python3 # -*- coding: utf-8 -*- …

# Exploit Title: XWiki 14 – SQL Injection via getdeleteddocuments.vm # Google Dork: N/A # Date: 28 July 2025 # Exploit Author: Byte Reaper # LinkedIn: N/A # Vendor Homepage: https://www.xwiki.org # Software Link: https://www.xwiki.org # Version: XWiki Platform ≤ 14.x # Tested on: XWiki Platform ≤ 14.x # CVE: CVE-2025-32429 ## Vulnerability Description …

# Exploit Title: Invision Community <= 4.7.20 (calendar/view.php) – SQL Injection # Google Dork: N/A # Date: 23 July 2025 # Exploit Author: Egidio Romano # LinkedIn: N/A # Vendor Homepage: https://invisioncommunity.com # Software Link: https://invisioncommunity.com # Version: Certain 4.x versions before 4.7.21 # Tested on: Invision Community <= 4.7.20 # CVE: CVE-2025-48932 …

# Exploit Title: Linux PAM Environment – Variable Injection Local Privilege Escalation # Exploit Author: @İbrahimsql # Exploit Author’s github: https://github.com/ibrahmsql # Description: PAM pam_env.so module allows environment variable injection via ~/.pam_environment # leading to privilege escalation through SystemD session manipulation # CVE: CVE-2025-6018, CVE-2025-6019 # Vendor Homepage: https://github.com/linux-pam/linux-pam # Software Link: https://github.com/linux-pam/linux-pam/releases # Version:…

As enterprises accelerate AI adoption, large language models (LLMs) hosted on public cloud platforms are quickly becoming the norm due to their simplified access and pricing model. Cloud-native services like AWS Bedrock, Azure AI Foundry, and Google Vertex AI offer powerful, pay-as-you-go access to Foundational AI Models and enterprise-grade pre-trained marketplace LLMs with just a…

# Exploit Title: Mezzanine CMS 6.1.0 Stored Cross Site Scripting (XSS) via component /blog/blogpost/add # Date: 23/07/2025 # Exploit Author: Kevin Dicks # Vendor Homepage: https://github.com/stephenmcd/mezzanine # Software Link: https://github.com/stephenmcd/mezzanine # Version: 6.1.0 # Category: Web Application # Tested on: Ubuntu Server 20.04.6 LTS (Focal Fossa), Firefox browser version 136.0 (64-bit) # CVE : CVE-2025-50481 …
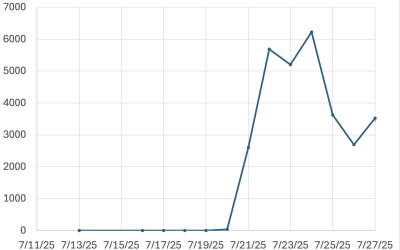
Last week, newly exploited SharePoint vulnerabilities took a lot of our attention. It is fair to assume that last Monday (July 21st), all exposed vulnerable SharePoint installs were exploited. Of course, there is nothing to prevent multiple exploitation of the same instance, and a lot of that certainly happened. But why exploit it yourself if…

# Exploit Title: Xlight FTP 1.1 – Denial Of Service (DOS) # Google Dork: N/A # Date: 22 July 2025 # Exploit Author: Fernando Mengali # LinkedIn: https://www.linkedin.com/in/fernando-mengali/ # Vendor Homepage: https://www.xlightftpd.com # Software Link: N/A # Version: 1.1 # Tested on: Windows XP # CVE: CVE-2024-0737 $sis=”$^O”; if ($sis eq “windows”){ …

For the latest discoveries in cyber research for the week of 28th July, please download our Threat Intelligence Bulletin. TOP ATTACKS AND BREACHES The US Energy Department, including its National Nuclear Security Administration (NNSA), was reportedly breached as part of a Microsoft SharePoint vulnerability exploit. The breach was linked to a broader espionage campaign, that…