
Setchu stages first runway show in Milan menswear
Six months ago, when Satoshi Kuwata made his global runway show debut with Setchu in…











Overview A recently disclosed pair of vulnerabilities affecting Fortinet devices—CVE-2025-59718 and CVE-2025-59719—are drawing urgent attention after confirmation of their active exploitation in the wild. The vulnerabilities carry a critical CVSSv3 score and allow an unauthenticated remote attacker to bypass authentication using a crafted SAML message, ultimately gaining administrative access to the device. Current information indicates…

Following disclosure of the React2Shell vulnerability (CVE-2025-55182), a maximum-severity Remote Code Execution (RCE) in React Server Components (RSC) a.k.a. the Flight protocol, security teams are assessing exposure and validating fixes. React and ecosystem vendors have released patches; exploitation in the wild has been reported, so rapid validation matters. What is React2Shell? React2Shell is an unauthenticated…

A user can conduct machine learning (ML) data experiments in data environments, such as Snowflake, using the Snowpark library. However, tracking these experiments across diverse environments can be challenging due to the difficulty in maintaining a central repository to monitor experiment metadata, parameters, hyperparameters, models, results, and other pertinent information. In this post, we demonstrate…

Earlier this year, I was asked about the connection between digital rights to human rights. I responded with my own questions. Today, I’m asking you those same questions: When was the last time you learned about a police or military force harming a community? Where did you learn that information? When was the last time…

I have already talked about various React2Shell exploit attempts we have observed in the last weeks. But new varieties of the exploit are popping up, and the most recent one is using this particular version of the exploit: POST /app HTTP/1.1 Host: 81.187.66.58 Content-Type: multipart/form-data; boundary=—-WebKitFormBoundary7MA4YWxkTrZu0gW Next-Action: 0 Rsc-Action: 0 Content-Length: 388 User-Agent: Mozilla/5.0…

Executive Summary ShadyPanda has exploited trusted browser extensions to compromise millions of users, illustrating how legitimate software can unexpectedly become harmful. Qualys TruRisk Eliminate empowers organizations to identify risky behaviors, prioritize real threats, and eliminate malicious components before attackers exploit them. How Browser Extensions Have Become a New Blind Spot Browser extensions are part of everyday…

Building custom foundation models requires coordinating multiple assets across the development lifecycle such as data assets, compute infrastructure, model architecture and frameworks, lineage, and production deployments. Data scientists create and refine training datasets, develop custom evaluators to assess model quality and safety, and iterate through fine-tuning configurations to optimize performance. As these workflows scale across…
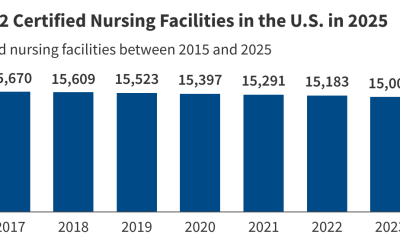
The 2025 reconciliation law could have major implications for nearly 15,000 federally certified nursing facilities and the more than 1.2 million people living in them. Nursing facilities provide medical and personal care services for older adults and people with disabilities. In 2023, Medicaid paid for 44% of long-term institutional care costs; 37% of long-term institutional care…

Philippa RoxbyHealth reporter Getty Images Young men are behind the growing popularity of nicotine pouches in Great Britain, a study suggests. Around 7.5% of 16 to 24-year-old-men are using the small sachets that fit under the top lip, compared with 1.9% use among young women and 1% among adults overall. Most pouch users – estimated…

Today, we’re expanding the Gemini 3 model family with the release of Gemini 3 Flash, which offers frontier intelligence built for speed at a fraction of the cost. With this release, we’re making Gemini 3’s next-generation intelligence accessible to everyone across Google products. Last month, we kicked off Gemini 3 with Gemini 3 Pro and…