NYT Connections hints and answers for Wednesday, July 9 (game #759)
Looking for a different day? A new NYT Connections puzzle appears at midnight each day…











I was struck by her pessimism, which she told me was shared by friends from California to Georgia to New Hampshire. In an already fragile world, one increasingly beset by climate change and the breakdown of the international order, AI looms in the background, threatening young people’s ability to secure a prosperous future. It’s an…

Move over gym rats. Bumble bees are now the true masters of macros. In the first long-term, community-level field study of wild bumble bee nutrition, a team of ecologists led by Northwestern University and the Chicago Botanic Garden discovered that wild bees aren’t just flitting from flower to flower, collecting pollen at random. Instead, they…

Sharks can famously replace their teeth, with new ones always growing as they’re using up the current set. As sharks rely on their teeth to catch prey, this is vital to the survival of one of the oceans’ top predators. But the ability to regrow teeth might not be enough to ensure they can withstand…

Researchers test a chest compression machine on a dummy in an aeroplane CNES Microgravity makes it tricky to do simple tasks like eating, using the toilet and showering, so it is no wonder that performing CPR on someone whose heart stops beating in space is an extremely demanding procedure. But a mechanical device could do…
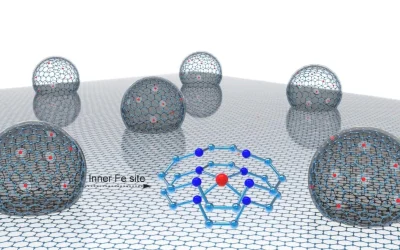
Proton exchange membrane fuel cells (PEMFCs), often referred to as “hydrogen power banks,” are clean energy devices that generate electricity from hydrogen and oxygen with only water as a byproduct. Characterized by high efficiency, rapid start-up, and zero emissions, they hold great promise in transportation, portable electronics, and stationary power generation. Unfortunately, PEMFCs currently rely…
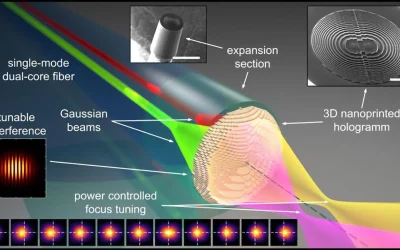
Precise control of light focus is essential for applications ranging from microscopy and laser surgery to quantum optics and telecommunications. However, existing solutions often rely on large, complex external components that limit integration and speed. In a new study published in Light: Science & Applications, researchers led by Professor Markus A. Schmidt from the Leibniz…
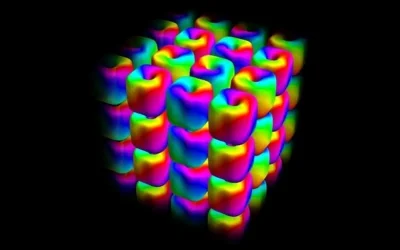
An internationally joint research group between Singapore and Japan has unveiled a blueprint for arranging exotic, knot-like patterns of light into repeatable crystals that extend across both space and time. The work lays out how to build and control “hopfion” lattices using structured beams at two different colors, pointing to future systems for dense, robust…

Some patients who have been red flagged for breast cancer assessments are waiting up to seven weeks to be seen in Northern Ireland. The target set by Northern Ireland’s devolved Department of Health – which oversees five health and social care trusts – is 14 days. BBC News NI understands that several breast cancer consultants…

In most attack scenarios, attackers have to perform a crucial operation: to load a shellcode in memory and execute it. This is often performed in a three-step process: Some memory must be allocated and flagged as “executable” with VirtualAlloc() (and sometimes combined with VirtualProtect()) The shellcode (often deobfuscated) is copied into this newly…

Maddie Molloy BBC Climate & Science Bidyut Kalita This image titled “Special Delivery” was highly commended in the Behaviour: Invertebrates category. At first glance, the potter wasp appears to be riding a broomstick. But this industrious insect isn’t flying back to stir its witch’s cauldron, or playing Quidditch. It’s carrying a caterpillar – prey to…