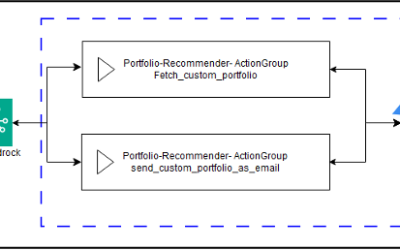
Chinese tech workers are smuggling AI data on hard drives while America chokes chip access with sanctions
Flying petabytes of AI data is China’s latest workaround for strict U.S. chip controls Physically smuggling hard drives now bypasses surveillance and digital firewalls across multiple jurisdictions GPU-rich Malaysian data centers are becoming ground zero for offshore Chinese AI training As the United States continues to tighten export restrictions on advanced AI chips, such as…