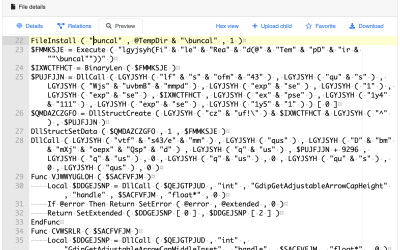
AutoIT3 Compiled Scripts Dropping Shellcodes
AutoIT3[1] is a powerful language that helps to built nice applications for Windows environments, mainly to automate tasks. If it looks pretty old, the latest version was released last September and it remains popular amongst developers, for the good… or the bad! Malware written in AutoIt3 has existed since the late 2000s, when attackers realized…







![Nation-State Attack or Compromised Government? [Guest Diary]](https://informernow.online/wp-content/uploads/2025/12/Jackie_Nguyen_pic1-400x250.png)

