For the latest discoveries in cyber research for the week of 14th July, please download our Threat Intelligence Bulletin.
TOP ATTACKS AND BREACHES
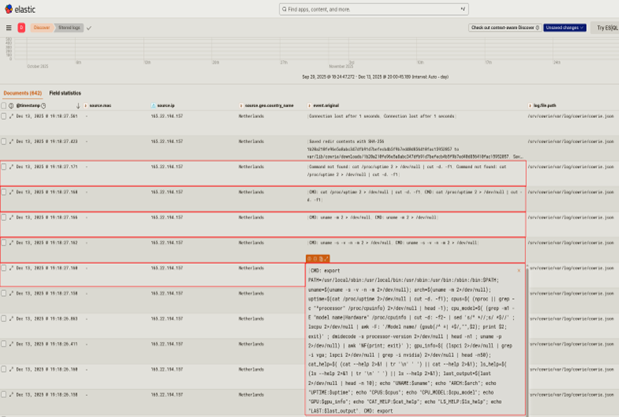
- McDonald’s has suffered a data breach that resulted in the exposure of chat transcripts, session tokens, and personal data from more than 64 million job applications submitted through its AI powered McHire chatbot platform. Data leaked included applicants’ names, email addresses, phone numbers, home addresses, availability, and personality test results, made accessible due to an insecure direct object reference (IDOR) vulnerability and admin accounts protected by weak default credentials.
- RocketGenius, the developer of WordPress plugin Gravity Forms, has experienced a cyber-attack that resulted in the compromise of plugin versions 2.9.11.1 and 2.9.12 available for manual download and composer install between July 10 and 11. The attack enabled remote code execution, extensive exfiltration of website metadata—including URLs, admin paths, installed themes, plugin and server versions—and the creation of a rogue admin account granting attackers complete control over affected websites, impacting potentially one million sites.
- Bitcoin Depot, a major Bitcoin ATM operator in the US, has suffered a data breach that resulted in the exposure of sensitive personal information belonging to nearly 27,000 customers, including full names, phone numbers, driver’s license numbers, addresses, dates of birth, and email addresses.
- Albemarle County in Virgina, United States, was hit by a ransomware attack that resulted in significant phone and technology outages, and the potential exposure of sensitive data belonging to local government and public-school employees, including driver’s license numbers, Social Security numbers, passport numbers, military IDs, and more. Some of the county’s 112,000 residents may have also had their names, addresses, and Social Security numbers compromised.
- GMX, a decentralized crypto exchange platform, has confirmed a cyber-attack that resulted in the theft of more than $40 million worth of cryptocurrency assets from its platform. The incident impacted user funds, with about $43 million in digital assets—including Ethereum, USDC, and DAI—being stolen and laundered by the hacker, affecting the platform’s more than 700,000 users.
- Nippon Steel Solutions, Japan’s largest steelmaker, has suffered a data breach after attackers exploited a zero-day vulnerability in its network equipment, resulting in unauthorized access to sensitive information. The breach has potentially exposed personal data of customers, partners, and employees.
- Ameos Group, a major Swiss hospital group, has experienced a cyber-attack that resulted in significant disruptions to its hospital operations across multiple locations. Critical IT systems were rendered inoperable, affecting both inpatient and outpatient care, as well as internal communication and documentation.
VULNERABILITIES AND PATCHES
- Microsoft has published July’s Patch Tuesday, addressing 137 vulnerabilities across Microsoft products, including a publicly disclosed zero-day (CVE-2025-49719) in Microsoft SQL Server that allows remote, unauthenticated information disclosure due to improper input validation. Critical remote code execution vulnerabilities in Microsoft Office—triggered by malicious documents or preview pane viewing—and additional RCE flaws in Microsoft SharePoint (CVE-2025-49704) are also resolved.
- Details have been disclosed on a pre-authenticated SQL injection vulnerability (CVE-2025-25257, CVSS 9.8) in Fortinet FortiWeb, where exploitation can lead to remote code execution on unpatched systems. Attackers can inject arbitrary SQL via the Authorization header in HTTP requests, allowing unauthorized file creation and code execution through manipulated Python files. Exploits and technical details have been released publicly, greatly increasing the risk of compromise.
Check Point IPS provides protection against this threat (Fortinet FortiWeb SQL Injection CVE-2025-25257)
- A technical analysis of the PerfektBlue vulnerability chain revealed four chained flaws (CVE-2024-45431 through CVE-2024-45434) in the Blue SDK Bluetooth stack used by OpenSynergy. The vulnerabilities enable remote code execution in over 350 million vehicles from Mercedes-Benz, Volkswagen, Skoda, and possibly Ford, and more than 1 billion embedded devices spanning automotive, industrial, consumer, mobile, and medical sectors.
THREAT INTELLIGENCE REPORTS
- Check Point Research has released its June 2025 Malware Report highlighting AsyncRAT which was ranked number three among Top Malware. AsyncRAT was distributed via sophisticated multi-stage malware campaign exploiting expired Discord vanity invite links, leveraging trusted platforms such as GitHub, Bitbucket, and Discord for payload delivery and data exfiltration. The report also details additional malware families including FakeUpdates and Androxgh0st, affecting sectors such as education, healthcare, and government.
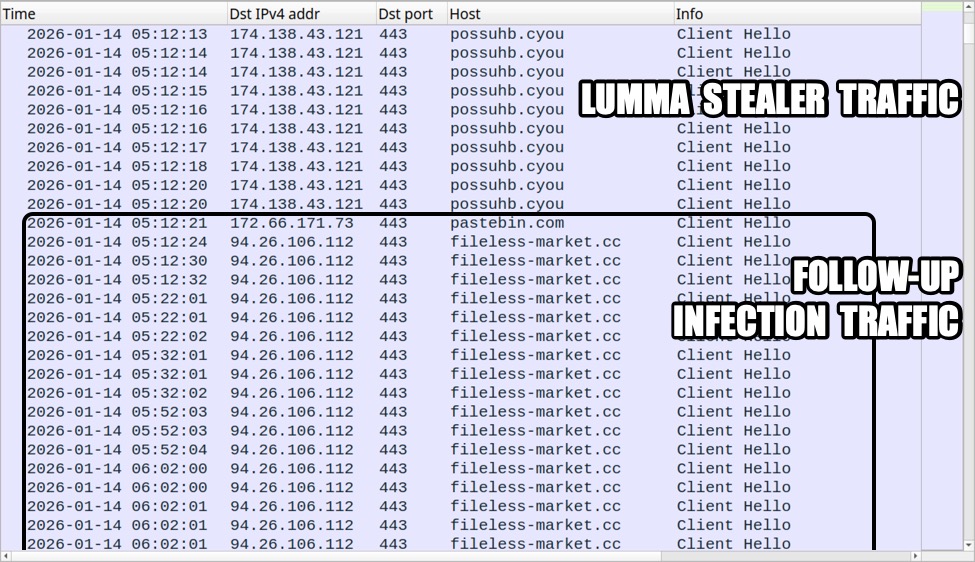
- Check Point Research has summarized key findings about the Scattered Spider threat group, which has recently targeted major airlines and diverse enterprises using sophisticated social engineering and phishing domain infrastructure. The group employs phishing sites that mimic corporate login portals (e.g., victimname-sso.com), MFA fatigue, vishing, SIM swapping, and uses both remote access tools and infostealers.
- Check Point has released findings revealing a 39% surge in weekly cyber-attacks targeting organizations in Latin America during the first half of 2025, averaging 2,716 weekly incidents compared to the global average of 1,955. Key threats include advanced malware such as RATs and botnets, while email was identified as the leading delivery vector.