
ISC Stormcast For Wednesday, July 9th, 2025 https://isc.sans.edu/podcastdetail/9518 – SANS Internet Storm Center
ISC Stormcast For Wednesday, July 9th, 2025 https://isc.sans.edu/podcastdetail/9518, (Wed, Jul 9th) Source link

ISC Stormcast For Wednesday, July 9th, 2025 https://isc.sans.edu/podcastdetail/9518, (Wed, Jul 9th) Source link

#!/usr/bin/env python3 “”” Exploit Title: Discourse 3.2.x – Anonymous Cache Poisoning Date: 2024-10-15 Exploit Author: ibrahimsql Github: : https://github.com/ibrahmsql Vendor Homepage: https://discourse.org Software Link: https://github.com/discourse/discourse Version: Discourse < latest (patched) Tested on: Discourse 3.1.x, 3.2.x CVE: CVE-2024-47773 CVSS: 7.1 (AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:L) Description: Discourse anonymous cache poisoning vulnerability allows attackers to poison the cache with responses…

# Titles: Microsoft Outlook – Remote Code Execution (RCE) # Author: nu11secur1ty # Date: 07/06/2025 # Vendor: Microsoft # Software: https://www.microsoft.com/en-us/microsoft-365/outlook/log-in # Reference: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-47176 > https://www.cloudflare.com/learning/security/what-is-remote-code-execution/ # CVE-2025-47176 ## Description This proof-of-concept (PoC) demonstrates the CVE-2025-47176 vulnerability simulation. It injects a crafted mail item into Outlook containing a malicious sync path that triggers an…

AMD: CVE-2024-36350 Transient Scheduler Attack in Store Queue CVE-2025-36350 No No – Less Likely Critical 5.6 4.9 AMD: CVE-2025-36357 Transient Scheduler Attack in L1 Data Queue CVE-2025-36357 No No – Less Likely …
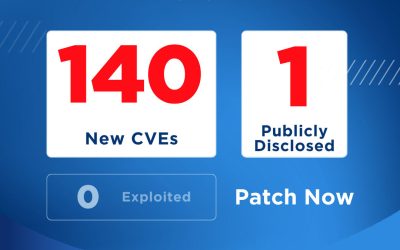
With cybersecurity threats continuing to evolve, Microsoft’s July 2025 Patch Tuesday highlights the need for consistent patching — this month’s release includes key fixes for actively exploited vulnerabilities. Here’s a quick breakdown of what you need to know. Microsoft Patch Tuesday for July 2025 In this month’s Patch Tuesday, the July 2025 edition, Microsoft addressed…

#!/bin/bash # Exploit Title: Microsoft Defender for Endpoint (MDE) – Elevation of Privilege # Date: 2025-05-27 # Exploit Author: Rich Mirch # Vendor Homepage: https://learn.microsoft.com/en-us/defender-endpoint/ # Software Link: https://learn.microsoft.com/en-us/defender-endpoint/microsoft-defender-endpoint-linux # Versions: # Vulnerable March-2025 Build: 101.25012.0000 30.125012.0000.0 # Vulnerable Feb-2025 Build: 101.24122.0008 20.124112.0008.0 # Vulnerable Feb-2025 Build: 101.24112.0003 30.124112.0003.0 # Vulnerable Jan-2025 Build: 101.24112.0001 30.124112.0001.0 …

Exploit Title: Sudo chroot 1.9.17 – Local Privilege Escalation Google Dork: not aplicable Date: Mon, 30 Jun 2025 Exploit Author: Stratascale Vendor Homepage:https://salsa.debian.org/sudo-team/sudo Software Link: Version: Sudo versions 1.9.14 to 1.9.17 inclusive Tested on: Kali Rolling 2025-7-3 CVE : CVE-2025-32463 *Version running today in Kali:* https://pkg.kali.org/news/640802/sudo-1916p2-2-imported-into-kali-rolling/ *Background* An attacker can leverage sudo’s…

Arti is our ongoing project to create a next-generation Tor client in Rust. We’re happy to announce the latest release, Arti 1.4.5. This release of Arti continues our development efforts towards supporting xon-based (proposal 324) flow control and multi-legged tunnels in Arti via our Conflux feature. In addition to the ongoing client feature efforts, the…

# Exploit Title: ScriptCase 9.12.006 (23) – Remote Command Execution (RCE) # Date: 04/07/2025 # Exploit Author: Alexandre ZANNI (noraj) & Alexandre DROULLÉ (cabir) # Vendor Homepage: https://www.scriptcase.net/ # Software Link: https://www.scriptcase.net/download/ # Version: 1.0.003-build-2 (Production Environment) / 9.12.006 (23) (ScriptCase) # Tested on: EndeavourOS # CVE : CVE-2025-47227, CVE-2025-47228 # Source: https://github.com/synacktiv/CVE-2025-47227_CVE-2025-47228 # Advisory:…

# Exploit Title: Stacks Mobile App Builder 5.2.3 – Authentication Bypass via Account Takeover # Date: October 25, 2024 # Exploit Author: stealthcopter # Vendor Homepage: https://stacksmarket.co/ # Software Link: https://wordpress.org/plugins/stacks-mobile-app-builder/ # Version: <= 5.2.3 # Tested on: Ubuntu 24.10/Docker # CVE: CVE-2024-50477 # References: # – https://github.com/stealthcopter/wordpress-hacking/blob/main/reports/stacks-mobile-app-builder-priv-esc/stacks-mobile-app-builder-priv-esc.md # – https://www.wordfence.com/threat-intel/vulnerabilities/wordpress-plugins/stacks-mobile-app-builder/stacks-mobile-app-builder-523-authentication-bypass-via-account-takeover 1. Navigate…