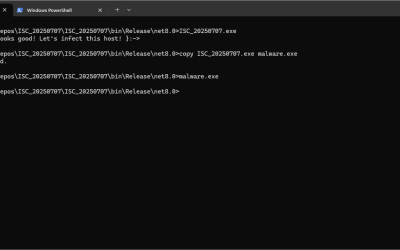
Sudo 1.9.17 Host Option – Elevation of Privilege
# Exploit Title: Sudo 1.9.17 Host Option – Elevation of Privilege # Date: 2025-06-30 # Exploit Author: Rich Mirch # Vendor Homepage: https://www.sudo.ws # Software Link: https://www.sudo.ws/dist/sudo-1.9.17.tar.gz # Version: Stable 1.9.0 – 1.9.17, Legacy 1.8.8 – 1.8.32 # Fixed in: 1.9.17p1 # Vendor Advisory: https://www.sudo.ws/security/advisories/host_any # Blog: https://www.stratascale.com/vulnerability-alert-CVE-2025-32462-sudo-host # Tested on: Ubuntu 24.04.1; Sudo 1.9.15p5,…