Older Java installations pose a significant security risk, particularly when developers install them in non-standard locations without any version control. These unmanaged installations often go undetected, silently expanding the organization’s attack surface and leaving critical vulnerabilities unpatched.
To reduce this risk, users should be able to identify all Java installations on a host and remove unapproved or outdated versions.
Challenges
Users commonly face the following key challenges when trying to reduce the risk associated with Java vulnerabilities:
Inventory Gaps
It’s extremely difficult to locate all installed Java instances – for a specific version of jdk/jre across distributed environments.
Vulnerability Detection Accuracy
Most tools lack accuracy in identifying the exact vulnerable Java installations on the host, especially when they reside in custom paths or are not properly registered.
Limited Response Capabilities
There is often no straightforward way to remove the vulnerable Java instances or flexibility to write custom mitigation or remediation signatures to remove a jdk/jre prior to the minimum safe version. Most vulnerability management tools do not offer out-of-the-box remediation capabilities for Java.
How Qualys Can Help
Qualys provides a complete solution from discovery to remediation to eliminate Java-related risk across your environment.
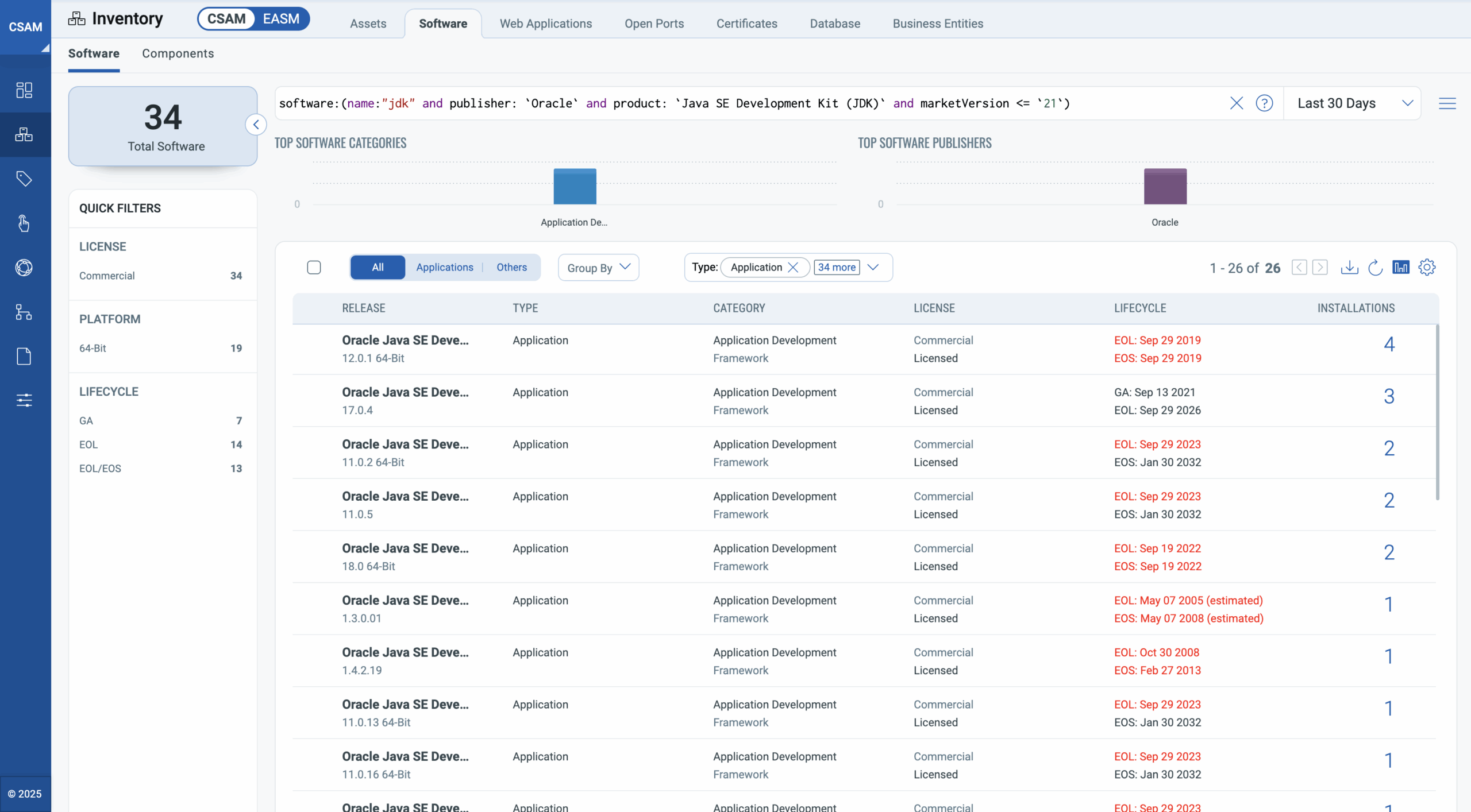
Inventory Java Instances Using Qualys CSAM
With Qualys Cyber Security Asset Management (CSAM), you can easily gain a comprehensive view of all installed Java instances, including granular, version-specific details.
Use a simple query like the one below to get a detailed inventory, along with End-of-Life (EOL) and End-of-Support (EOS) timelines. software:(name:”jdk” and publisher: `Oracle` and product: `Java SE Development Kit (JDK)` and marketVersion <= `21`)
This visibility empowers you to identify older, unapproved versions before they become a security threat.
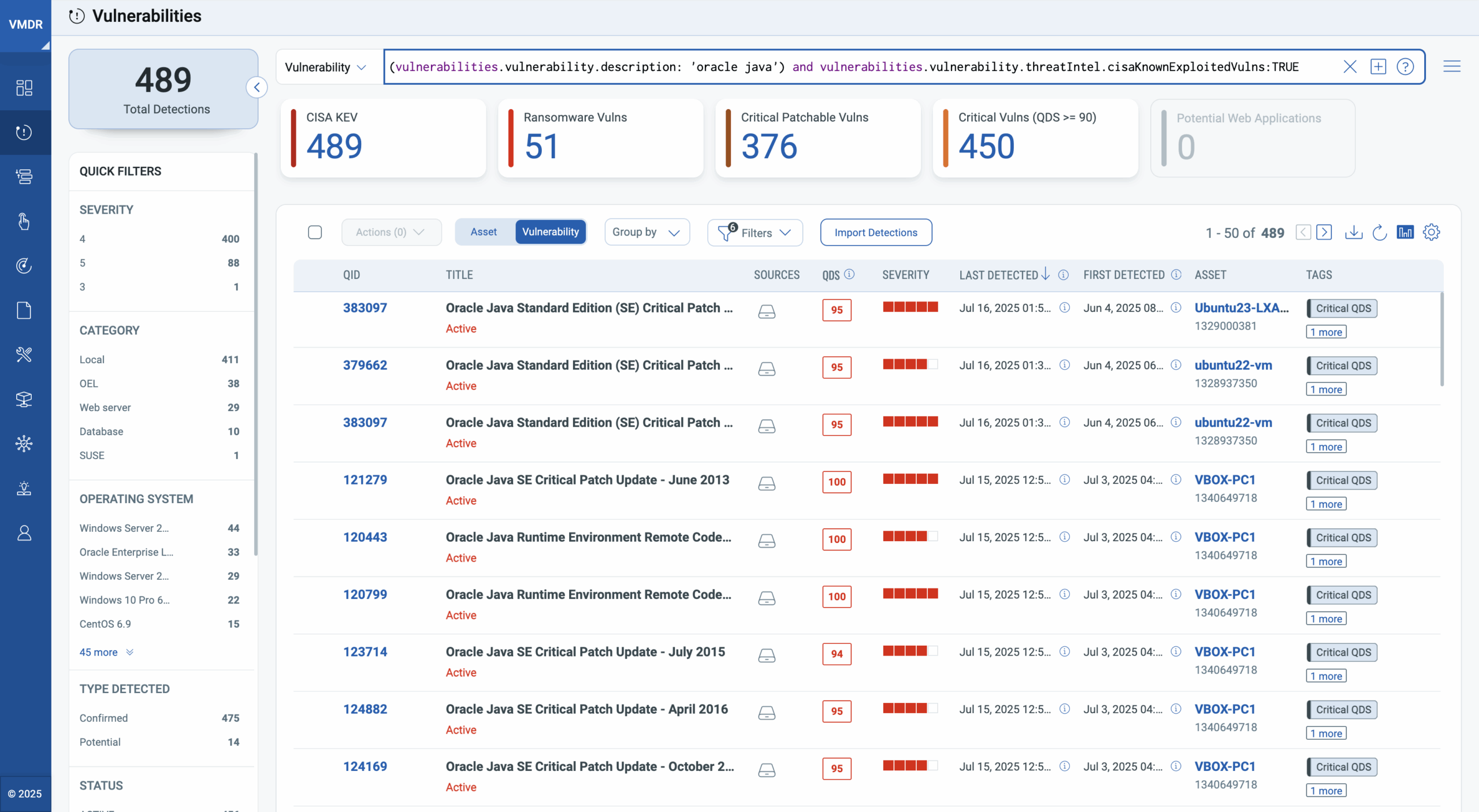
Discover Vulnerable Java Instances Using Qualys VMDR
To list down all the vulnerabilities caused by Oracle Java JDK/JRE, run the following VMDR query:
(vulnerabilities.vulnerability.description: ‘oracle java’)
You don’t need to immediately start remediation efforts for all such vulnerable detections. Prioritize and address the vulnerabilities that pose maximum risk to your organization. Start with CISA Known Exploited Vulnerabilities (KEV).
(vulnerabilities.vulnerability.description: ‘oracle java’) and (vulnerabilities.vulnerability.threatIntel.cisaKnownExploitedVulns:TRUE)
This will list all the critical vulnerabilities linked to older or unsupported Java versions.
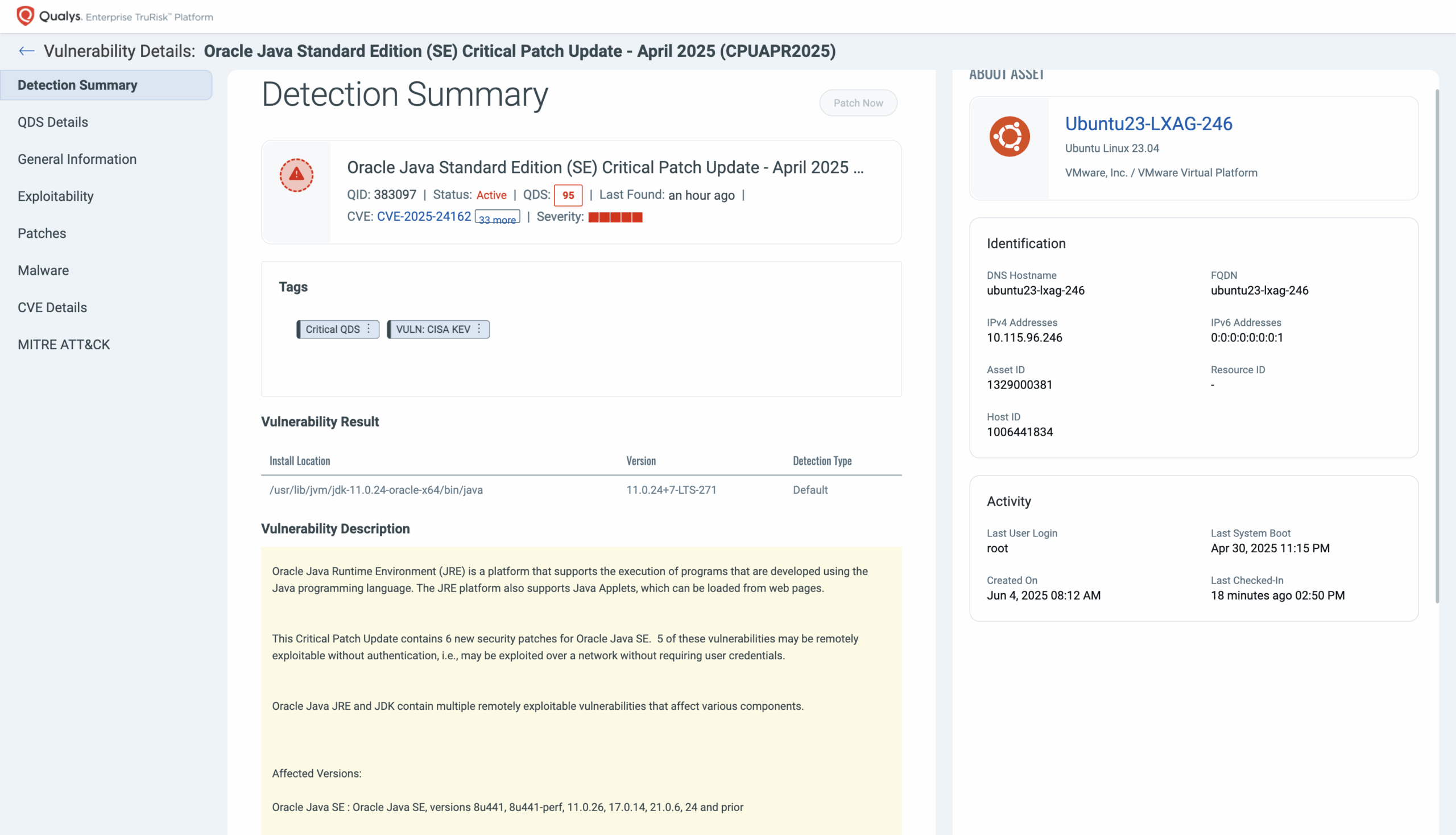
Each detection provides comprehensive details as follows:
With Qualys TruRisk™ Eliminate, you can take direct action on outdated or non-compliant Java versions and reduce the risk. It provides you complete flexibility to remove outdated Java versions based on your environment’s approved baseline.
Let’s consider a use case for your environment where:
Approved versions are:
- JDK 21 and above
- JRE 8 and above
Recommended action is to remove all other versions below this baseline.
Rationale: This helps eliminate risk from unsupported or unknown Java installations.
Qualys TruRisk™ Eliminate enables you to perform this action with ease and accuracy, ensuring risk reduction.
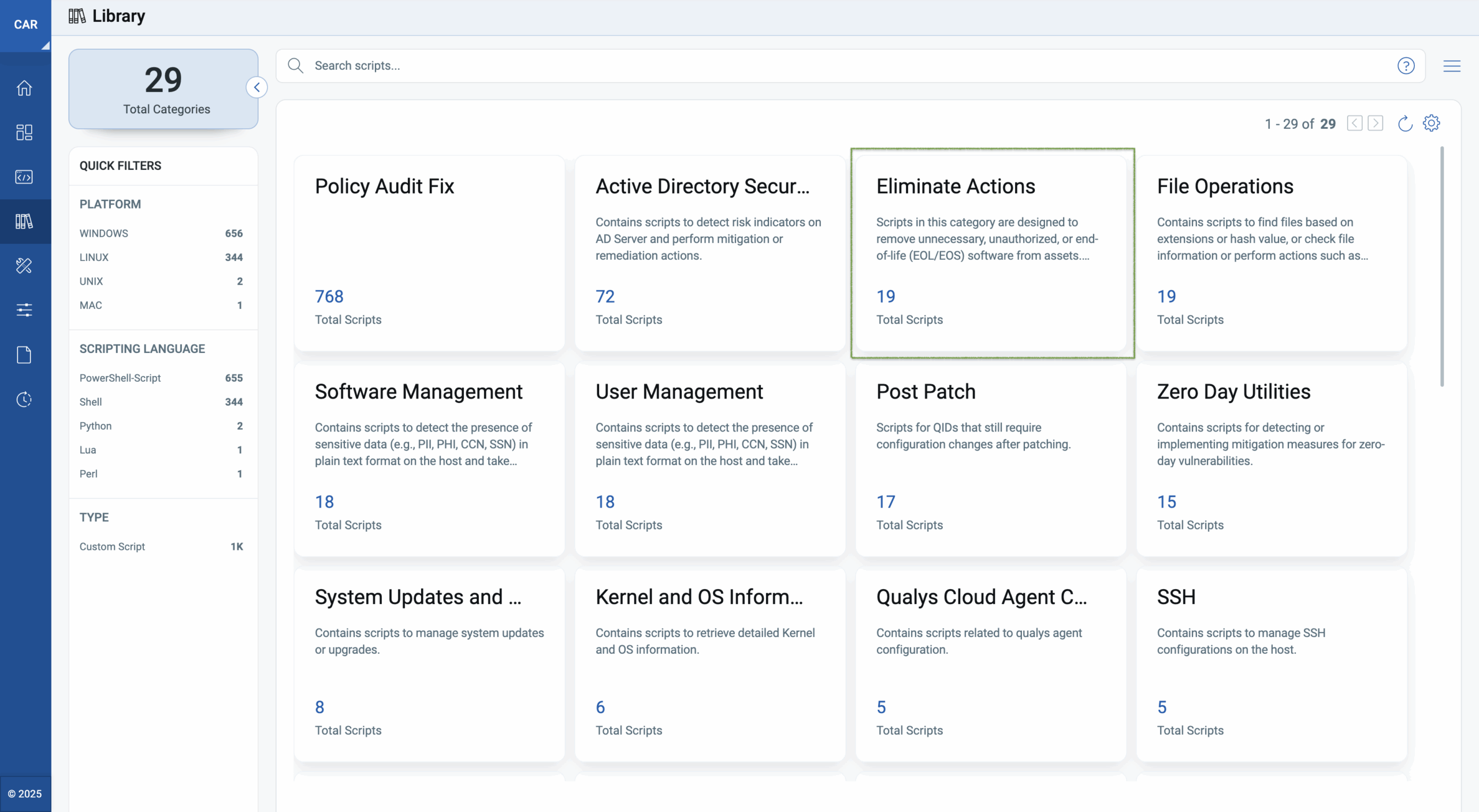
Remove Outdated Java Versions Using Qualys CAR
Qualys Custom Assessment and Remediation (CAR) is a core capability within TruRisk™ Eliminate that lets you execute custom remediation actions across your assets.
CAR offers a prebuilt script library, which comprises not just generic script templates, but also actual scripts based on real-world security use cases.
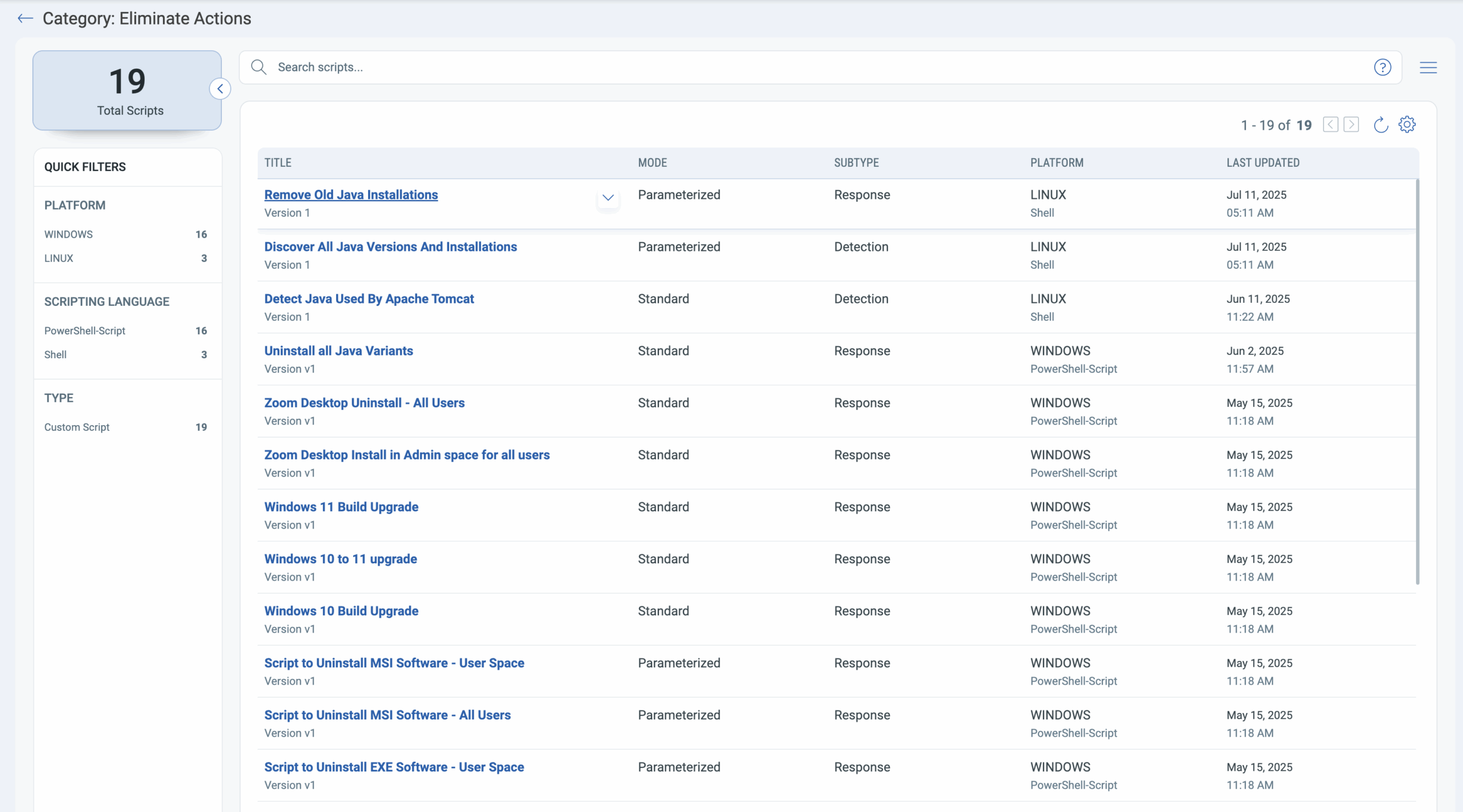
To tackle risk reduction use cases, we have introduced a NEW category in the CAR Library:
Step by Step Workflow
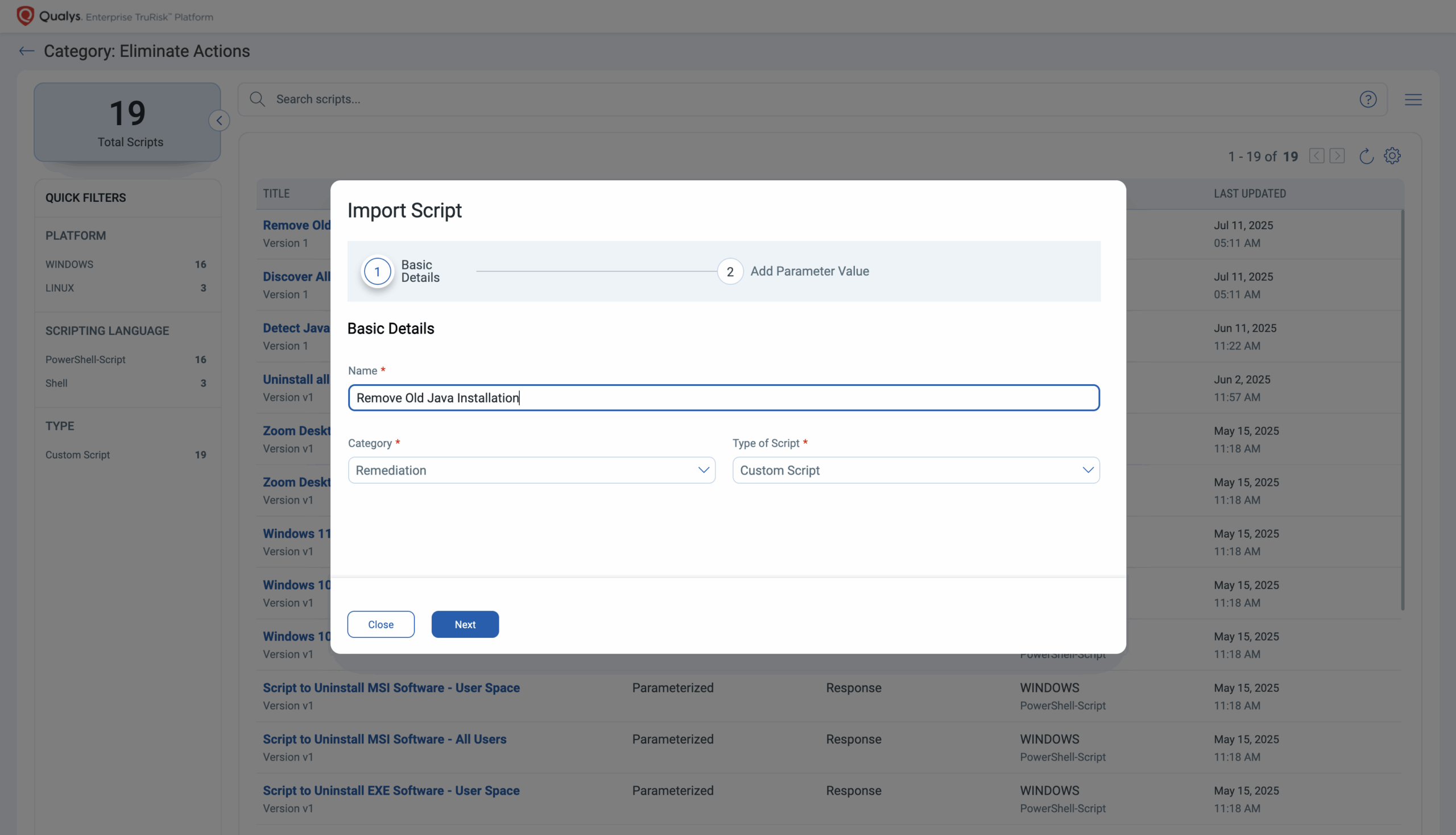
- Go to: Qualys CAR Library > Elimination Actions > Remove Old Java Installations
2. Click Import, then Define Parameters (e.g., minimum approved version)
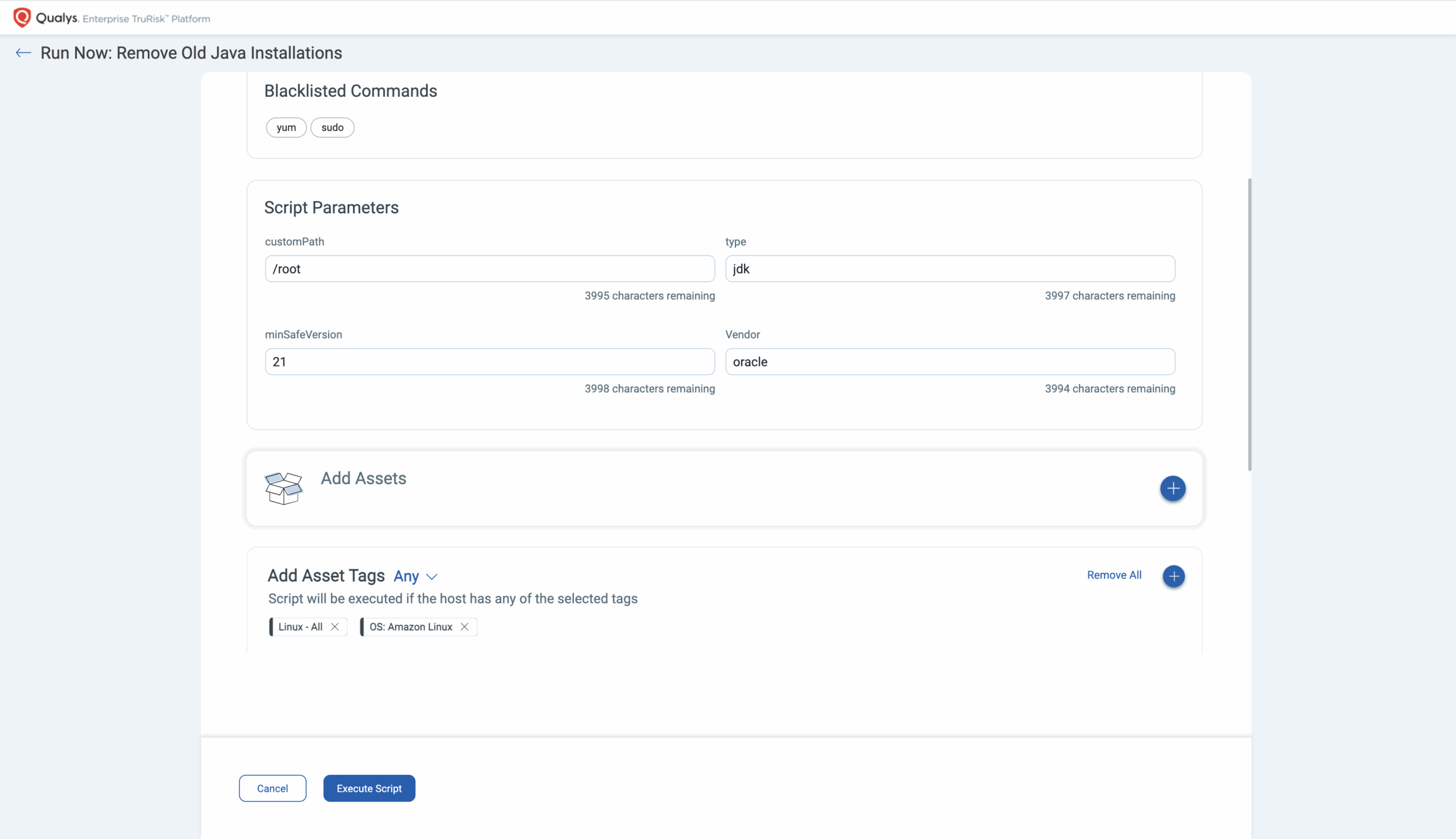
You don’t need to write the script. Everything is predefined, just provide the minimum safe version as a parameter, and any instance below that version will be removed once the script is executed.
3. Execute the script across your assets
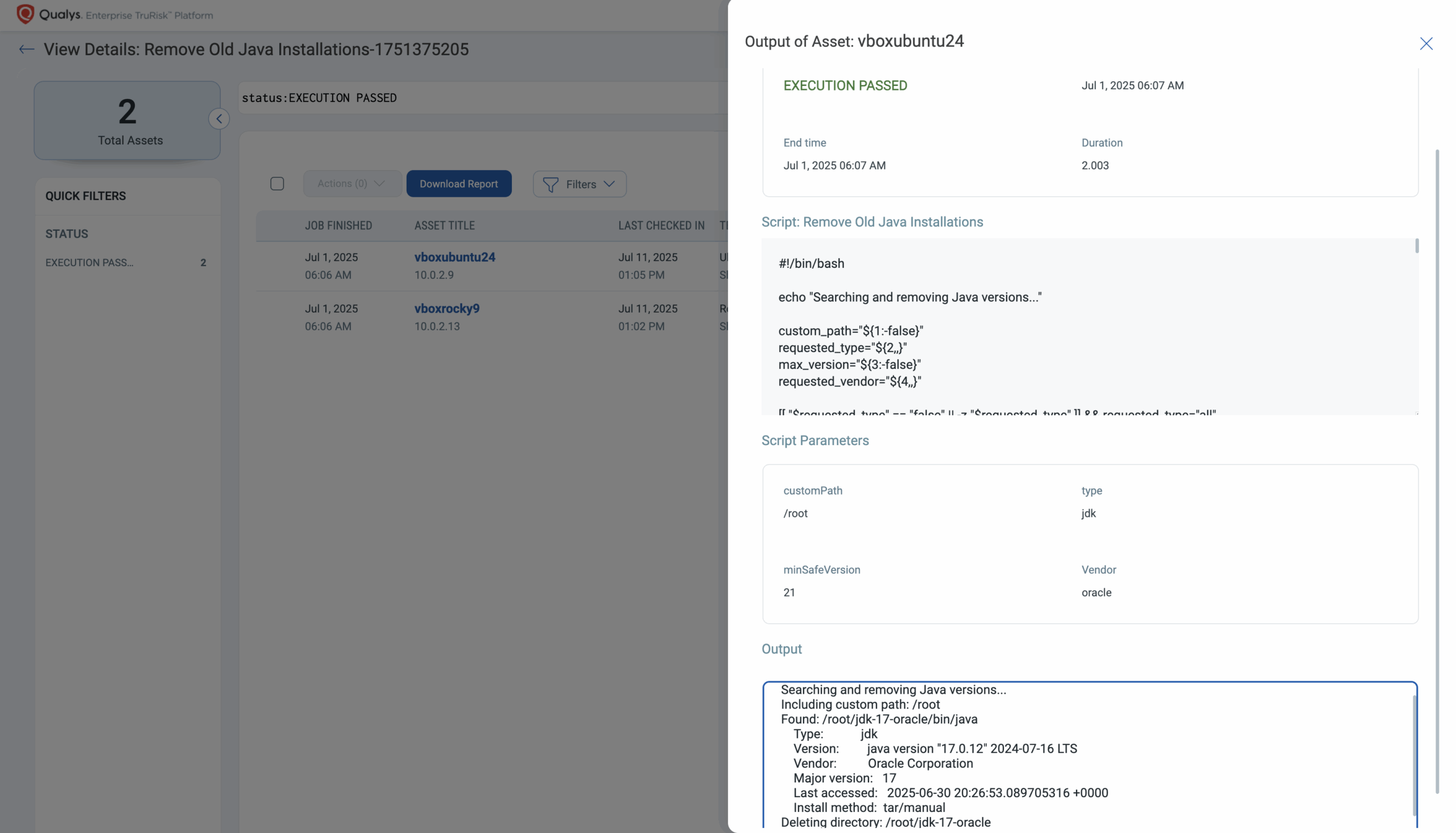
4. Review the output to confirm removal
5. Vulnerabilities related to removed Java versions will be automatically cleared
Conclusion
Qualys continues to evolve to meet the complex security needs of our customers. With the capabilities within TruRisk™ Eliminate, we provide comprehensive solutions that go beyond traditional patch management, ensuring that all vulnerabilities can be effectively addressed.
Save time and reduce your attack surface with Qualys TruRisk™ Eliminate