When Windows Management Instrumentation (WMI) classes fail, it can disrupt critical security operations by causing vulnerability scans to miss important data and compliance reports to lack accuracy. These issues may lead to gaps in visibility, making it harder for security teams to maintain a comprehensive understanding of their environment. By addressing WMI class failures proactively, organizations can ensure their systems remain resilient, their data accurate, and their risk posture strong.
This blog explores the “Invalid class” WMI issue, its operational and security implications, and how Qualys TruRisk™ Eliminate empowers teams to automate remediation at scale. Let’s dive into how to regain control, eliminate hidden risks, and ensure your systems are secure, compliant, and resilient.
Windows Management Instrumentation (WMI) is a built-in Windows feature that provides a standardized interface for querying and interacting with system-level data and operations. It acts as a bridge between the Windows operating system and management tools, scripts, or applications.
Understanding the WMI “Invalid Class” Issue
The “Invalid class” error in WMI indicates that the system cannot locate or access a specific WMI class being queried.
What Does This Mean?
This error occurs when the WMI repository fails to recognize or contain the class being queried. Common causes include:
- The class file (.MOF) was never loaded or compiled.
- The WMI repository is corrupted or partially rebuilt.
- A Windows update, driver installation, or application setup disrupted WMI consistency.
- Mismanagement or unregistration of WMI namespaces.
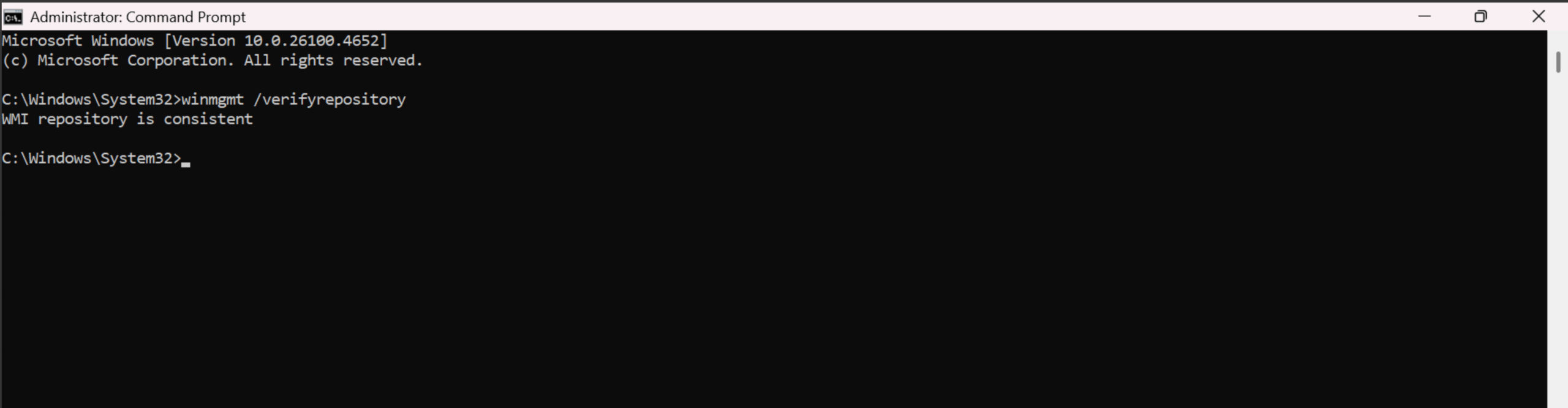
WMI Invalid Class but “WMI repository is consistent”
The repository verification check (winmgmt /verifyrepository) can report a “consistent” status even when critical WMI classes are broken. However, reviewing WMI Control Properties (wmimgmt.msc) can uncover deeper issues.
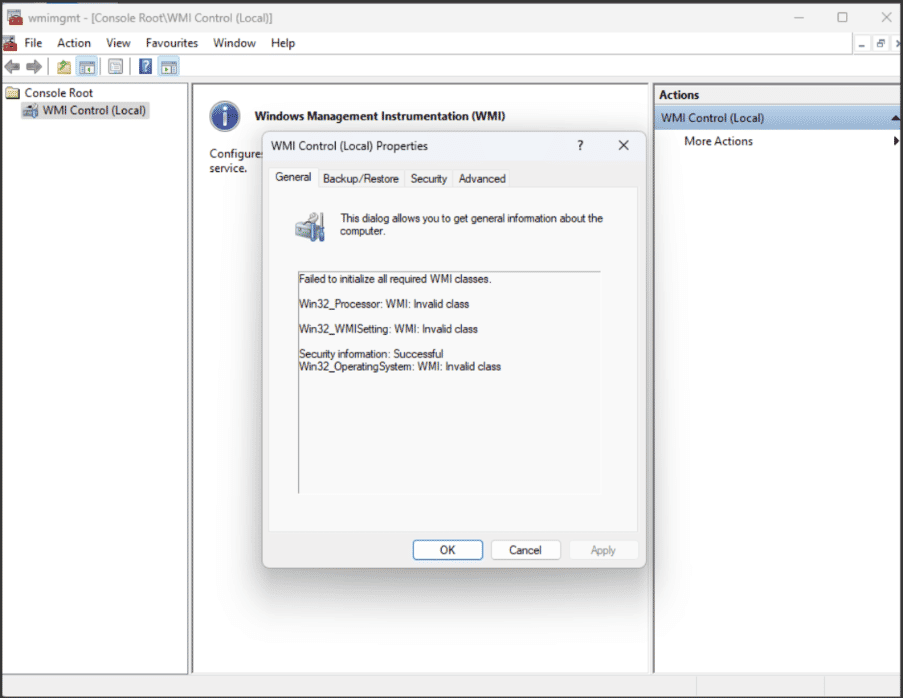
In one affected environment, the WMI Control Properties window showed:
- Failed to initialize all required WMI classes
- Win32_Processor — Invalid class
- Win32_WMISetting — Invalid class
- Security Information — Successful
- Win32_OperatingSystem — Invalid class
A “consistent” repository status doesn’t guarantee that all WMI classes are functional; broken classes can still disrupt detection and reporting without obvious signs.
Real-World Impact: Vulnerability Detection Failure
In anonymized data from the Qualys platform, we identified the “Invalid class” WMI issue, which was leading to significant operational impact.
Case Study:
A customer experienced detection failures for a critical QID across 10,000+ Windows assets:
- QID: 48032 — Microsoft Active Directory Organizational Unit (OU) Information
- Issue: This QID relies on WMI queries to fetch Active Directory OU data using specific WMI classes. Corruption or absence of these classes on endpoints led to silent detection failures, resulting in incomplete vulnerability data.
Risks posed by this issue:
- Security teams lacked OU context for impacted assets.
- Compliance reports were incomplete, creating potential audit risks.
Automate Fix with TruRisk™ Eliminate
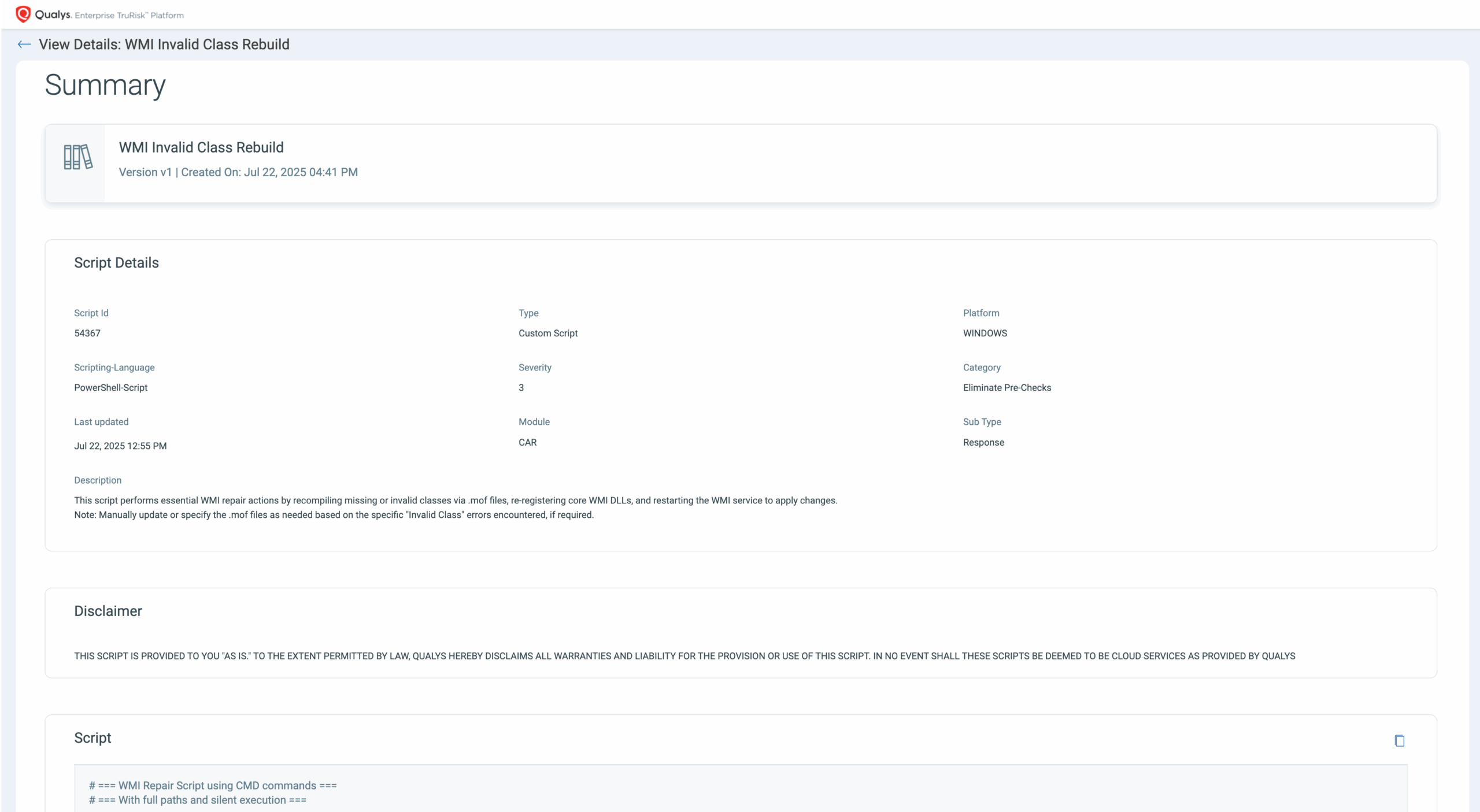
To resolve the WMI “Invalid class” issue across thousands of assets, users can leverage the out-of-the-box script, WMI Invalid Class Rebuild, available in the CAR Library under the Eliminate Pre-checks category.
What the Script Does:
Once deployed, the script:
- Recompiles all invalid or missing WMI classes by processing .MOF files.
- Re-registers core WMI DLLs.
- Restarts the WMI service to ensure proper functionality.
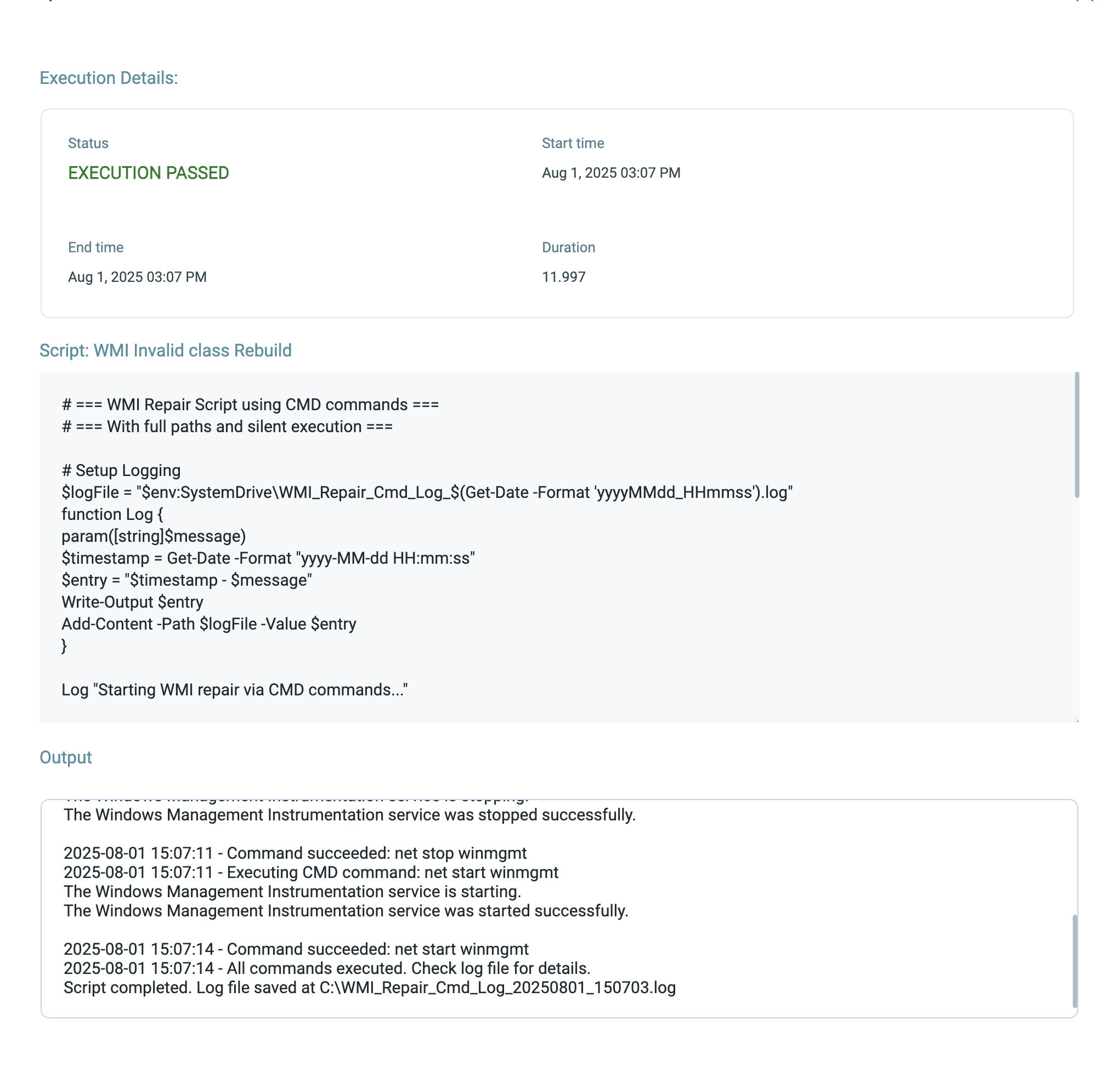
Script Output:
The script provides detailed logs, confirming the successful remediation of WMI class corruption.
Conclusion
Qualys TruRisk™ Eliminate, with its extensive script library, transforms complex, manual tasks into automated, scalable solutions. This use case demonstrates the value of Eliminate beyond patching, enabling deep system health and configuration remediation.
Ready to experience the power of TruRisk™ Eliminate?