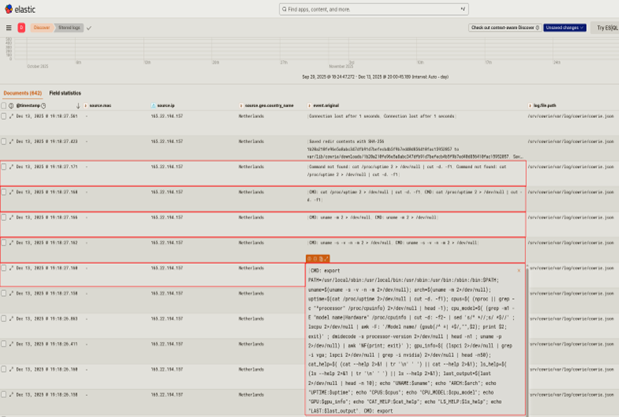
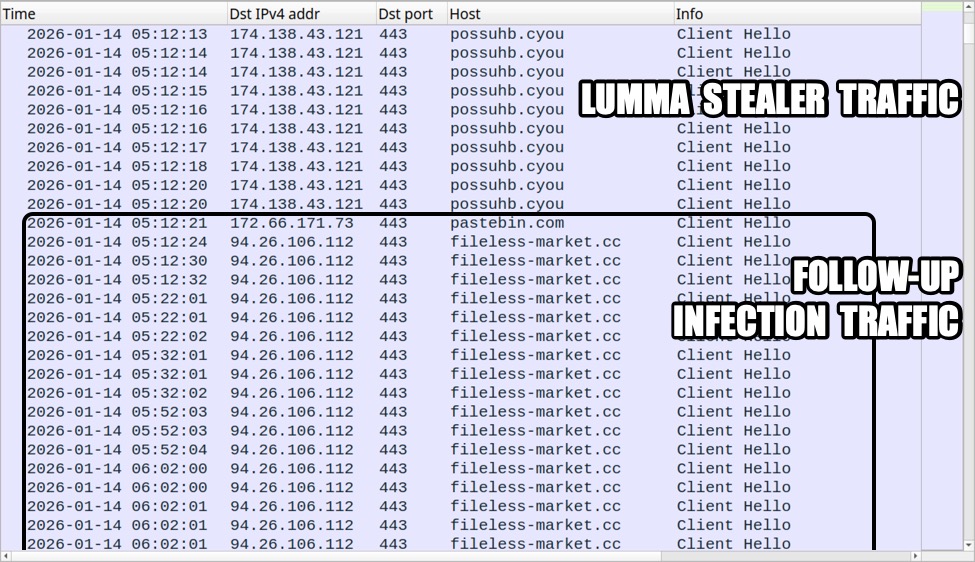
Integrating Rapid7 InsightIDR with ANY.RUN Threat Intelligence Feeds enhances security by delivering real-time, actionable insights directly into the SIEM platform. ANY.RUN Threat Intelligence Feeds stand out by delivering high-fidelity indicators of compromise (IPs, domains, URLs), extracted directly from live malware detonations in its Interactive Sandbox. The samples are submitted by more than 15,000 actively combating the latest cyber attacks.
Feeding this data into InsightIDR helps security teams quickly identify and correlate threats across their environment, improving both detection accuracy and response time. The added context enables deeper analysis, allowing teams to respond to active threats and proactively defend against emerging tactics and malware variants.
Unlike traditional sources that rely on post-incident reports and outdated indicators, ANY.RUN delivers real-time IOCs, giving SOC teams actionable intelligence on threats still active in the wild.
This real-time approach empowers organizations to respond to emerging threats at their earliest stages, staying ahead of attackers.
ANY.RUN Threat Intelligence Feeds with Rapid7
While InsightIDR includes a wide range of built-in detection rules, you can further strengthen threat detection by integrating Threat Intelligence Feeds from ANY.RUN. These feeds deliver specific indicators such as malicious IP addresses, domains, and URLs directly into InsightIDR. Soon, ANY.RUN Threat Intelligence Feeds will include file hashes for even stronger threat intelligence
When InsightIDR matches an indicator from your feed, it triggers one of several detection rules. Here’s what those look like in action:
-
Account Received Suspicious Link – Detects when a user receives a malicious link in their inbox
-
Account Visits Suspicious Link – Detects when a user clicks a tracked malicious URL, based on firewall or DNS logs
-
Suspicious Process Hash Discovered (This will be developed later by ANY.RUN)– Detects when a known malicious process hash runs on an endpoint
-
Ingress from Community Threat – Detects remote logins from IP addresses associated with subscribed community threats.
-
Ingress from Threat – Detects remote logins from IP addresses linked to threats you own or track directly
-
Network Access for Threat – Detects when a user accesses a domain or IP address listed in the threat feed.
If you receive detections from a community threat source such as ANY.RUN you can mark the alert as a false positive when closing the associated investigation.These alerts will not be allowlisted but will contribute to your false positive statistics on the Community Threats page.
Docs: Rapid7 and Utilizing Existing Threats
Benefits of adding a threat intelligence (TI) feed to a SIEM
Integrating ANY.RUN Threat Intelligence Feeds with Rapid7 InsightIDR significantly strengthens SOC capabilities by combining real-time IOCs with advanced detection and response features.
-
Enhanced Threat Detection – Real-time IOCs from live attack detonations help InsightIDR identify emerging malware and phishing campaigns. For example, analysts can correlate malicious URLs from ANY.RUN with email logs to flag early-stage phishing activity
-
Reduced False Positives – ANY.RUN’s pre-processed IOCs are curated for high confidence, helping reduce alert fatigue and allowing analysts to focus on verified threats
-
Proactive Threat Hunting – ANY.RUN feeds allow InsightIDR users to search historical logs or monitor active threats. For instance, teams can uncover supply chain attacks by matching IOC IPs against recent network activity
-
Streamlined Workflows – With automated correlation and enrichment, teams can take real-time actions like blocking malicious domains, streamlining triage and investigation
Adding a threat intelligence feed transforms your SIEM into a proactive, intelligence-driven defense system, enhancing visibility, reducing noise, and accelerating response.
Integrating ANY.RUN Threat Intelligence Feeds into Rapid7 IDR:
To integrate ANY.RUN’s Threat Intelligence Feeds with Rapid7 InsightIDR, follow this step-by-step guide. For users without a subscription, ANY.RUN offers a free trial.
During setup, configuration is managed through the .env file in your integration environment:
-
Feed update frequency – Adjust the ANYRUN_FEED_FETCH_INTERVAL setting to control how often the feed updates. By default, updates occur every 2 hours.
-
Feed freshness – Each new fetch removes old ANY.RUN community threat data and loads only the most recent indicators, improving detection accuracy and minimizing false positives.
-
Historical depth – Use ANYRUN_FEED_FETCH_DEPTH to define how far back the integration retrieves indicators. The default is 30 days.
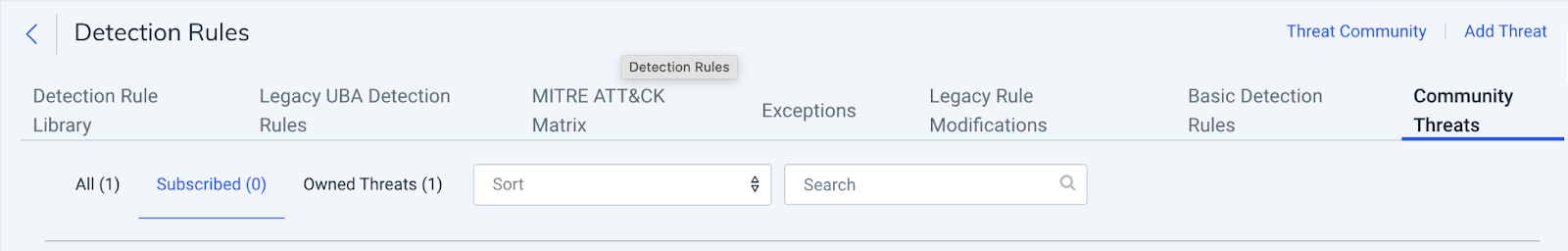
Once the integration is active and subscribed, your ANY.RUN threat feed will appear in your InsightIDR dashboard under:
Detection Rules → Community Threats → Subscribe:
Note: The ANY.RUN Threat Intelligence Feeds integration was developed by ANY.RUN and is not supported by Rapid7. For assistance with integration, please contact [email protected].