Overview
On October 6, 2025, the cyber deception company Defused published a proof-of-concept exploit on social media that was captured by one of their Fortinet FortiWeb Manager honeypots. FortiWeb is a Web Application Firewall (WAF) product that is designed to detect and block malicious traffic to web applications. Exploitation of this new vulnerability, now tracked as CVE-2025-64446, allows an attacker with no existing level of access to gain administrator-level access to the FortiWeb Manager panel and websocket command-line interface. Rapid7 has tested the latest FortiWeb version 8.0.2 and observed that the existing public proof-of-concept exploit does not work. However, the exploit does work against earlier versions, including version 8.0.1, which was released in August, 2025.
Based on the information circulated by Defused, this new vulnerability is claimed to have been exploited in the wild in October, 2025. On November 14, 2025, Fortinet PSIRT published CVE-2025-64446 and an official advisory for the critical vulnerability, which holds a CVSS score of 9.1. Organizations running versions of Fortinet FortiWeb that are listed as affected in the advisory are advised to remediate this vulnerability on an emergency basis, given that exploitation has been occurring since October in targeted attacks, and broad exploitation will likely occur in the coming days. A Metasploit module for CVE-2025-64446 is available here, and security firm watchTowr has published a technical analysis. CISA’s KEV catalog has been updated to include CVE-2025-64446.
It’s unclear whether the FortiWeb release cycle intentionally included a silent patch for this vulnerability or merely coincidentally included changes that broke the existing exploit.
On November 18, 2025, Fortinet published a new advisory for CVE-2025-58034. This new vulnerability is an authenticated command injection affecting FortiWeb. Fortinet has indicated CVE-2025-58034 has also been exploited in-the-wild, and CISA’s KEV catalog has been updated to include this new vulnerability. It is not clear at this time if both CVE-2025-64446 and CVE-2025-58034 have been exploited in-the-wild together as an exploit chain.
This blog post will be updated as new developments arise.
Rapid7 observations
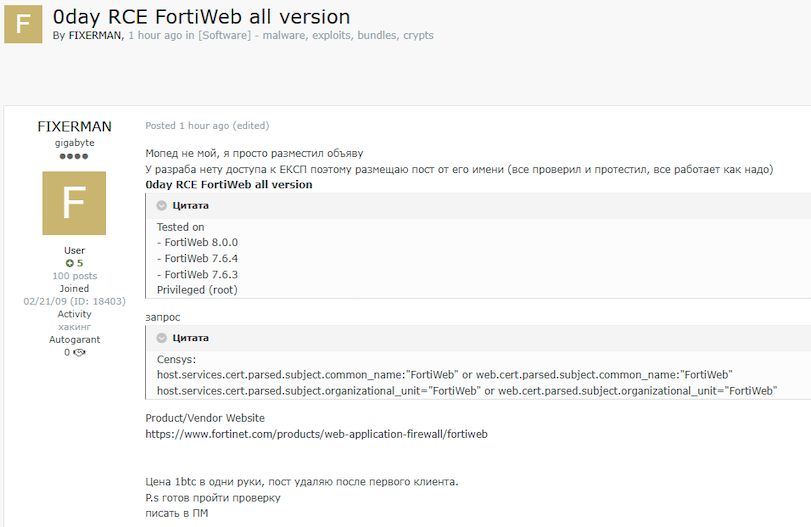
On November 6, 2025, Rapid7 Labs observed that an alleged zero-day exploit targeting FortiWeb was published for sale on a popular black hat forum. While it is not clear at this time if this is the same exploit as the one described above, the timing is coincidental.
⠀
Mitigation guidance
On November 14, 2025, Fortinet published an advisory that outlines remediation steps and workaround mitigations for CVE-2025-64446. According to Fortinet, the following versions are affected, and the fixed versions for each main release branch are also listed:
-
Versions 8.0.0 through 8.0.1 are vulnerable, 8.0.2 and above are fixed. -
Versions 7.6.0 through 7.6.4 are vulnerable, 7.6.5 and above are fixed. -
Versions 7.4.0 through 7.4.9 are vulnerable, 7.4.10 and above are fixed. -
Versions 7.2.0 through 7.2.11 are vulnerable, 7.2.12 and above are fixed. -
Versions 7.0.0 through 7.0.11 are vulnerable, 7.0.12 and above are fixed.
In cases where immediate upgrades are not possible, the advisory states the following: “Disable HTTP or HTTPS for internet facing interfaces. Fortinet recommends taking this action until an upgrade can be performed. If the HTTP/HTTPS Management interface is internally accessible only as per best practice, the risk is significantly reduced.”
Exploitation behavior
When testing the public exploit against a target FortiWeb device, the target application’s differing responses between versions 8.0.1 and 8.0.2 are included below.
Against version 8.0.1, the application returns the following response for a successful exploitation attempt, in which a new malicious local administrator account “hax0r” was created:
HTTP/1.1 200 OK
Date: Thu, 13 Nov 2025 17:57:28 GMT
Cache-Control: no-cache, no-store, must-revalidate
Pragma: no-cache
Strict-Transport-Security: max-age=31536000; includeSubDomains; preload
X-Frame-Options: SAMEORIGIN
X-XSS-Protection: 1; mode=block
Content-Security-Policy: script-src 'self'; default-src 'self'; style-src 'self' 'unsafe-inline'; font-src 'self'; img-src 'self' data:; connect-src 'self'; frame-ancestors 'self'; object-src 'none'; base-uri 'self'; upgrade-insecure-requests; block-all-mixed-content;
X-Content-Type-Options: nosniff
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: application/json
Content-Length: 1202
{ "results": { "can_view": 0, "q_ref": 0, "can_clone": 1, "q_type": 1, "name": "hax0r", "access-profile": "prof_admin", "access-profile_val": "1008", "trusthostv4": "0.0.0.0\/0 ", "trusthostv6": "::\/0 ", "last-name": "", "first-name": "", "email-address": "", "phone-number": "", "mobile-number": "", "hidden": 0, "domains": "root ", "gui-global-menu-favorites": "", "gui-vdom-menu-favorites": "", "sz_dashboard": 8, "sz_gui-dashboard": 7, "type": "local-user", "type_val": "0", "admin-usergrp": "", "admin-usergrp_val": "0", "password": "ENC XXXX", "wildcard": "disable", "wildcard_val": "0", "accprofile-override": "disable", "accprofile-override_val": "0", "fortiai": "disable", "fortiai_val": "0", "sshkey": "", "passwd-set-time": 1763056648, "history-password-pos": 1, "history-password0": "ENC XXXX", "history-password1": "ENC XXXX", "history-password2": "ENC XXXX", "history-password3": "ENC XXXX", "history-password4": "ENC XXXX", "history-password5": "ENC XXXX", "history-password6": "ENC XXXX", "history-password7": "ENC XXXX", "history-password8": "ENC XXXX", "history-password9": "ENC XXXX", "force-password-change": "disable", "force-password-change_val": "0", "feature-info-ver": "" } }⠀
However, against version 8.0.2, the application returns the following “403 Forbidden” response for an unsuccessful exploitation attempt:
⠀
HTTP/1.1 403 Forbidden
Date: Thu, 13 Nov 2025 17:28:42 GMT
Strict-Transport-Security: max-age=31536000; includeSubDomains; preload
X-Frame-Options: SAMEORIGIN
X-XSS-Protection: 1; mode=block
Content-Security-Policy: script-src 'self'; default-src 'self'; style-src 'self' 'unsafe-inline'; font-src 'self'; img-src 'self' data:; connect-src 'self'; frame-ancestors 'self'; object-src 'none'; base-uri 'self'; upgrade-insecure-requests; block-all-mixed-content;
X-Content-Type-Options: nosniff
Content-Length: 199
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=iso-8859-1
403 Forbidden
You don't have permission to access this resource.







