In today’s software-driven economy, every organization, regardless of industry, is a software company. And increasingly, every software company is an open-source company. With open-source components (OSS) now comprising up to 80% of modern codebase, the software supply chain has emerged as one of the most significant and most vulnerable frontiers in cybersecurity.
Unfortunately, adversaries have taken note.
Gartner predicts that by the end of 2025, 45% of global organizations will have experienced a software supply chain attack, a threefold increase since 2021. In just four years, these attacks have surged by 431%, pointing towards an evolving challenge: while OSS is indispensable for the accelerated pace of innovation, it also exposes development and security teams to considerable risk.
These risks are playing out in real time, disrupting businesses and escalating security costs. A recent Cybersecurity Ventures report estimates that the annual cost of software supply chain attacks will hit $60 billion by the end of 2025, up from $46 billion in 2023. With projections pointing to a steady 15% YoY increase through 2031, the financial stakes are mounting. Attackers are zeroing in on build pipelines, open-source dependencies, and AI/ML software supply chains by leveraging phishing, social engineering, and increasingly complex malware to exploit critical gaps.
Amid this rise in attacks, security leaders and enterprise architects continue to grapple with foundational challenges:
- Fragmented visibility across hybrid development environments
- Insufficient awareness of transitive dependencies between the application and components
- Lack of actionable insights derived from software composition data
- Difficulty contextualizing OSS risk in terms of real business impact
- Mounting compliance pressure from SBOM mandates to executive order directives
That’s reflected in the fact that only one in three organizations feels adequately prepared to defend against the threats posed by these foundational challenges. Nearly half admit they haven’t even identified the most vulnerable components in their software supply chain.
What CISOs, AppSec, DevSecOps Need and Aren’t Getting from Traditional SCAs
Legacy Software Composition Analysis (SCA) tools weren’t designed for today’s large-scale hybrid production environments or CI/CD pace. They operate in silos, produce static lists, and leave AppSec and DevOps teams struggling to answer the most critical questions:
- Which OSS components are exploitable in production?
- Which ones are actively used versus dormant?
- How does a vulnerability in this library impact business services?
Most tools stop at compiling a static list of outdated or vulnerable libraries, offering little more than a snapshot in time with no business context. As a result, security teams are often left buried in unactionable alerts, drowning in false positives with no clear remediation path.
Traditionally, Software Composition Analysis has lived in the developer toolchain as a code-level hygiene check. But as open-source dependencies have become deeply embedded in production systems, SCA is evolving into a strategic control point, one that spans development, security, operations, and compliance.
Qualys Software Composition Analysis (SwCA): Built for the Reality of Modern Enterprises
Qualys Software Composition Analysis (SwCA) was designed with these challenges in mind.
Fully integrated into the Qualys platform, SwCA transforms how organizations detect, prioritize, and respond to open-source risks. It correlates discovered vulnerabilities with real-time production data, CI/CD activity, and runtime behavior to determine what’s truly exploitable, what’s actively in use, and what needs immediate attention.
It’s a strategic capability that helps organizations to:
- Transform OSS data into business-aligned decisions.
- Empower developers with precise, low-friction remediation workflows.
- Support audit-readiness with living documentation and runtime assurance.
- Automate patching or mitigation workflows.
SwCA acts as a bridge between fragmented visibility and enterprise-wide confidence, equipping leaders to manage OSS risk without compromising velocity.
Since its initial release, SwCA has evolved significantly, expanding coverage and capabilities to help organizations better discover, assess, and remediate OSS risks. In the next section, we highlight key improvements made since the launch.
Watch Webinar
What’s New: Strategic Enhancements for 2025 and Beyond
Enterprise needs have evolved, and so has SwCA. The series of enhancements is designed to deepen coverage, improve visibility, meet compliance requirements, improve usability, and scale across enterprise environments. Through its latest major updates, SwCA advances its role as a frontrunner in securing software supply chains.
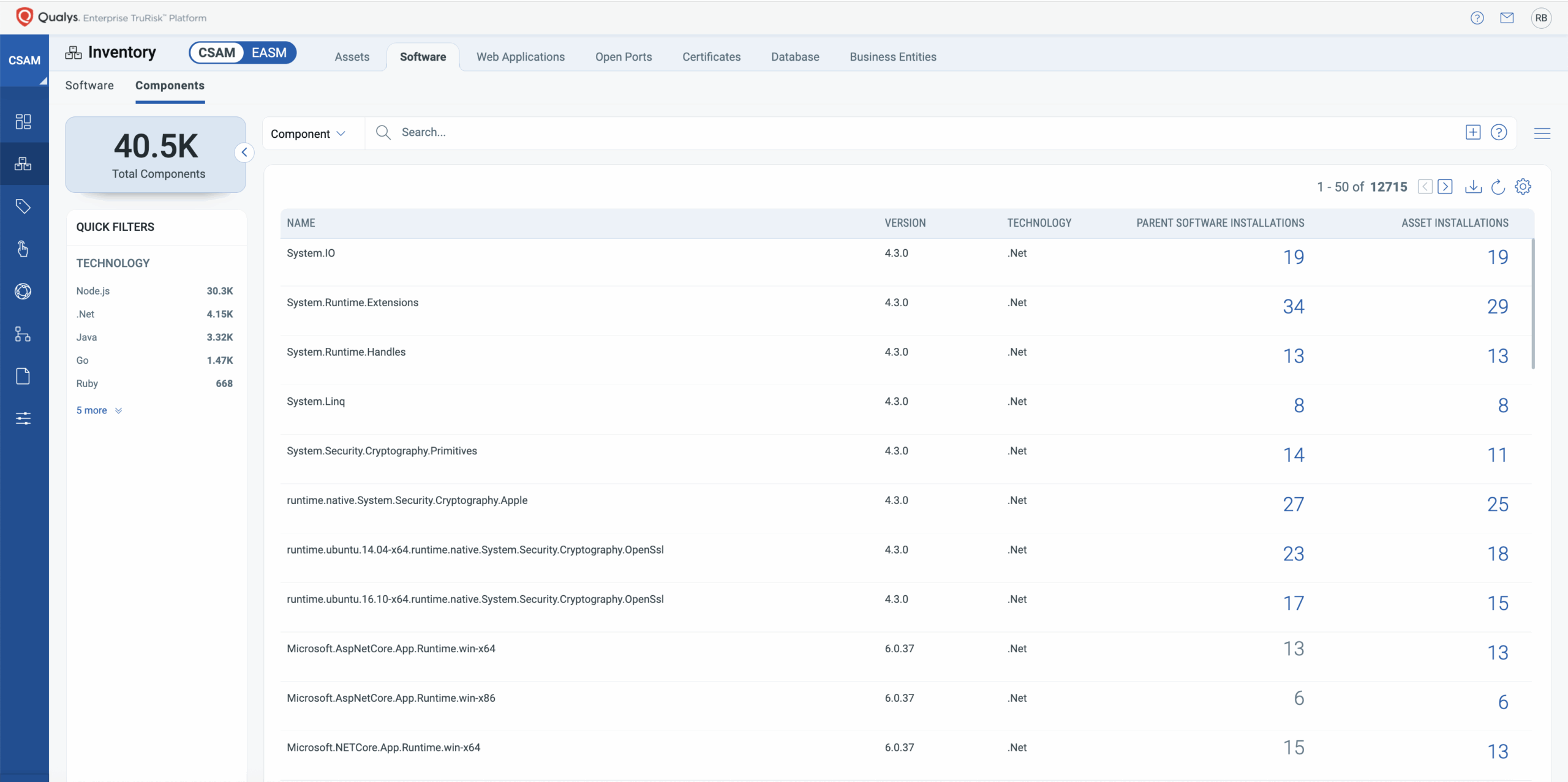
1. Software Atlas: Application-to-Component Mapping for Contextual Risk Assessment
Qualys SwCA introduces Software Atlas, the industry’s first native vulnerability management solution offering deeper insights into dependencies by mapping applications to their underlying components. Its robust software component-to-application mapping capabilities eliminate guesswork and manual tracking by giving you unprecedented insight to strengthen your software supply chain.
What this means in practice:
- Goes beyond basic inventory by mapping OSS components to the applications they impact
- Prioritizes issues based on real-world risk, e.g., customer-facing apps take precedence over internal tools
- Offers detailed visibility into component-to-application relationships for smarter decision-making
- Accelerates remediation by up to 60% by pinpointing root component issues across multiple dependencies
This contextual mapping transforms static inventory into operational insight. By surfacing these linkages, risk teams can now align OSS risk with business value, ensuring the most impactful issues are resolved first without drowning in false positives or low-priority alerts.
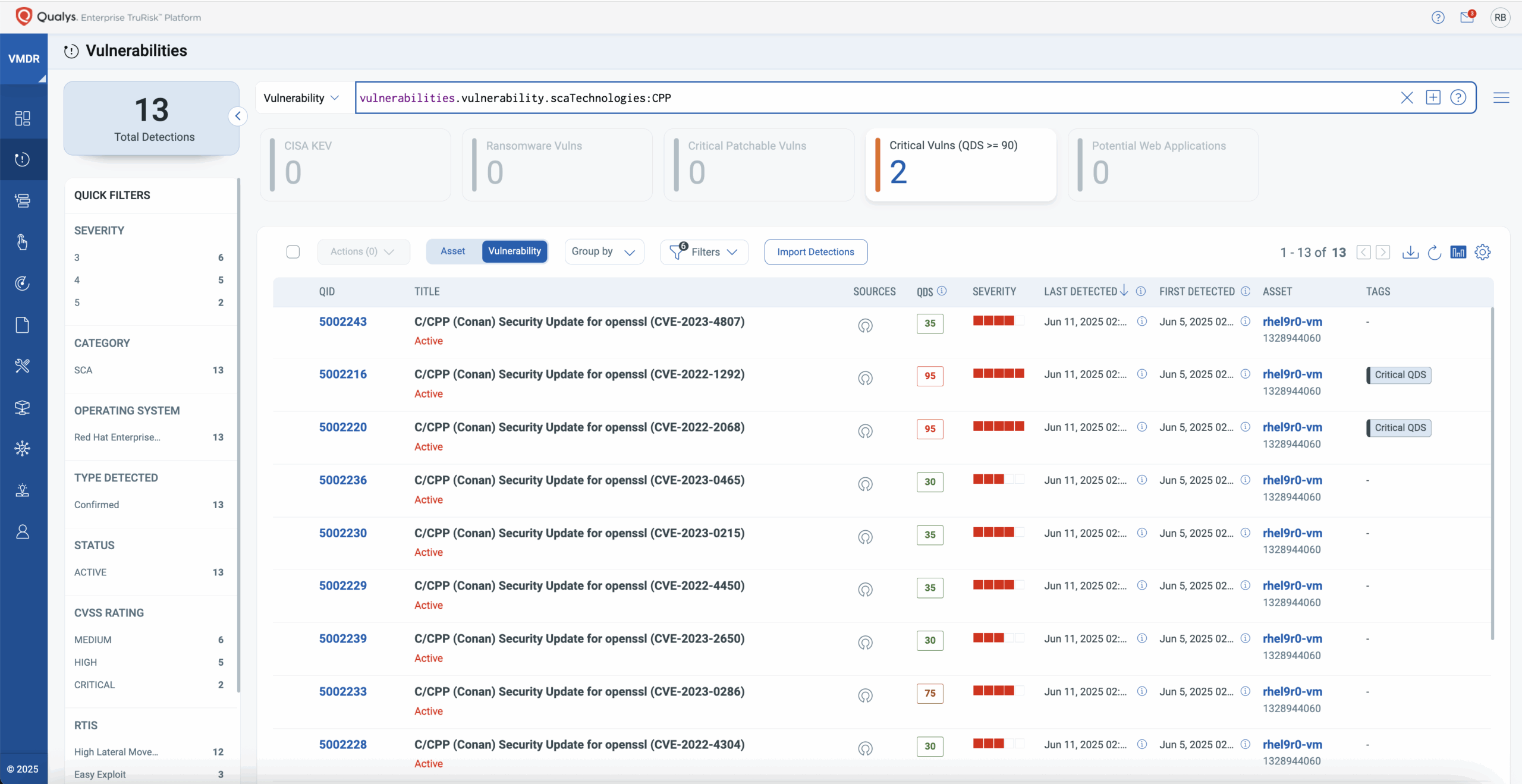
2. C/C++ Detection: Exposing Blind Spots in Legacy Code
While modern languages benefit from mature OSS visibility tooling, C and C++ have long remained opaque due to compilation, static linking, and lack of manifest metadata. This has left critical legacy systems—often central to telecom, embedded, aerospace, and finance—exposed to undetected supply chain risks.
The enhanced SwCA now brings first-class support for C/C++ binaries, enabling DevSecOps teams to:
- Analyze ELF and PE binary formats without requiring access to source code.
- Surface vulnerabilities in statically linked libraries that traditional Software Composition Analysis tools often miss.
- Correlate discovered risks with TruRisk™ scoring, placing C/C++ issues in the same prioritization pipeline as modern tech stacks.
- Gain unified visibility across mixed-language environments from a single platform.
This expansion closes a critical visibility gap in software supply chain security, empowering teams to monitor and mitigate risk in foundational infrastructure previously out of reach. For sectors where C/C++ codebases persist, this capability is not just valuable but essential.
3. Streamlined Remediation with Smarter Ticketing
One of the longstanding challenges in software supply chain security is translating raw scan data into developer-friendly, trackable tasks, especially in environments where applications share libraries or span multiple ownership domains.
With enhanced QID result parsing, SwCA now enables:
- Granular ticket generation: Each vulnerable component is individually parsed and mapped to the right owner or development team for targeted remediation.
- Seamless workflow integration: Native support for tools like Jira and ServiceNow turns vulnerability data into structured, trackable remediation tasks.
- Clean separation of concerns: Scan output is organized to align components with the teams responsible, streamlining ownership and accountability and misrouting of issues.
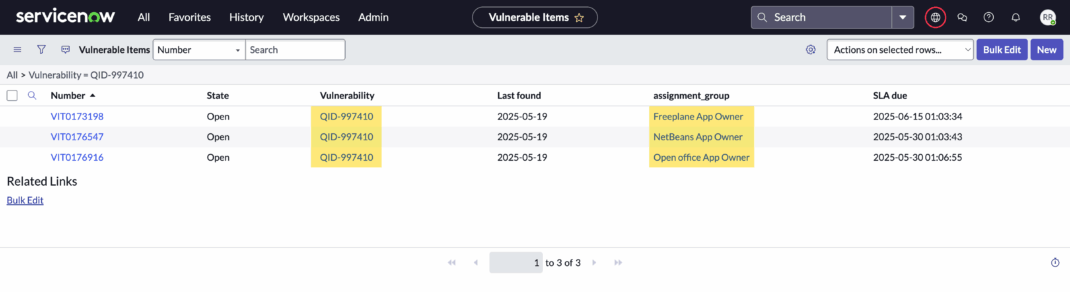
This upgrade transforms Qualys SwCA to help teams hand off issues directly to developers or app owners, operationalize vulnerability remediation at scale, eliminate manual processes, and ensure no risk signal gets lost in translation. By embedding SwCA into existing CI/CD workflows, organizations gain greater efficiency, precision, and accountability across the remediation lifecycle.
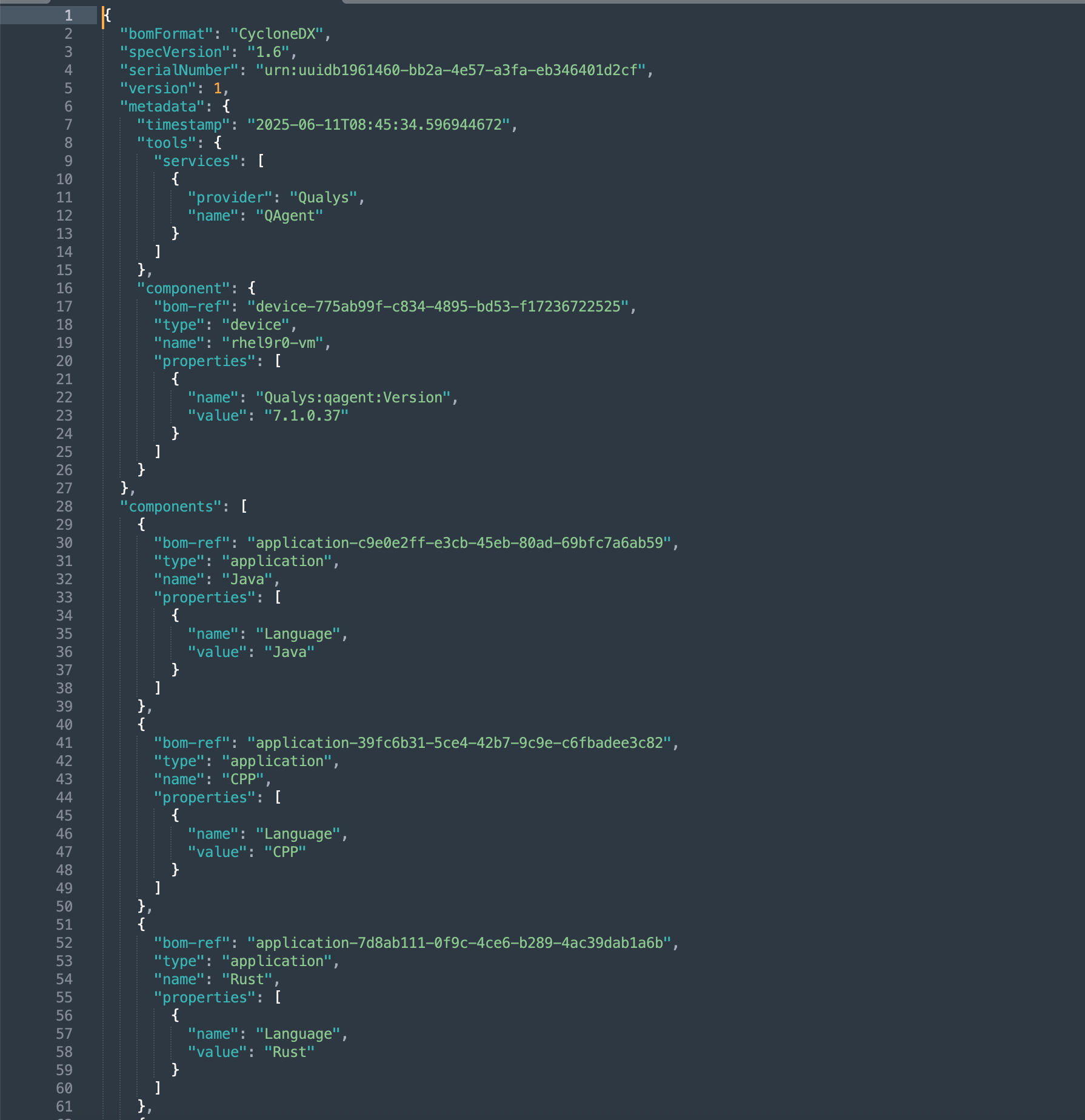
4. SBOM Generation for Transparent and Trustworthy Software Supply Chains
SBOMs are no longer a ‘nice to have.’ Compliance standards, executive orders, and customer SLAs demand them. Qualys SwCA now supports Software Bill of Materials (SBOM) generation in CycloneDX 1.4 and 1.6 formats via both the UI and API, making it easy to embed transparency into DevSecOps pipelines.
How these living SBOMs enable full-stack transparency:
- Comprehensive visibility: Generates a detailed, structured list of all open-source components within each application.
- Always up to date: Produces living SBOMs that automatically update with every new scan.
- Risk-aware inventory: Ties each component to real-time vulnerability and risk insights for proactive decision-making.
This helps teams proactively manage exposure, streamline compliance, and respond faster to emerging vulnerabilities in the ecosystem.
5. Runtime Software Composition Analysis: From Inventory to Exposure
Traditional SwCAs often focus on what’s built or deployed, but lack visibility into what is actually running in production. With runtime visibility via Qualys Cloud Agent, Qualys SwCA now shows which components are actively running, not just installed.
See what’s running, not just what’s deployed:
- Focus on real risk: Distinguishes between dormant and active components to prioritize OSS libraries that actually impact runtime.
- Smarter triage: Helps teams deprioritize inactive components and zero in on those loaded and in use.
- Continuous monitoring: Automatically assesses and tracks new components as they’re introduced or activated in production.
- Bridges key gaps: Connects static build-time analysis with real-world, runtime exposure for a more accurate risk picture.
This approach aligns OSS risk with real-world execution contexts, reducing wasted effort and improving resilience.
6. Enterprise Scalability: Designed for Global Operations
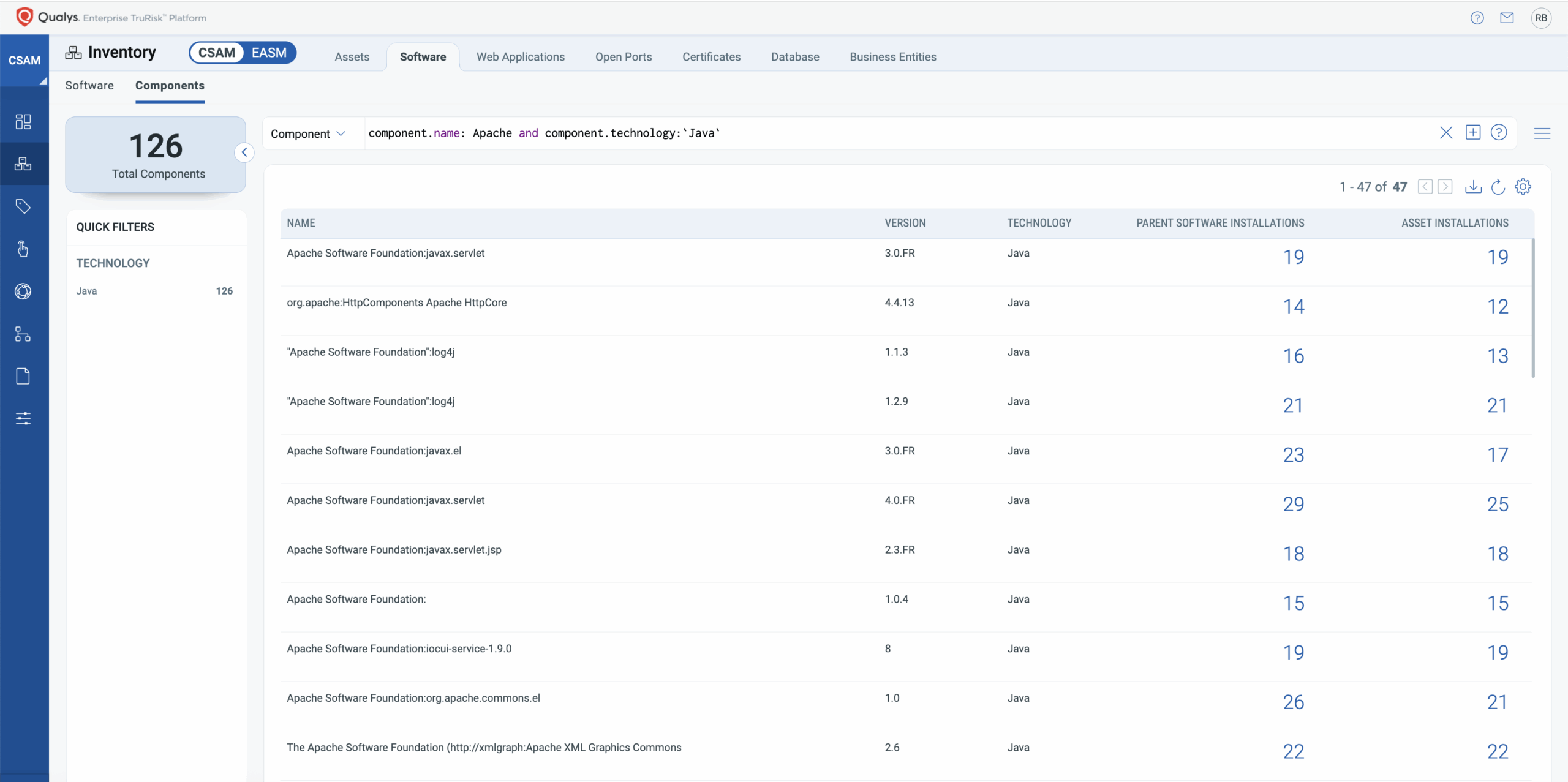
Enterprise software ecosystems can span thousands of components per asset. The enhanced Qualys SwCA now supports visibility into 20,000+ OSS components per asset, ensuring no risk goes unseen, no matter the scale. To complement this, it also introduces advanced query tokens like Component.name, Component.version, and Component.technology.
These allow DevSecOps teams to:
- Drill into specific risk profiles across vast environments.
- Filter and sort with precision in both UI and API workflows.
- Integrate seamlessly into analytics pipelines and automation tools.
With these powerful enhancements, teams can operationalize OSS insights across the organization with confidence and clarity, and eventually help enterprises move from mere data collection to decisive, value-driven action.
Real-world Impact: What Security Leaders Actually Gain
Qualys SwCA’s enhancements are direct responses to the reality faced by today’s enterprise security and risk leaders.
Here’s what that looks like in action:
| Strategic Advantage | Operational Impact |
| Business-Aligned, Contextual Risk Prioritization | Precisely map application-to-component relationships to prioritize remediation efforts based on business impact, accelerating risk reduction and improving mean time to remediate (MTTR) for critical, customer-facing applications. |
| Expanded Visibility Across Legacy Systems | Surface risks in C/C++ binaries, often blind spots, using TruRisk™ scoring to bring parity in risk evaluation across modern and legacy stacks. |
| Accelerated Remediation Through Workflow Integration | Automate creation of precise, component-level tickets tied to app ownership in JIRA and SNOW, enabling faster triage and resolution with fewer handoffs. |
| Software Supply Chain Transparency at Scale | Deliver live SBOMs enriched with vulnerability data for real-time compliance readiness, risk audits, and Zero Trust enforcement. |
| Real-World Risk Exposure Insights | Focus patching on actively executed OSS components in production, reducing false positives and aligning remediation with runtime behavior. |
| Scalable, Actionable Software Inventory Management | Efficiently manage and analyze large OSS footprints using flexible queries and metadata tokens, enabling enterprise-grade DevSecOps performance. |
Closing the Risk Gap in Software Supply Chains
In 2025, securing your software supply chain isn’t a checkbox exercise but a continuous, strategic discipline. With OSS usage only rising and attacker sophistication increasing in lockstep, modern enterprises must build resilience into their development and delivery pipelines.
What this requires is more than a scanning tool. It demands:
- Context over quantity
- Risk alignment over CVE counts
- Streamlined remediation built for Dev speed
- Continuous assurance over one-time audits
Qualys Software Composition Analysis (SwCA) meets these demands. With a deep commitment to continuous innovation, spanning runtime analysis, contextual mapping, SBOM generation, and extensive multi-language coverage, SwCA empowers security leaders to stay ahead of threats while aligning with operational realities. These enhancements bridge the gap between security and development, streamline remediation, and improve transparency, which are key pillars for building secure, trustworthy, and resilient software in the current threat landscape.
And more importantly, it reflects a shift in how leading organizations approach software risk as a business problem and not just a security one.
See What Proactive OSS Defense Looks Like
Software supply chain threats are growing, but with the right tools, your organization can grow stronger by tackling them head-on.
Ready to experience how Qualys SwCA with contextual OSS insights can accelerate your risk response?
Contact your Technical Account Manager (TAM) to explore how the Qualys SwCA solution can be customized to align with your existing DevSecOps pipelines and operationalize contextual risk scoring.