[This is a guest diary by Christopher Crowley, https://montance.com]
Here’s a good reason to include security awareness training for new hires!
I recently added an account to my Google Workspace domain (montance[dot]com). Friday, May 16th, 10:10 am, to be exact. Something interesting to note about the domain configuration is there’s a catchall account in place, so all email addresses are valid.
Starting May 28th the new account started receiving targeted phishing email messages. The subject was either blank or a variation of my name (Chris or Christopher), and the sender’s “From” address had a call to action and urgency:
From: "EMERGENCY: PROVIDE YOUR CELL NUMBER IMMEDIATELY"
From: "EMERGENCY:PROVIDE YOUR CELL PHONE NUMBER IMMEDIATELY ASAP"
From: "EMERGENCY; PROVIDE YOUR CELL PHONE NUMBER IMMEDIATELY"
From: GET BACK TO ME IMMEDIATELY
From: JUNE THURSDAY 5TH
From: Quick Response
From: RESPONSE REQUIRED
From: Timely Reminder
The messages all indicated that there were some urgent tasks to perform and that I supposedly needed the person’s phone number. There were 8 unique email addresses used, all of which invoke the concept of urgency:
hoursworking605--at--gmail_com
immediatelyofficemail79--at--gmail_com
officeoperatedeskboxx360--at--gmail_com
promotionaltask747--at--gmail_com
promotiontask910--at--gmail_com
quickreply946--at--gmail_com
quicktask5511--at--gmail_com
urgentmails696--at--gmail_com
All of these went into the Spam folder until June 10th, when a couple got through. Noteworthy, almost all of the email salutations used the recipient’s LinkedIn name. This is obvious because his name on LI includes certifications. Then on June 10th, they sent him a text message:
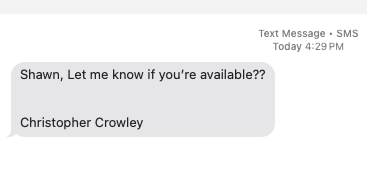
This is likely reasonably automated phishing with low targeting specificity, but the identification of the new account and fast phishing was interesting. In my case, it was easy to observe since there are so few accounts in the domain and he’s a vigilant and cyber-aware person. MFA is enabled.
One question I have for readers: does anyone have a script or know of a project that’s an equivalent of Invoke-MSOLSpray targeting Google Workspace domains? Someone must be using something like that to discover new accounts. The email address wasn’t posted online anywhere. His LinkedIn profile has a different email address. So, there was some amount of correlation the sender of the spam did.
Nothing especially surprising, but a reminder that they’re watching for opportunities. Someone new at the company and eager to appear responsive seems like a good phishing target!
—
Christopher Crowley
Author, Consultant, Instructor
https://montance.com