Qilin has quietly become one of the most active and impactful ransomware operations in the world today. If it’s not already on your threat radar, now is the time to take notice. This blog unpacks how Qilin operates, why it’s gaining traction across cybercriminal networks, and what steps security teams can take to get ahead of it before it becomes a response priority.
Let us first understand why it has rapidly gained popularity on the Dark Web and is now the top ransomware threat in the world.
Bottom Line Up Front (BLUF):
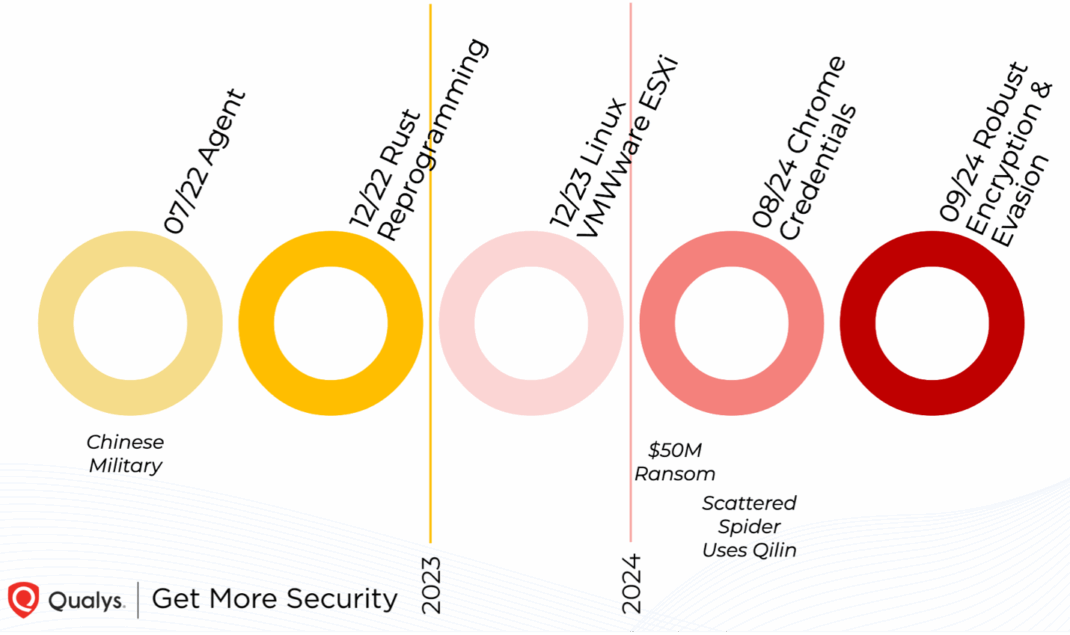
- Originally authored as ‘Agent’ in 2022 and later recoded in Rust.
- Gained popularity by late 2023 through targeted attacks on VMWare ESXi infrastructure.
- Expanded capabilities in 2024 to include Chrome Stealer functionality and robust encryption and evasion tactics.
- Amassed over $50 million in ransom payments in 2024 alone.
- Ranked as the most prevalent ransomware in public threat intelligence reports by 2025.
- Backed by a strong operational model, including legal support for clients (“Call Lawyer”), and incentives and technology for successful, unprecedented ransomware payouts.
Qilin Ransomware Explained: Language, Affiliations, and Targeting Patterns
Qilin was originally authored by the Dark Web moniker “BianLian”, with early deployments reportedly linked to clients associated with the Chinese military and other government-aligned entities, according to open-source intelligence. Over time, its use has expanded, with notable threat actor groups, such as Scattered Spiders and entities linked to North Korea, now observed leveraging Qilin in active campaigns.
Qilin (麒麟 ) is likely named after the mythical Chinese hoofed creature (like a unicorn), symbolizing power, prosperity, and greatness, a fitting metaphor for the perceived influence and financial gains associated with ransomware payouts and criminalization. Linguistic and behavioral indicators provide further attribution clues. BianLian has been observed communicating in both Russian and English, especially on Russian Dark Web forums. Similarly, Qilin’s malware is designed to avoid targeting systems in the Commonwealth of Independent States (CIS), a common trait among threat actors linked to Russian cybercriminal networks. These patterns strongly suggest that Russian-speaking individuals or groups are involved in supporting the Qilin Ransomware-as-a-Service (RaaS) operation.
Below is the Qilin logo, as seen on their Dark Web leak site:
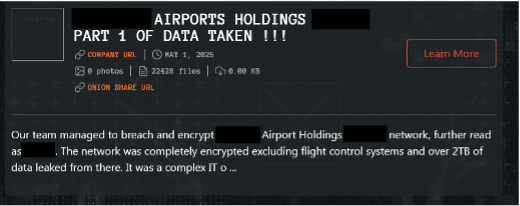
Qilin performs double extortion of victims, with rapid, high-speed, robust encryption and deletion of backups of targets and exfiltration of data as seen in this Dark Web leak (sanitized) below:
Qilin has been linked to attacks across more than 25 countries and countless targets to date. As of May 2025, public sources have identified Qilin as the leading ransomware threat overall. This stands out in a year marked by a proliferation of new ransomware groups, all vying for a share of this increasingly lucrative market. Qilin stands above the rest with its rapidly rising marketplace due to a mature ecosystem, extensive support options for clients, and robust solutions to ensure highly targeted, high-impact ransomware attacks designed to demand substantial payouts.
Qilin strategically targets three primary verticals, where payouts are more likely:
- Manufacturing
- Legal & Professional Services
- Financial Services.
They also regularly target critical infrastructure and larger organizations with a big pocketbook, using an online website to estimate potential payouts in advance, to focus on high-value financial opportunities.
An FBI report identified over 1,700 ransomware attacks in 2024, with reported earnings totaling $91 million. However, the actual figures are likely much higher due to the opaque and underreported nature of the cyber extortion ecosystem. The U.S. Department of Health and Human Services (HHS) also reported Qilin-related losses across multiple victims, with damages ranging from $6 million to $40 million, primarily affecting healthcare and government agencies across the Americas.
Common forms of Initial Access are gained through the following:
- Spearphishing
- Remote Monitoring & Management Software Exploitation
- Lateral Movement & Exploitation
- Multifactor Authentication (MFA) Bombing
- SIM Swapping
Recent Qilin B variants have the following important capability upgrades:
- Chrome Extension Stealer
- Encryption Enhancements (Faster, more secure, and nearly impossible to decrypt)
- AES-256-CTR – Advanced Encryption Standard (AES) with a 256-bit key and Counter (CTR) mode of operation.
- Optimal Asymmetric Encryption Padding (OAEP) to enhance security making it more resistant to certain attacks.
AES-NI (Advanced Encryption Standard New Instructions) capabilities for x86 architecture to accelerate the AES encryption and decryption processing.
- ChaCha20 for modern, fast, and secure streamed cipher communications.
- AES-256-CTR – Advanced Encryption Standard (AES) with a 256-bit key and Counter (CTR) mode of operation.
- Security Evasion
- Clears Windows event logs and deletes itself to hinder forensics evidence and IR research and response.
- Backup Corruption
- Deletes Windows Volume Shadow Copy Service (VSS) to hinder recovery in forcing payouts.
Rethink Ransomware Defense: Why Qilin Is a Wake-Up Call for Resilience
Proactive ransomware defense, especially to the left of boom, is not only more strategic but also more cost-effective than a reactive risk acceptance approach. Qilin has now emerged as a persistent and pervasive threat knocking at the door of every major organization in the world. A review of their dump site also reveals smaller organizations among the victims, underscoring that no entity is immune. Given their widespread reach, methods of exploitation, and varied motivations, Qilin now ranks as a top-priority threat across both eCrime and nation-state threat models.
For security teams looking for indicators of compromise (IOCs), it’s important to note that our CTI team emphasizes tactics, techniques, and procedures (TTPs) and broader strategic patterns over tactical signatures. However, a wealth of vetted and actionable IOCs is readily available through trusted sources, including the US. Department of Health and Human Services’ threat profile on Qilin, among other trusted sources online. These resources are invaluable for enriching your threat intelligence feeds or building familiarity with this ransomware family.
How to Prepare for Threats Like Qilin: Strategic Readiness Starts Left of Boom
To stay resilient against sophisticated threats like Qilin ransomware, organizations need a proactive, well-rounded strategy. From strengthening user awareness to validating incident response and hardening technical environments, the following measures help build confidence in your readiness and reduce exposure across the board:
User-Awareness
Educate users on the threat of Qilin ransomware, phishing, and other initial vectors, and how to practice safe cyber hygiene to reduce risk.
Incident Response Readiness
Emulate a Qilin ransomware incident to ensure MTTD/R operational excellence and verify that tools and alerts perform as expected within the organization’s technical environment. Also, conduct a tabletop exercise focused on a payout scenario, where recovery is not expected, to educate and align key leaders and stakeholders, including third parties and law enforcement. Use this to identify gaps in policies, procedures, insurance, regulatory compliance, alignment, and overall readiness.
Threat & Vulnerability Patch Management (TVM)
Is your software patched in a prioritized and timely manner to prevent exploitation by Qilin? For example, it has previously exploited CVE-2023-27532 as part of MITRE ATT&CK ID T1190. To reduce this exposure and risk, all network-facing and remotely exposed solutions at higher risk for Qilin must be prioritized for patching.
Antivirus Software
Use one or more anti-virus programs to help detect and block Qilin ransomware. Consider using one type of anti-virus for email and another for endpoints to build a more robust, multi-layered defense against the Spearphishing tactics used by Qilin.
Endpoint Threat Detection
Qilin executes a variety of scripts, including PowerShell and command-line interpreter events, which can be detected and/or blocked by a strong endpoint security solution before it can take over a system and/or network. Behaviorally, it also attempts to terminate anti-virus software, perform process injection, and make persistence-related changes to the registry, which are typically detectable. See the MITRE ATT&CK chart below for more details.
Network Discovery & Alerting
Do you have controls in place to detect scanning, lateral movement, and other behaviors consistent with Qilin’s propagation methods?
Immutable Backups
Qilin targets the deletion of Microsoft Windows VSS backups. Do you have an immutable ‘vault’ backup strategy in place? Have you demonstrated that it works as intended? Do you regularly (e.g., monthly) perform recovery exercises to ensure resiliency, redundancy, and recovery capabilities?
Prohibit Personal Devices
Personal devices in use in a corporate setting or on a corporate device can be an infection vector or carriers of Qilin. Enforce policy and technical controls to block such risks, including restrictions on USB usage, installation of unauthorized software, unauthorized device access, etc. Where possible, move to a whitelisting model.
Advanced Architecture
Implement Zero Trust Architecture (ZTA), with isolation and segmentation, to limit blast radius in case of a ransomware or similar network-aware breach, by design.
Use this list to identify specific TTPs used by Qilin to map against your own defensive solutions to protect to the left of boom, harden, and demonstrate in penetration and purple team tests, that defenses work as expected:
| ID | Description |
| T1078.002 | Valid Accounts: Domain Accounts |
| T1021.002 | Remote Services: SMB/Windows Admin Shares |
| T1566 | Phishing |
| T1566.001 | Spearphishing attachment |
| T1566.002 | Spearphishing link |
| T1190 | Exploit Public-Facing Application |
| T1190 | Exploit Public-Facing Application (CVE-2023-27532) |
| T1053 | Scheduled Task/Job |
| T1059.003 | Command & Scripting Interpreter |
| T1059.001 | PowerShell |
| T1037 | Boot or Logon Initialization Scripts |
| T1068 | Exploitation of Vulnerabilities |
| T1548 | Abuse Elevation Control Mechanism |
| T1055 | Process Injection |
| T1014 | Rootkit |
| T1204.002 | User Execution: Malicious File (e.g. C:\temp à w.exe) |
| T1211 | Exploitation for Defensive Evasion |
| T1133 | External Remote Services |
| T1480 | Execution Guardrails |
| T1497 | Virtualization/Sandbox Evasion |
| T1027 | Obfuscated Files or Information |
| T1003.001 | OS Credential Dumping, LSASS Memory |
| T1082 | System Information Discovery |
| T1010 | Application Window Discovery |
| T1046 | Network Service Scanning |
| T1018 | Remote System Discovery |
| T1134 | Access Token Manipulation |
| T1021.001 | Remote Servies, Remote Desktop Protocol, SSH |
| T1021.004 | Remote Servies, Remote Desktop Protocol, SSH |
| T1005 | Lateral Tool Transfer |
| T1569.002 | System Services: Service Execution |
| T1005 | Data from Local System |
| T1011.001 | Exfiltration Over Other Network Medium, Exfiltration Over Bluetooth |
| T10001.001 | Data Obfuscation, Junk Data |
| T1486 | Data Encrypted for Impact |
| T1485 | Data Destruction |
| T1490 | Inhibit System Recovery |
| T1561.001 | Disk Wipe |
| T1070 | Indicator Removal |
| T1562.001 | Impair Defenses: Disable or Modify Tools |
| TA0007 | Discovery |
| TA0040 | Impact |
| T1490 | Inhibit System Recovery |
| T1486 | Data Encrypted for Impact |
| T1529 | System Shutdown/Reboot |
Conclusion
Qilin is now one of the most prominent ransomware threats globally. Its rapid rise, adoption by advanced threat actors, and the growing number of victims in late 2024 and early 2025 point to sustained activity well into the year ahead.
Proactive defensive measures, such as a well-tested incident response plan, the ability to isolate and segment ransomware activity, and the use of resilient, immutable backups, are essential long before a breach occurs. Leaders should also run tabletop exercises that address both tactical ransomware response and operational payout scenarios. These exercises help validate policies, align stakeholders, and build the critical competencies required to respond effectively under pressure.
When ransomware attacks, there’s rarely time to pause and regroup. Executive teams need to be ready to make tough calls quickly and with limited visibility. Bridging technical readiness with business continuity can help security leaders turn a reactive scramble into a decisive, coordinated response.
With threats like Qilin on the rise, resilience isn’t a static plan. It’s a shared, practiced capability.
Is your endpoint protection ready for Qilin-level attacks? Explore how Qualys Endpoint Prevention, Detection, and Response (EDR & EPP) gives you the real-time visibility and response power to stop ransomware threats like Qilin!
Get Ahead of What’s Next
The tactics, tools, and targeting patterns of ransomware groups like Qilin are evolving faster than ever. Staying informed isn’t just about awareness, it’s about readiness. Whether you’re building out your incident response playbooks, prioritizing patch cycles, or aligning stakeholders through tabletop exercises, timely intelligence is the foundation of smart decisions.
Subscribe to the Qualys blog for trusted threat intelligence, vulnerability insights, and practical guidance you can act on!