“The art of communication is the language of leadership.” — James Humes, former Presidential speechwriter and author.
Cybersecurity teams face adversaries who thrive in chaos. Attackers move fast, automate, and strike where defenses are weakest. In a borderless digital world, disruption is constant, driven by innovation, complexity, and the pressure to move faster, often at the cost of safety.
To withstand that pressure, teams need leadership and effective, confident communication.
Industry studies, including the Verizon DBIR, consistently find that the majority of major incidents are worsened by poor communication and a lack of coordinated responses. The tactics of effective cybersecurity leadership rely on continuous improvement, clarity, structure, and agility. With the right priorities and proper coordination, leaders can build systems that support swift, unified action, even under relentless pressure. However, as we’ve seen throughout this series, success hinges on information, available resources, and clear mission priorities. Without structure, even the strongest plans can collapse under pressure.
A global shipping and logistics company experienced this firsthand during the NotPetya attack. Despite strong tools and sound practices, ransomware spread unchecked, crippling critical operations and paralyzing logistics networks around the world.
- Systems locked up across regions.
- Communication and coordination collapsed.
- Schedules, systems, and asset visibility gone.
- Shipments halted; global operations disrupted.
It took almost two weeks to recover to basic operating levels. (Recovery could have taken far longer if not for a fortunate offline backup of a key domain controller.)
The financial toll reached hundreds of millions, but the real exposure was strategic: the incident revealed just how fragile operations are without a structured link between technical action and business needs.
The most glaring lesson: technology and talent alone weren’t enough.
In the aftermath, the company began mapping and building foundational systems it had never fully established. Business Continuity and Disaster Recovery plans were rewritten. Asset inventories were created and validated. And for the first time, risk-based decision-making was integrated into every critical function. With surprising agility, teams shifted from simply reacting to executing with a streamlined, prioritized posture. Leadership gained real-time visibility into risks, assets, and threats, finally aligning technical insight with business impact.
Today, security and technical teams understand what disaster and success look like. They know which systems matter most. Leadership experienced far less friction when requesting metrics and communicating them to various decision-makers.
As we have covered throughout this series, technology alone will never be enough. Cybersecurity teams must build systems that ensure clear, confident communication, especially when everything is on the line.
An Orchestrated Response – Prioritized and Sharply Tuned
“All the squadrons in the world are of no use if they cannot be brought into action at the right moment, at the right spot, and in sufficient numbers.” – Air Chief Marshal Hugh Dowding
Victory in Cybersecurity isn’t determined by raw resources, but by how effectively they’re deployed. For leaders to be effective, threat awareness must drive and empower decisive action.
In Step 3, we introduced the British defensive pivot after the fall of France in the spring of 1940. Facing invasion, Britain’s survival would not simply depend on brute force but clarity of mission, methodical deployments, and a bit of innovation.
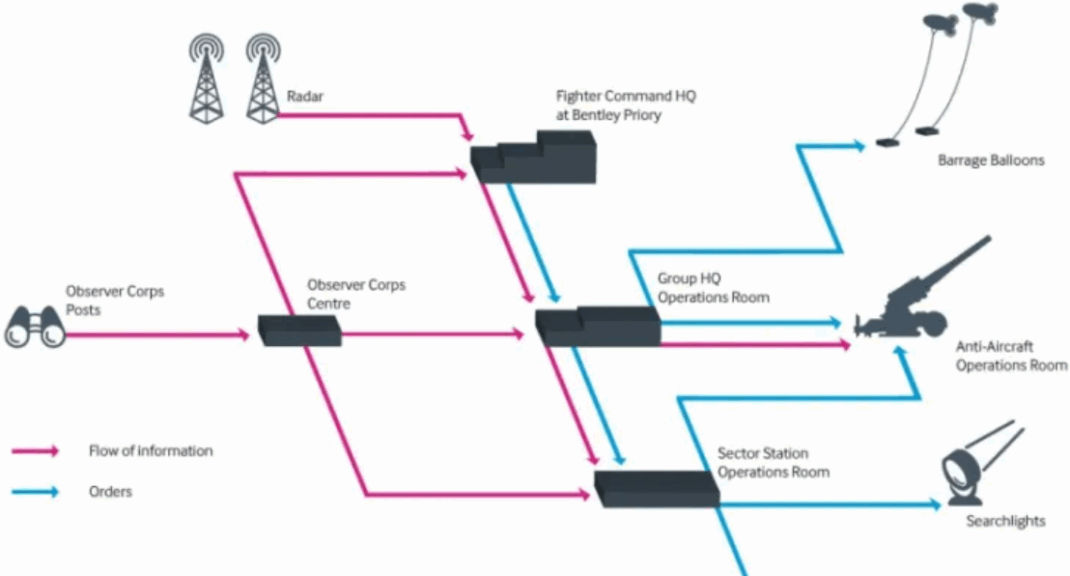
That summer, Germany poured effort and resources into securing radio transmissions for the next push. However, rather than simply focusing on intercepting enemy messages, Britain built a system to see attacks before they struck. For the first time in history, coastal radar towers were used to reflect signals and triangulate the position of incoming aircraft. This innovation enabled unparalleled early detection and gave defenders the critical seconds needed to respond rapidly.
Germany, meanwhile, concentrated on encrypting communications and bombing airfields, underestimating the value of Britain’s radar network. This early miscalculation allowed Britain to preserve its early warning capabilities, enabling faster, more effective responses to incoming raids.
This breakthrough, known as “Chain Home,” gave defenders the eyes and foresight they needed to act. Integrated into the Dowding System framework, it funneled intelligence to command centers, which coordinated real-time air defensive deployments.
The innovative Dowding System brought order to mountains of intelligence and data, enabling maximum impact of limited resources. Agile communication, clear roles, and rapid execution gave Britain an edge.
Despite standing alone and facing overwhelming odds, the system held; the attacks were repelled, and for the first time, the tide began to turn.
This wasn’t just technological ingenuity, but an innovative, repeatable system, for an agile and orchestrated response. It turned scattered inputs into decisive action and gave leadership the visibility to make well-informed calls at the speed of conflict. It also inspired other nations who witnessed the first defeat of a force thought to be unbeatable.
Every day brought new attacks, often without warning, targeting airfields, radar stations, cities, and supply lines. There was no pause, just the constant pressure to intercept, adapt, and survive.
Modern cybersecurity teams face a similar battle. The digital homeland is constantly under attack. Adversaries move fast, looking for every weakness, thriving on slow, disjointed responses. The Dowding System stitched together radar, ground observers, and command centers into a live operational picture. This enabled rapid identification, vectoring of fighter squadrons, and centralized decision-making under pressure. In the end, the right tools and talent mean little without a structure that translates information into swift, confident action.
Good news: Security teams don’t have to build their own Dowding and Chain Home systems from scratch.
A Template for Resilience – Leveraging NIST Frameworks
“All the great struggles of history, whether in war or peace, turn on effective organization, on bringing superior force to bear at the right time, and place.” — Winston Churchill
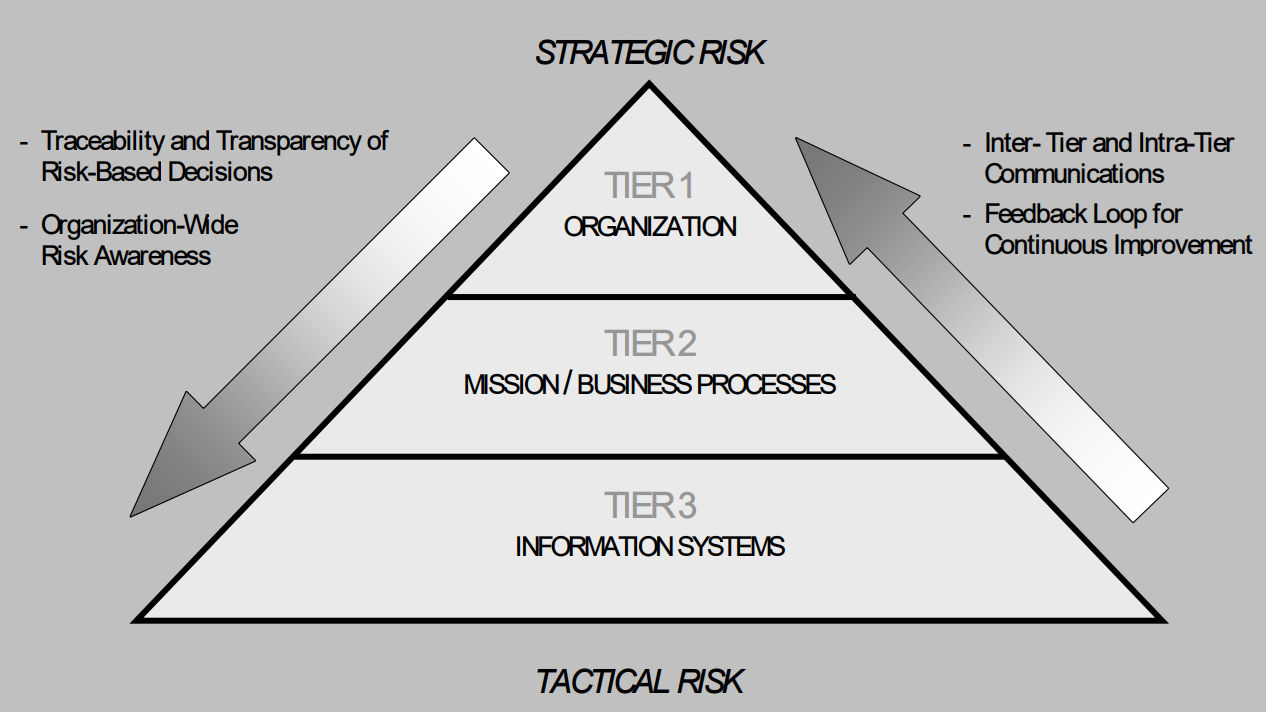
It bears repeating that there is no need for cybersecurity teams to build their risk-reduction strategies from the ground up. Established risk management frameworks (RMF) offer a proven playbook for maturing security posture and turning intelligence into prioritized action. These frameworks move organizations beyond reactive responses to scalable, repeatable risk reduction aligned with business goals. NIST’s strategic runbooks embed cybersecurity risk management into everyday business operations, ensuring risk is measured, communicated, and acted on across the organization.
We’ll focus on two essential frameworks that help teams integrate cybersecurity into business operations with clarity and confidence: 1) NIST 800-39 and 2) 800-37.
- NIST 800-39 RMF focuses on organization-wide risk management. It aligns cybersecurity with mission objectives, assigns clear ownership, and embeds risk directly into business decision-making. Leadership should start here to communicate accountability and drive a top-down, business-first approach to managing risk.
RMF Implementation – Simplified:
- Categorize: Identify the impact level of assets to prioritize security needs.
- Select & Implement Controls: Tailor and deploy security measures based on the identified risks.
- Assess & Monitor: Continuously assess and refine controls to keep up with emerging threats.
- NIST 800-37 revision 2 lays out the Risk Management Framework (RMF), a repeatable process for selecting, implementing, assessing, and continuously monitoring security controls.This is where teams measure effectiveness, eliminate blind spots, and keep defenses relevant through day-to-day execution.
Key principles from NIST 800-37 Rev. 2:
- Cybersecurity as a Business Function:
Risk is not isolated, and cybersecurity is integral to business objectives. Aligning risk management with business functions reduces the chance of overlooked threats and strengthens operational resilience. - Continuous Monitoring:
Risk management isn’t a one-and-done exercise. Ongoing assessment ensures defenses stay effective and responsive as the threat landscape shifts. - Preparation and Planning:
Effective risk management starts with a solid foundation. Proactive preparation ensures smoother RMF execution and faster response to real-world risks. - Lifecycle Approach to Security:
Risk management must span the entire system lifecycle, from design through deployment, to ensure systems are protected from the start.
By embedding security from the beginning and continuously reassessing controls, organizations align cybersecurity with broader business strategies, boosting resilience, reducing downtime, and ensuring that defenses adapt to risk.
Think of NIST 800-39 and 800-37, combined with the Enterprise TruRisk™ Platform, as today’s Dowding System. A unified command-and-control structure where intelligence flows freely, decisions are informed, and responses are swift. By applying these frameworks, cybersecurity leaders aren’t just protecting systems but embedding resilience into the DNA of the business. And with solutions like Qualys’ Enterprise TruRisk™ Platform, leaders have the tools to seamlessly integrate risk management, streamline operations, and continuously fortify defenses, ensuring their business stays ahead of the ever-evolving threat landscape.
Informed, Prioritized, Aligned – Enterprise TruRisk™ Management
Qualys Enterprise TruRisk ™ Management (ETM) unifies vulnerability, threat, and asset data, regardless of source, into a single, business-aligned view. It enables ownership assignment, enrichment, and deduplicated data, while connecting tooling to real financial impact. With native connectors and open integrations, organizations pull in data from across their ecosystem: Threat intel, third-party data, and CMDBs, in one shared platform. (See built-in connectors)
Teams gain cockpit-level visibility into risk, with search tokens, dynamic report tools, or automated continuous monitoring response rules, all from the same interface.
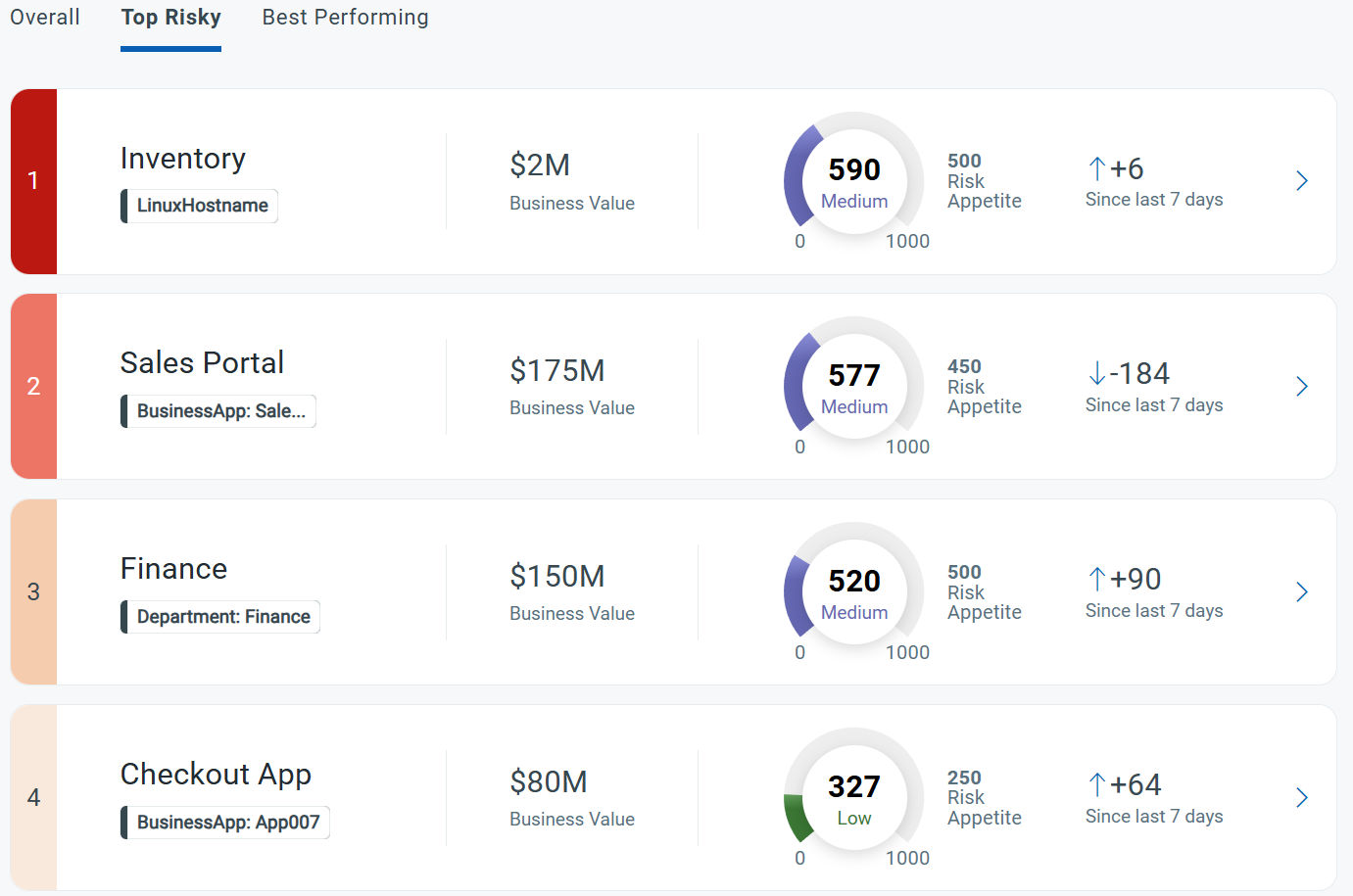
The business context drives every decision. ETM enables customized Business Entity creation, assignment of risk tolerance, and tracking exposure. That’s how you see where risk lives, how it trends, and where to act first based on what matters to the business.

See top risky groups, their value, and trends:
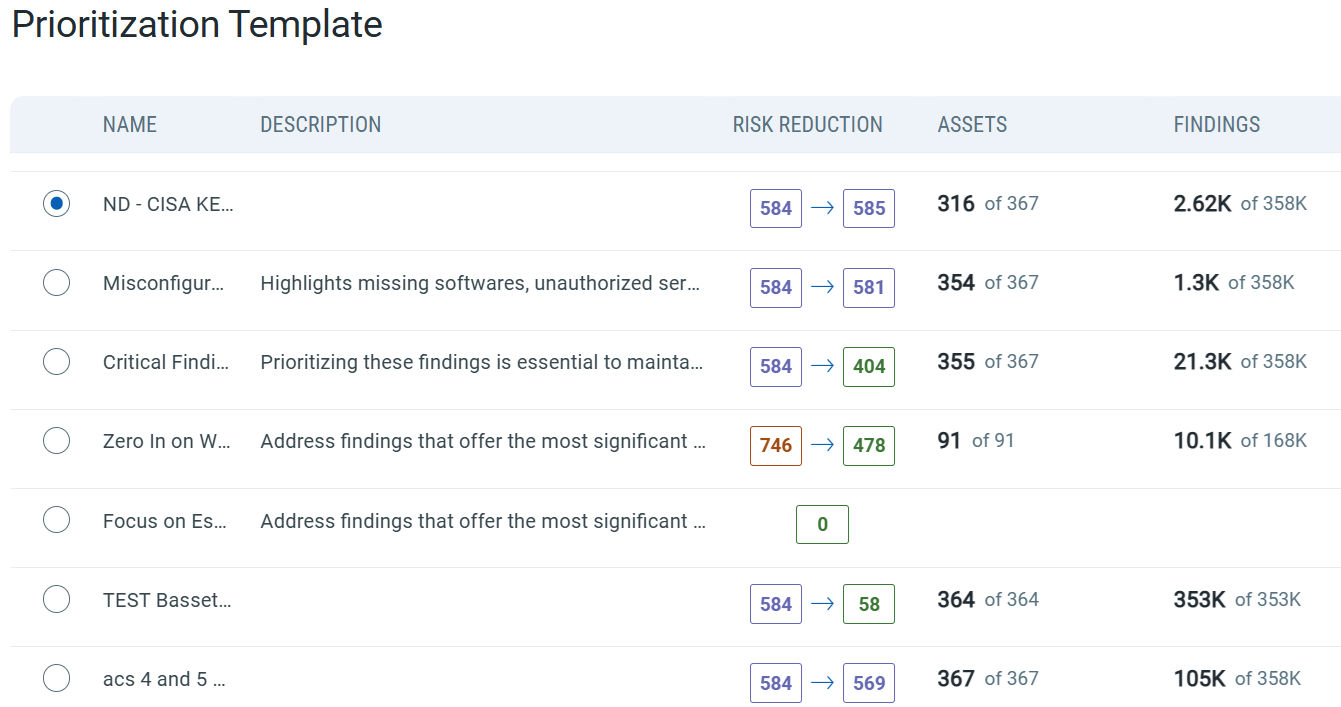
Customized Risk Reduction priority building:
With Qualys ETM, organizations operate from a single source of truth. Risk is measured, communicated, and acted on confidently across teams. With fewer clicks and fewer silos, a single agent delivers greater clarity, speed, and time, enabling more informed decisions that align cyber risk with business priorities.
From Measurement to Leadership: Communicating & Executing with Purpose
Steps 1 through 4 to TruRisk™ laid the groundwork: mapping assets, understanding threats, prioritizing what truly matters, and communicating risk. With this foundation, you’ve moved beyond the fog of digital war.
Step 5 is where leadership turns into action, strategy becomes execution, and risk is tackled, not just tracked. This is when teams shift from identifying to addressing risk. Step 5 is about executing with authority, marshaling the right resources, aligning teams, and closing gaps that matter most to your business.
Every step has led to this: It’s time to de-risk the business.
Stay tuned for the next and final chapter of this series!