Forget ransomware – most firms think quantum computing is the biggest security risk to come
Quantum computers will soon be able to break modern-day encryption When that happens, nation-states can…











Executive Summary ShadyPanda has exploited trusted browser extensions to compromise millions of users, illustrating how legitimate software can unexpectedly become harmful. Qualys TruRisk Eliminate empowers organizations to identify risky behaviors, prioritize real threats, and eliminate malicious components before attackers exploit them. How Browser Extensions Have Become a New Blind Spot Browser extensions are part of everyday…

Building custom foundation models requires coordinating multiple assets across the development lifecycle such as data assets, compute infrastructure, model architecture and frameworks, lineage, and production deployments. Data scientists create and refine training datasets, develop custom evaluators to assess model quality and safety, and iterate through fine-tuning configurations to optimize performance. As these workflows scale across…
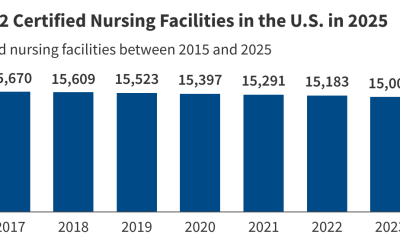
The 2025 reconciliation law could have major implications for nearly 15,000 federally certified nursing facilities and the more than 1.2 million people living in them. Nursing facilities provide medical and personal care services for older adults and people with disabilities. In 2023, Medicaid paid for 44% of long-term institutional care costs; 37% of long-term institutional care…

Philippa RoxbyHealth reporter Getty Images Young men are behind the growing popularity of nicotine pouches in Great Britain, a study suggests. Around 7.5% of 16 to 24-year-old-men are using the small sachets that fit under the top lip, compared with 1.9% use among young women and 1% among adults overall. Most pouch users – estimated…

Today, we’re expanding the Gemini 3 model family with the release of Gemini 3 Flash, which offers frontier intelligence built for speed at a fraction of the cost. With this release, we’re making Gemini 3’s next-generation intelligence accessible to everyone across Google products. Last month, we kicked off Gemini 3 with Gemini 3 Pro and…

Nick Triggle,Health correspondent, Jim Reed,Health reporterand Philippa Roxby,Health reporter Getty Images Prime Minister Keir Starmer has said the latest five-day strike by doctors in England is “dangerous and utterly irresponsible” and warned them not to abandon patients. The walkout by resident doctors, the new name for junior doctors, began at 07:00 on Wednesday. The British…

Getty Images Ruth CleggHealth and wellbeing reporter More babies are being born by caesarean section in England than delivered naturally – without assistance – for the first time. Latest NHS data for 2024-25 shows that 45% of births were by C-section, compared to 44% which were spontaneous, a term used to describe a natural vaginal…

Research by: Sven Rath (@eversinc33), Jaromír Hořejší (@JaromirHorejsi) Key Points The YouTube Ghost Network is a malware distribution network that uses compromised accounts to promote malicious videos and spread malware, such as infostealers. One of the observed campaigns uses a new, heavily obfuscated loader malware written in Node.js, which we call GachiLoader. To make it easier to analyze obfuscated Node.js malware,…

Staying ahead of what’s exposed, automatically. The modern enterprise doesn’t stand still. New domains are registered, acquisitions bring inherited infrastructure, cloud workloads spin up and down daily, and somewhere in the middle of it all, your visible footprint on the internet external attack surface keeps expanding. For CISOs, this constant motion makes one CTEM step…

Fouch knew automated sensors could help by, for example, identifying the environmental culprits of the hole-punching issues, but with so many potential options to try he didn’t know where to start. “The worst thing you can do, in a smaller business especially, is muddle through pilot purgatory, hoping to find a viable product,” he says….