Rapid7’s Q2 incident response (IR) data illustrates a solidification of trends first observed in Q1. There are no sweeping changes to commonly observed malware, or noticeably different software being deployed by threat actors in Q2. If you were expecting Bunny Loader to lose its impressive prominence, or perhaps initial access gained through compromised valid accounts to decrease significantly, you’d be mistaken.
Looking at it another way: this level of consistency and predictability from threat actors can be used to a defender’s advantage. For example, SOC teams should already have detections in place for Bunny Loader, and controls should also be established to block employees from mistakenly downloading trojanized versions of popular tools. Additionally, organizations can prioritize the implementation of robust multi-factor authentication (MFA) solutions, and educate employees as to why MFA is crucial to keeping the network secure.
Many or all of the threat actor tactics we’re observing are likely to be seen in play until at least Q4, so there’s no time like the present to turn the tables on would-be attackers.
Initial access vectors
Valid accounts / no MFA reigns supreme (again)
Valid accounts / no MFA as an initial access vector (IAV) are, once again, top of Rapid7’s investigated incident responses for Q2 2025, despite a drop from 56% to 43%. The percentage of observed brute-force attacks also dropped, down from 13% in Q1 to 7% in Q2. Given that our IR team noted an uptick in both MFA and brute-force attacks in Q1, these changes may not be out of the ordinary.
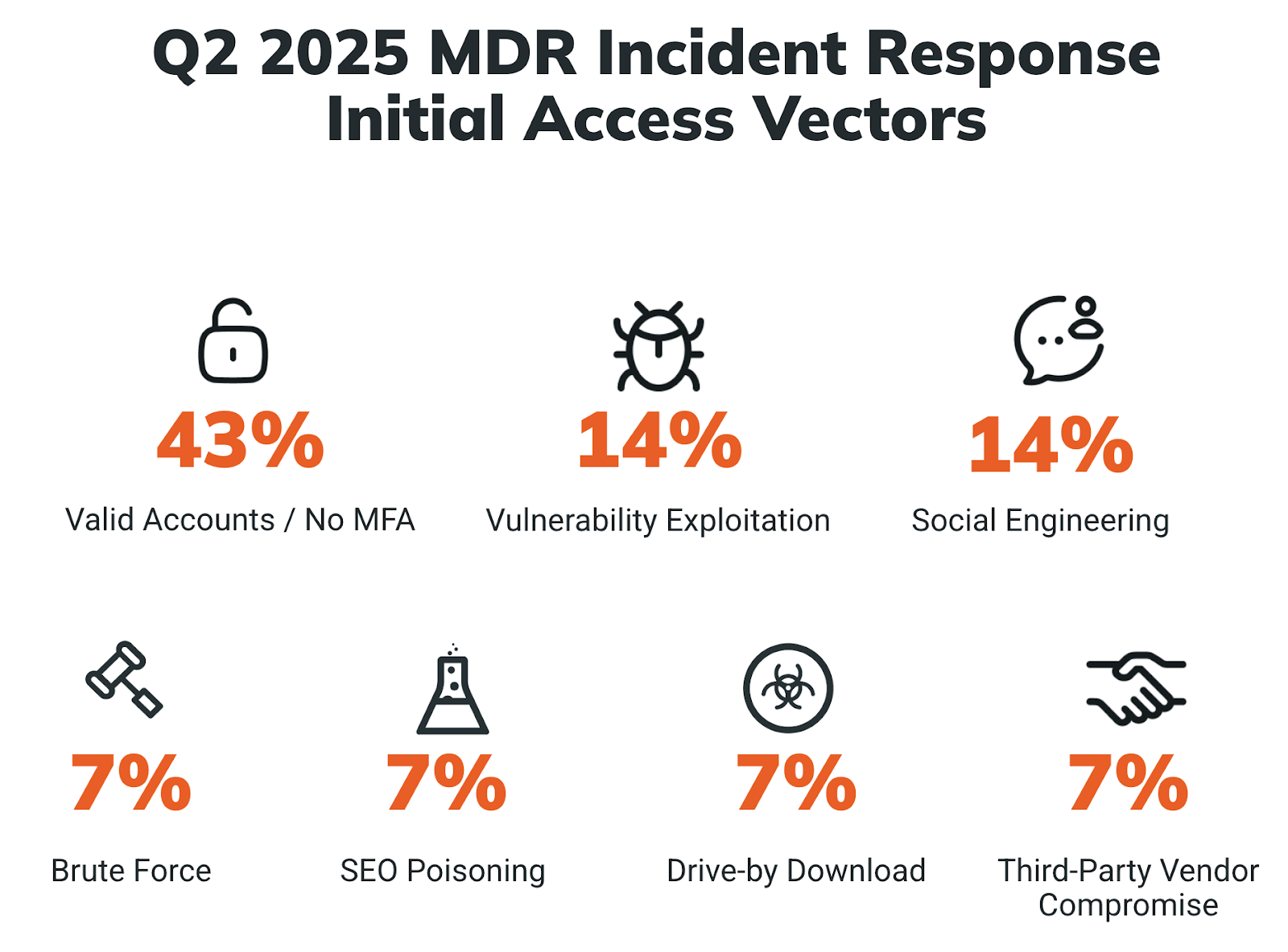
⠀⠀
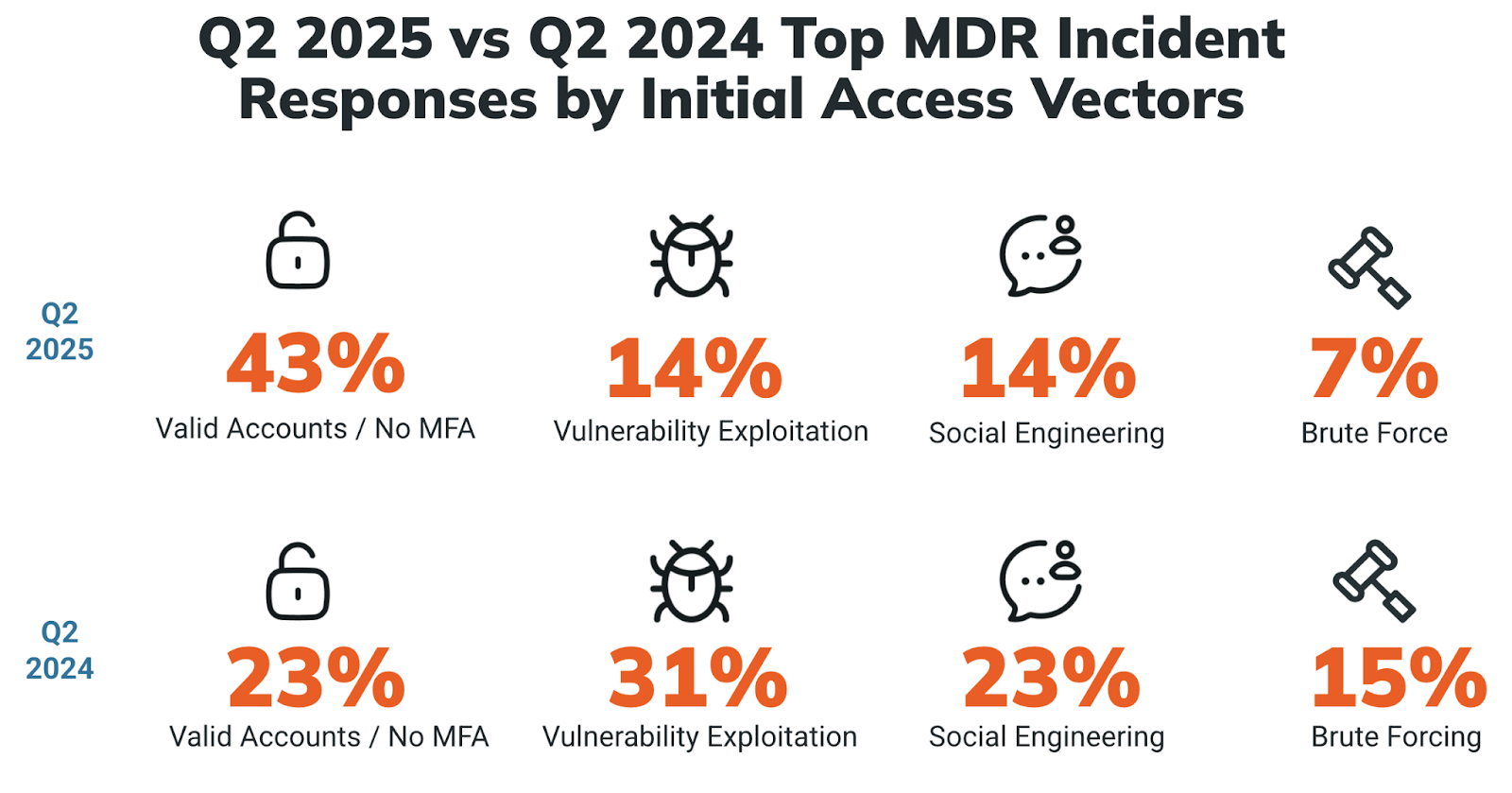
Below, we compare Q2 2025 and Q2 2024. There’s a big step-up for valid accounts / no MFA, and a 17% drop for vulnerability exploitation. Social engineering is also down compared to Q2 2024, but it remains a top access vector. And while 15% would place brute force in the upper realms in 2024, it’s one of several access vectors trailing the top three in Q2 of this year.
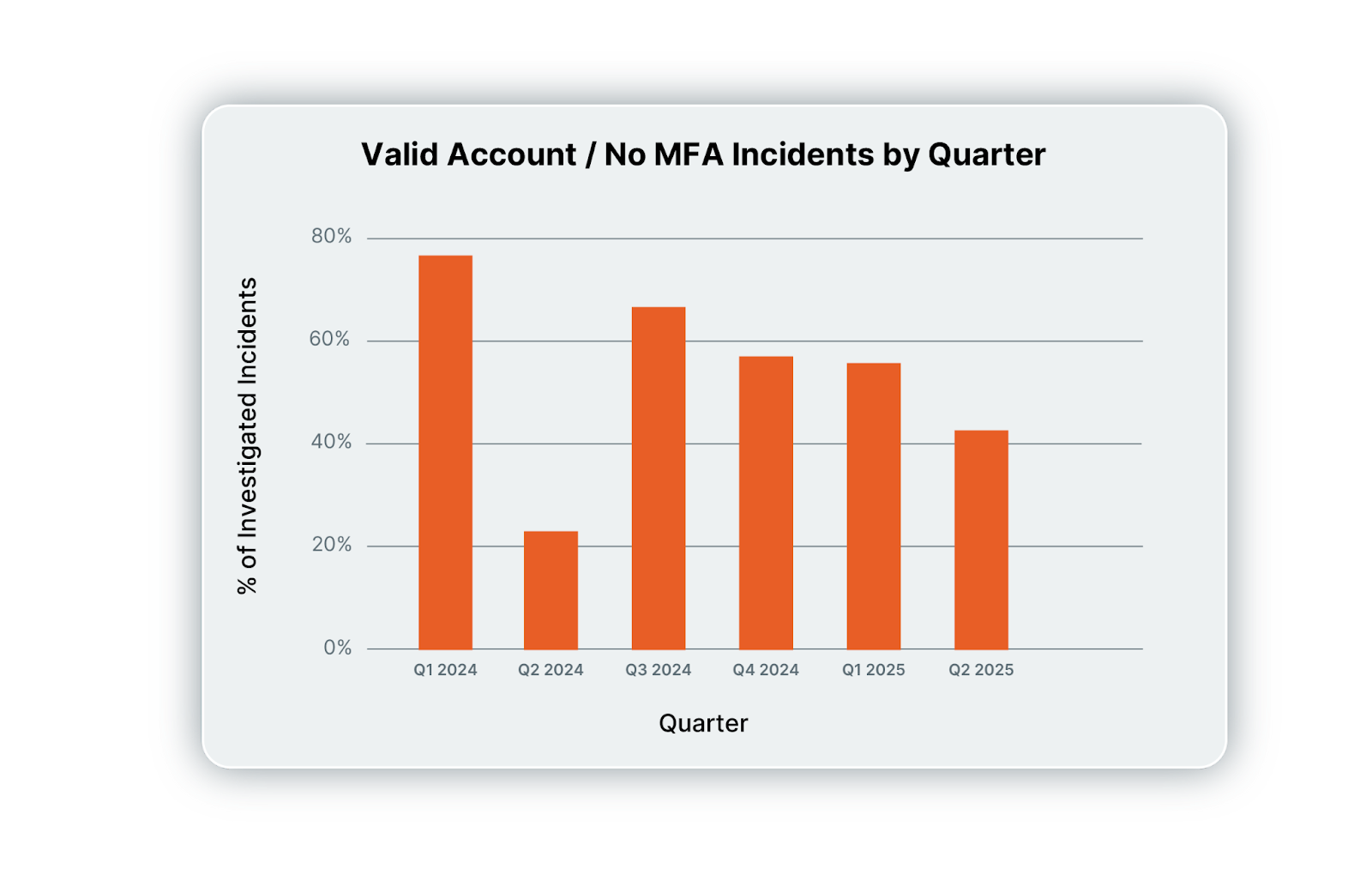
Here’s what our increasingly permanent fixture of a valid accounts / no MFA graph shows across the last six quarters of investigated incidents:
IAVs from Q2 include low-cost VPN authentication without MFA leveraging credentials via phishing, organizations with no MFA in place at all, and a crossover into social engineering techniques via MFA fatigue attacks.
Vulnerability exploitation
Rapid7’s IR services team observed multiple vulnerabilities used, or likely to have been used, as an IAV in Q2 2025. This includes exploitation, or attempted exploitation, of Microsoft SharePoint Server (CVE-2023–29357, CVE-2023-24955), CentreStack (CVE-2025-30406), Palo Alto PAN-OS (CVE-2024-9474, CVE-2024-0012), and SonicWall’s SonicOS (CVE-2024-53704). We’ll look at these in more detail in the relevant individual industry sections below.
Social engineering
Threat actors focused on weaponizing employees against their own interests made up 14% of all incident responses. Popular Q2 tactics included Microsoft Teams chats involving the impersonation of employees, directing employees to renamed / trojanized remote monitoring and management (RMM) tools, or wearing targets down with MFA fatigue attacks.
Attacker behavior observations by industry
The top five industries most observed in incidents during Q2 were Services (21.2%), Manufacturing (16.8%), Retail (14.1%), Healthcare (10.3%), and Communications and Media (10%). This top 5 match those of Q1, albeit their order has changed. Most notably, Services and Manufacturing have exchanged first and second place, and Retail has moved from fifth place to third.
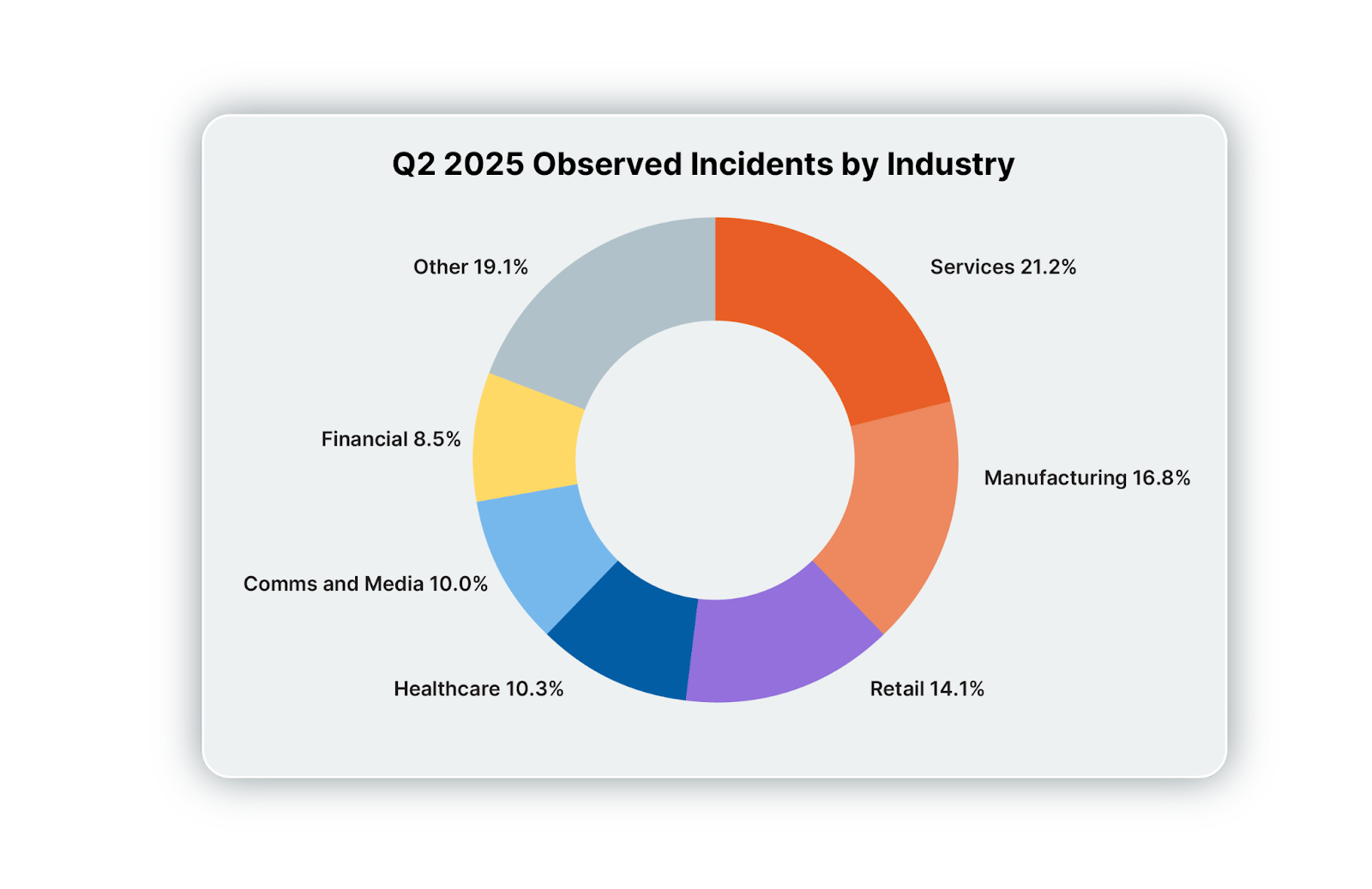
Q1 2025 played host to a Bunny Loader overload, taking top spot across every industry bar one for total number of observed incidents. Q2 continues this trend, with the MaaS tool significantly ahead of the pack across the top 5, while sharing top spot with the likes of Tangerine Turkey and Lumma Stealer in industries such as Utilities & Energy and Real Estate.
Services industry
Bunny Loader dominates the pack where services are concerned (58%), with other notables such as Lumma Stealer and SocGholish sharing the limelight.
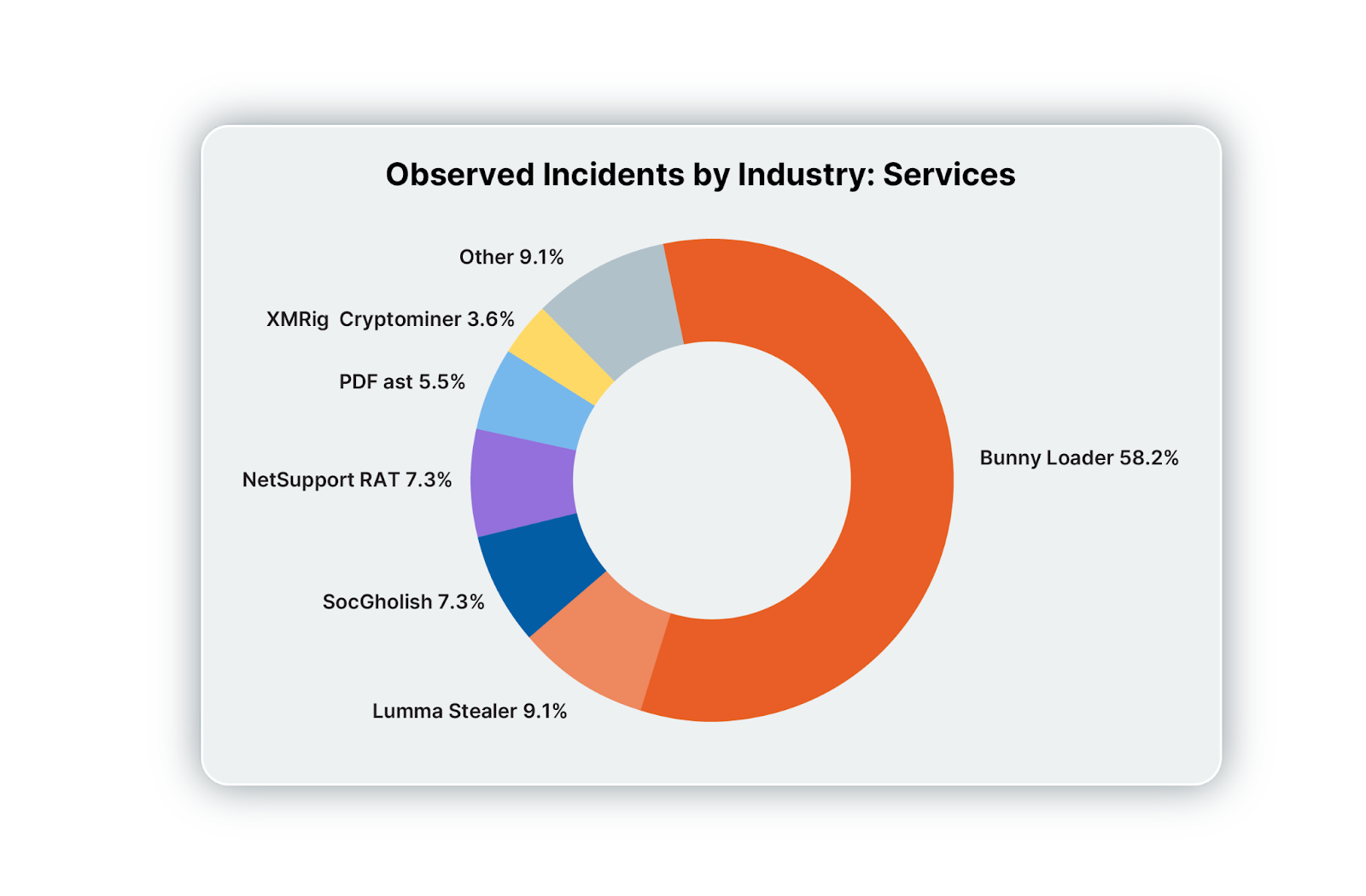
Tactics observed include malicious websites offering fake CAPTCHAs, SEO poisoning, drive-by downloads, and malvertising. Social engineering was also a popular choice for attackers targeting services, most commonly following one of the below patterns:
-
IT Support Scan -> Quick Assist
-
Microsoft Teams Chat -> Quick Assist
-
Download and execution of renamed ScreenConnect installer
In one business services incident we observed, a threat actor successfully impersonated an employee to social engineer the help desk. The attacker passed all security Personally Identifiable Information (PII) checks to successfully reset both MFA device and password. This targeted social engineering attack reveals the need to review help desk checks to ensure there are non-PII checks in the review chain, such as manager approval for elevated accounts.
Rapid7 IR teams also observed several examples of vulnerability exploitation involving the following CVEs:
- CVE-2023–29357 – Microsoft SharePoint Server Elevation of Privilege Vulnerability
- CVE-2023-24955 – Microsoft SharePoint Server Remote Code Execution Vulnerability
These two vulnerabilities comprise an exploit chain that allows a remote unauthenticated attacker to achieve remote code execution against a vulnerable Microsoft SharePoint server. CVE-2023-29357 is an authentication bypass vulnerability, due to how SharePoint may skip signature validation if an attacker-controlled JSON web token does not specify a signing algorithm.
By leveraging the authentication bypass vulnerability, an attacker can then trigger CVE-2023-24955. This allows for arbitrary attacker controlled .NET code to be executed via a code injection issue. The result of this chain is unauthenticated remote code execution.
This CVE is an improper authentication vulnerability affecting the SSLVPN authentication mechanism of SonicWall’s SonicOS. The vulnerability allows for a remote unauthenticated attacker to successfully leak out the session cookie of an existing legitimate user’s SSL VPN session. Upon leaking the session cookie, an attacker can reuse the cookies to hijack the legitimate SSL VPN connection. This allows an attacker to successfully establish a VPN connection into the target network.
Manufacturing
As with so many other industries in Q2, Bunny Loader and Lumma Stealer are out in front, although the distance between Bunny and Lumma is significant.
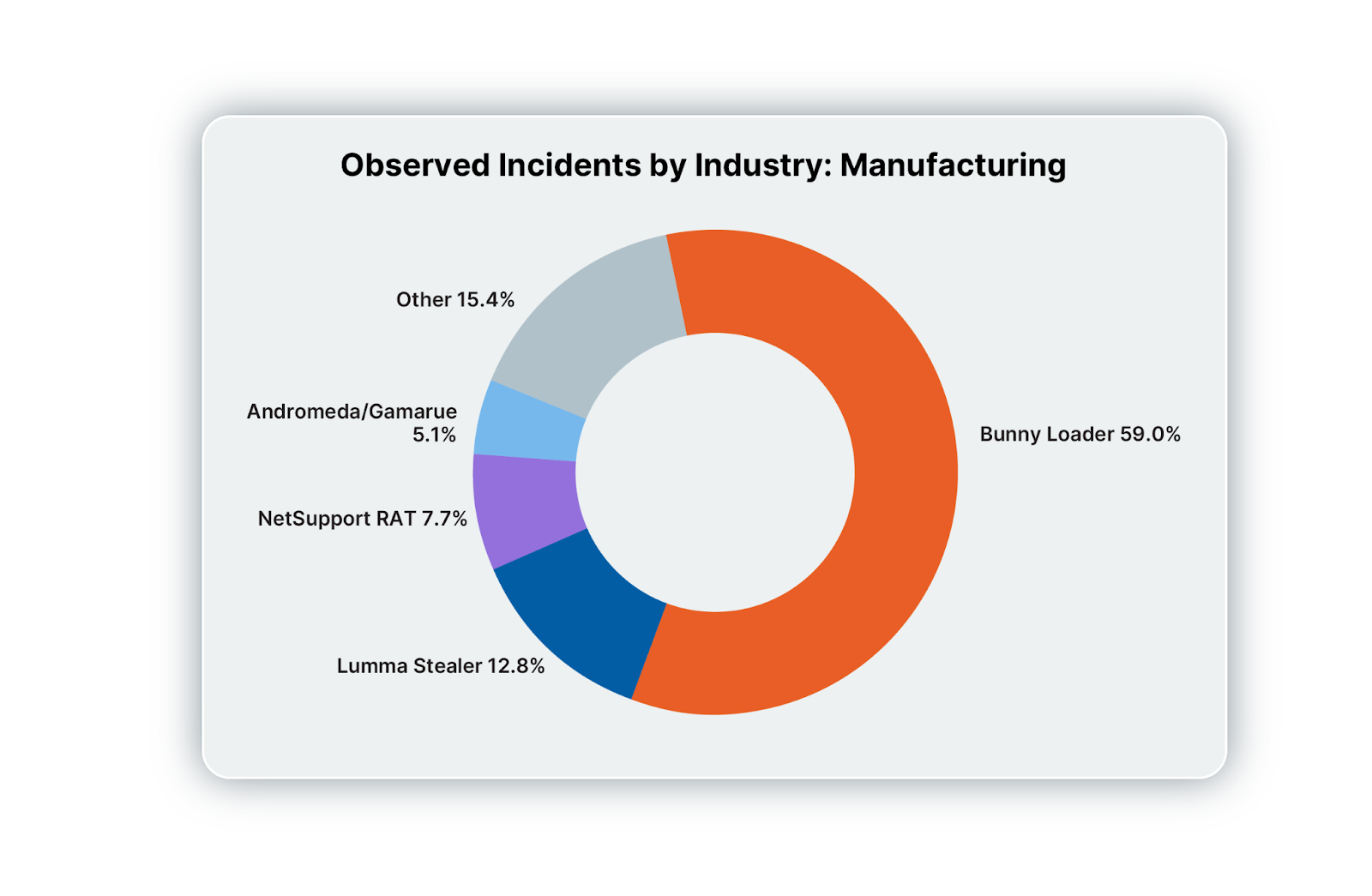
Here and elsewhere, fake CAPTCHAs, drive-by downloads, phishing, and infected USB drives are in play. Where social engineering is concerned, suspicious Microsoft Teams chat requests are popular. So too is the installation of renamed RMM tools, such as ScreenConnect and Quick Assist.
In one manufacturing incident we observed, initial access was gained via a VPN with no MFA protection. The threat actor quickly collected data, including asset information and passwords into CSV files, as well as created new accounts and added them to the Domain Admin security group. This ended with installation of RMM tools, and a sizable amount of data exfiltration. The launchpad for all of this was most likely a basic phishing attack, something which would have been much more difficult to achieve if MFA controls had been in place. Also of note was the use of a .sys file to disrupt security tooling on the system — a tactic in which we saw a bit of a usage uptick in Q2.
Vulnerability exploitation observed in manufacturing includes:
These two vulnerabilities comprise an exploit chain that was exploited in the wild. CVE-2024-0012 is an authentication bypass that allows a remote unauthenticated attacker to circumvent authentication and reach an endpoint that will create a new user session. CVE-2024-9474 is a command injection vulnerability in how session objects are processed. An attacker can poison a new session object via CVE-2024-9474 and insert an arbitrary operating system command to be executed. Chaining these two vulnerabilities together achieves unauthenticated RCE with root privileges.
CentreStack is a file sharing platform aimed at managed services providers (MSPs). Prior to the patch for CVE-2025-30406, a CentreStack server would use a hardcoded cryptographic key to encrypt serialized .NET objects that were sent and received to clients interacting with the server, a common feature of how ASP.NET web applications work. Because the key was hardcoded, and thus known to an attacker, a remote unauthenticated attacker could correctly encrypt a malicious .NET deserialization payload and transmit it to the server, achieving authenticated remote code execution.
Retail
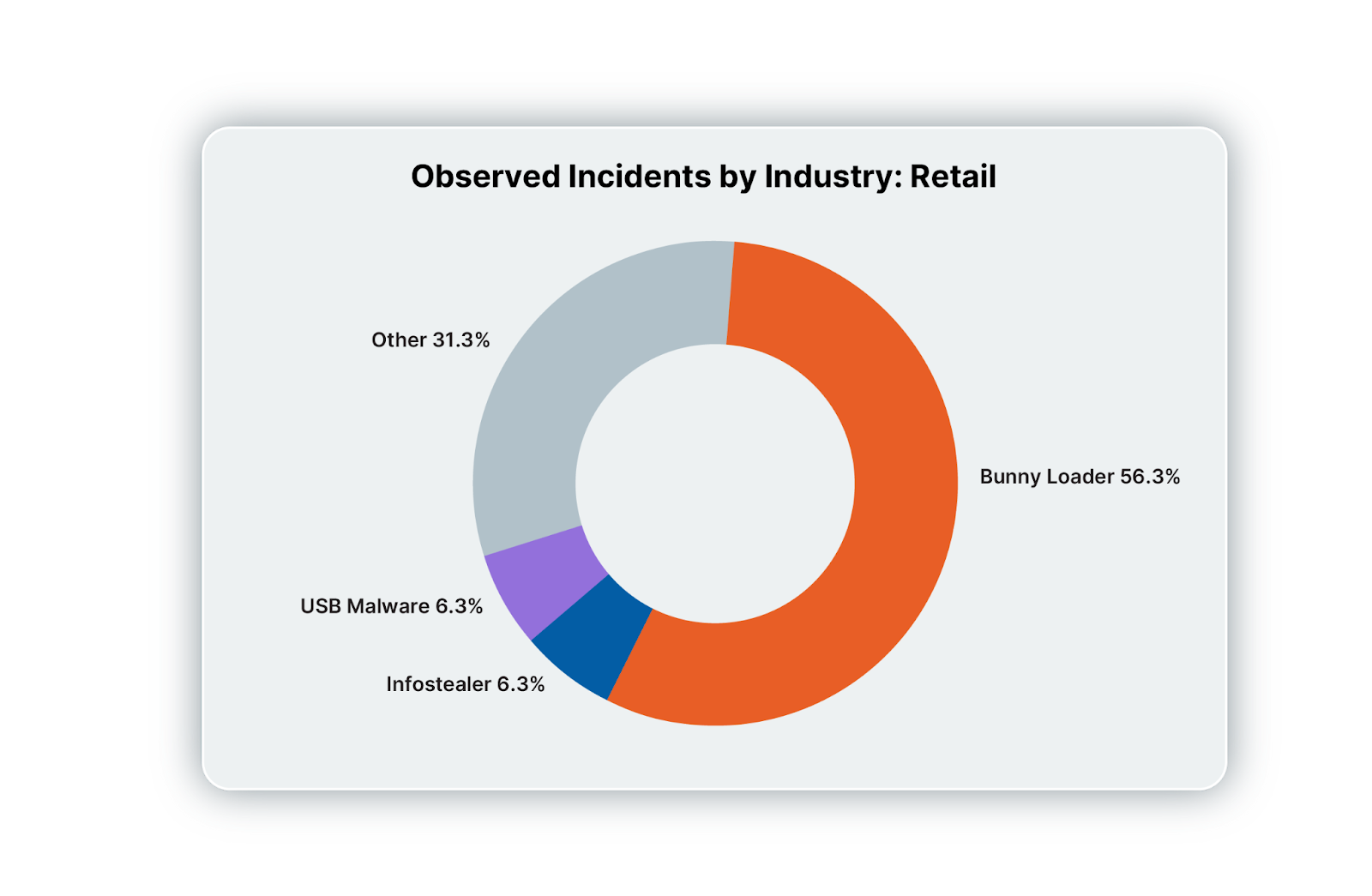
Retail follows a similar pattern to the services industry, filled with a mixture of fake CAPTCHAs, phishing, and drive-by downloads. Infected USB drives also make an appearance, while social engineering incidents include the download and installation of RMM tools, such as ScreenConnect and Quick Assist.
One retail investigation we observed mirrored an incident from Q1: poisoned search results leading to a trojanized version of RVTools. The software contained the previously mentioned Bumblebee, loading malicious code and ultimately communicating with Command & Control (C2) servers to execute further commands and payloads. Eventually, local accounts were created and a legitimate digital forensic tool was used to collect and exfiltrate credential information.
Rapid7 also observed CVE-2025-31324 — SAP NetWeaver Unrestricted Upload of File — used in a retail attack. This vulnerability was disclosed by SAP as a zero day that was exploited in the wild. SAP NetWeaver is a software stack that many other SAP products are built upon. The affected component within NetWeaver was the Visual Composer, which is not installed by default but is a commonly deployed component. The vulnerability allows a remote unauthenticated attacker to upload a malicious file, such as a web shell, and subsequently achieve remote code execution on the target system.
Healthcare
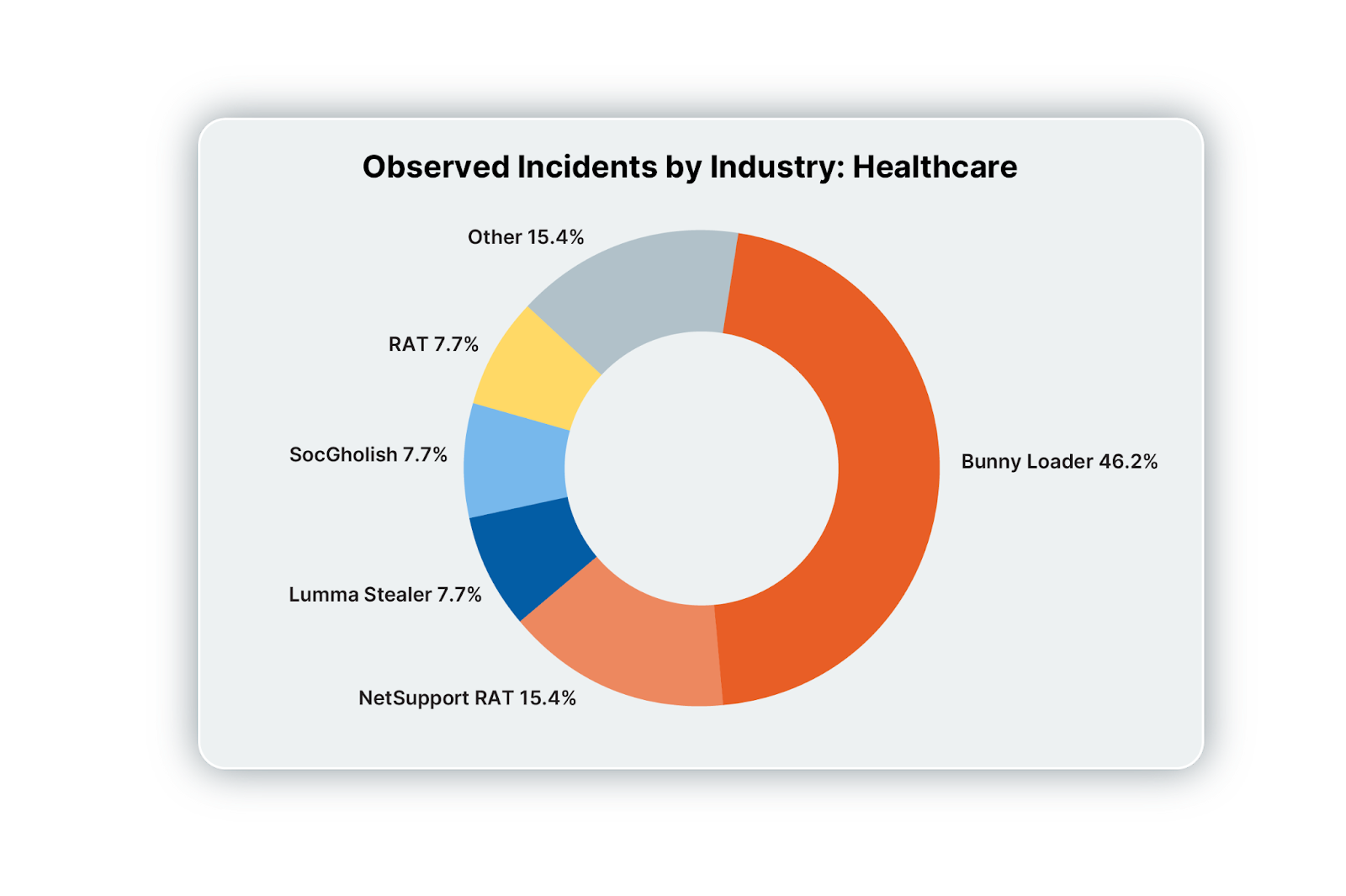
Malicious domains / CAPTCHAs, and phishing were popular threats in the healthcare realm in Q2. Account compromise / business email compromise (BEC) was also observed. This involved suspicious inbox rule creation, and the use of software intended for backups used as a method for exfiltrating data.
Communications and media
Bunny Loader, inevitably, is at number one spot for Comms and Media (35% of observed incidents), with SocGholish in second place (10%). CAPTCHAs, phishing, drive-by downloads, and fake browser updates make up the rest of the notable tactics on display.
Trojanized software is popular here, perhaps reflecting the specific digital needs of an industry requiring a multitude of design tools and ways to transfer large files easily. Among those observed were trojanized versions of Adobe Creative Cloud Software, ScreenConnect, and RVTools. Regular readers will know we highlighted how easily bogus versions of RVTools appear in sponsored search results in our Q1 report.
Searches for Adobe Creative Cloud and ScreenConnect in various search engines right now result in multiple downloads, from both sponsored ads and third-party websites. It’s often difficult to navigate the wealth of paid ads, bannered offers, and regular websites and figure out which ones are genuine so it’s no surprise to see a well-worn tactic still in play.
Conclusion
Q2 2025 takes many of the trends and tactics from Q1, and sees them continuing to thrive in the workplace. Bunny Loader is still very much in the running for being the most common malicious file observed by the Rapid7 Incident Response team across 2025 if it keeps up this kind of pace, standing head and shoulders above the competition. Valid accounts with no MFA protection are not going away anytime soon, and the threat posed by social engineering — largely involving exploiting help desk support, as well as a range of attacks using Microsoft Teams as a launchpad — is always a cause for concern.
There is no better time than now to take advantage of threat actor predictability, paying particular attention to training and education on CAPTCHAs and social engineering attacks focused on help desk workers. It’s also not too late to develop a fleshed-out MFA plan for your business and play a part in helping to shrink our valid accounts / no MFA chart even further.