
Green claims: confusion surrounds the EU’s anti-greenwashing directive
Translated by Nicola Mira Published July 1, 2025 The EU’s ‘Green Claim’ directive is designed…











Will Smale Business reporter, BBC News Cain Californian winery Cain makes a red wine that is a blend of two consecutive years In the world of wine vintage is king. If you are buying a bottle of red, white or rosé then the specific year of the grape harvest is almost always written on the…

What happens when a legacy application quietly slips under the radar and ends up at the center of a security incident involving AI and APIs? For one global organization, this scenario played out in real time when an unusual chatbot behavior sparked a closer look into their recruitment platform, revealing a set of compounding risks….
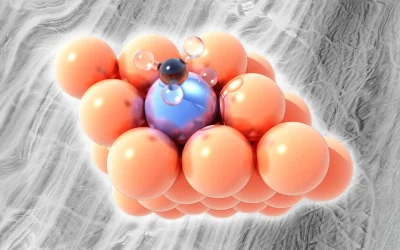
Indole, a molecule made up of a six-membered benzene ring fused to a five-membered ring containing nitrogen, forms the core structure of many biologically active compounds. Derivatives of indole, where hydrogen atoms are replaced by various chemical groups, are naturally produced by plants, fungi, and even the human body. Due to their properties, indoles have…

There are a number of reasons why this summer has been so warm. High pressure has regularly been overhead, meaning long spells of dry, calm, sunny weather. The dry ground has also helped temperatures to climb. Less of the Sun’s energy has been used in evaporating moisture leaving more to heat the ground and the…

For the first time, a research team at the University of Minnesota Twin Cities demonstrated a groundbreaking process that combines 3D printing, stem cell biology, and lab-grown tissues for spinal cord injury recovery. The study was recently published in Advanced Healthcare Materials, a peer-reviewed scientific journal. According to the National Spinal Cord Injury Statistical Center,…
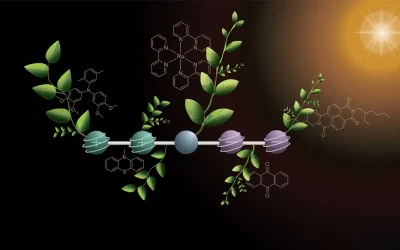
A research team from the University of Basel, Switzerland, has developed a new molecule modeled on plant photosynthesis: under the influence of light, it stores two positive and two negative charges at the same time. The aim is to convert sunlight into carbon-neutral fuels. Plants use the energy of sunlight to convert CO2 into energy-rich…

Enrollment in Medicare Advantage has grown rapidly in recent years, with more than half of all eligible Medicare beneficiaries now receiving their coverage from a private plan. Although the pace of enrollment increases slowed in 2025, the total number of Medicare Advantage enrollees still increased and the share of Medicare beneficiaries who obtain their Medicare…
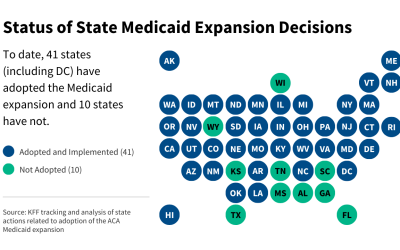
The Affordable Care Act’s (ACA) Medicaid expansion expanded Medicaid coverage to nearly all adults with incomes up to 138% of the Federal Poverty Level ($21,597 for an individual in 2025) and provided states with an enhanced federal matching rate (FMAP) for their expansion populations. To date, 41 states (including DC) have adopted the Medicaid expansion and…

The first human case of a flesh-eating parasite infestation has been confirmed in the US, authorities say. New World screwworm (NWS) myiasis was found in a patient who returned to the US from El Salvador, the Department of Health and Human Services said on Monday. The case was confirmed on 4 August. NWS myiasis is…

Key findings: Check Point Research has been monitoring a sophisticated social-engineering campaign targeting supply chain–critical manufacturing companies, where attackers leverage legitimate-looking business interactions to stealthily deliver a custom malware implant. The attacker initiates the communication via targeted company’s public “Contact Us” form, making the overture appear legitimate. The typical phishing flow is reversed as the…